CREDENTIALS and PROJECT_ID.
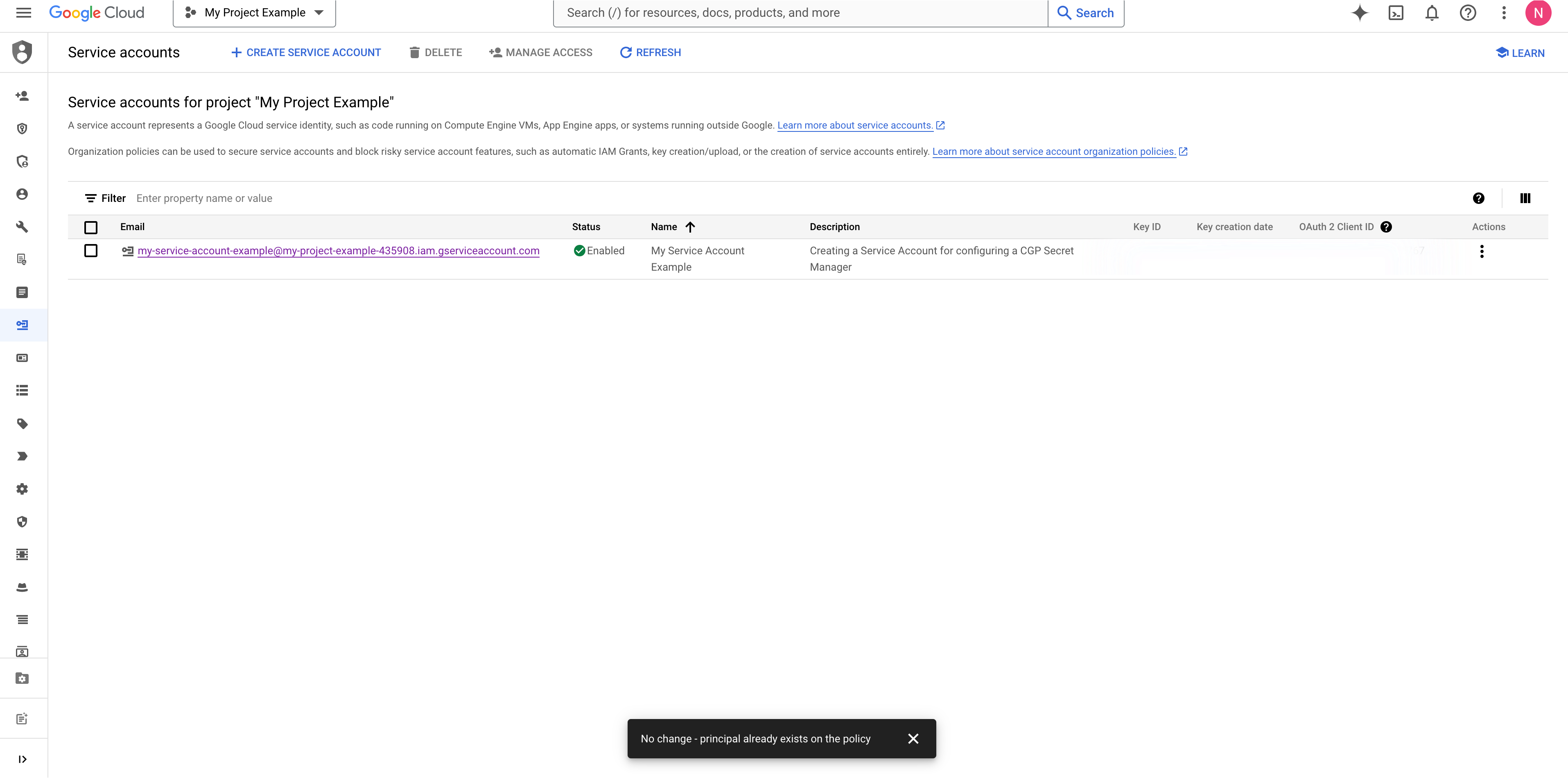
Create a GCP IAM Service Account
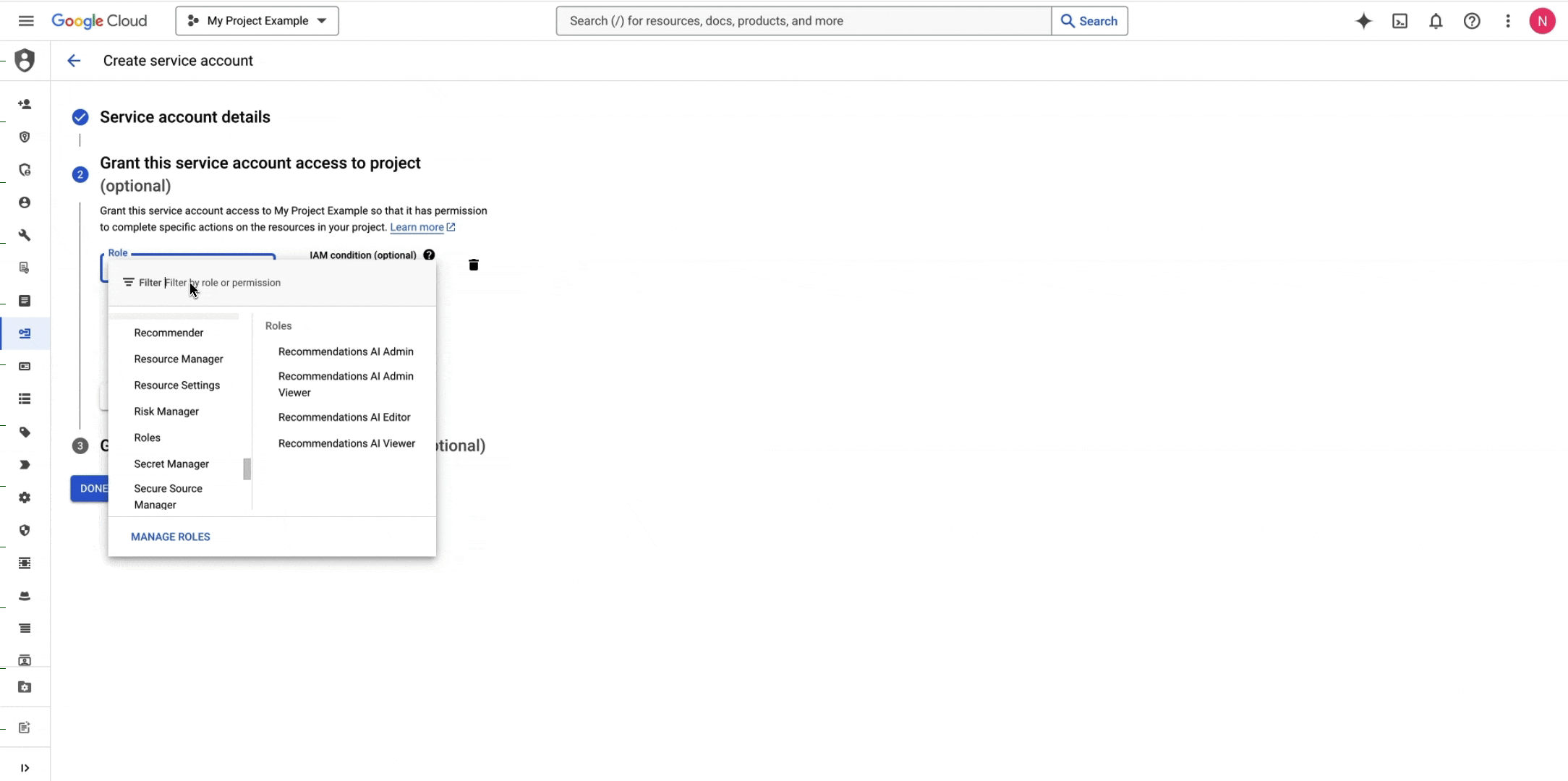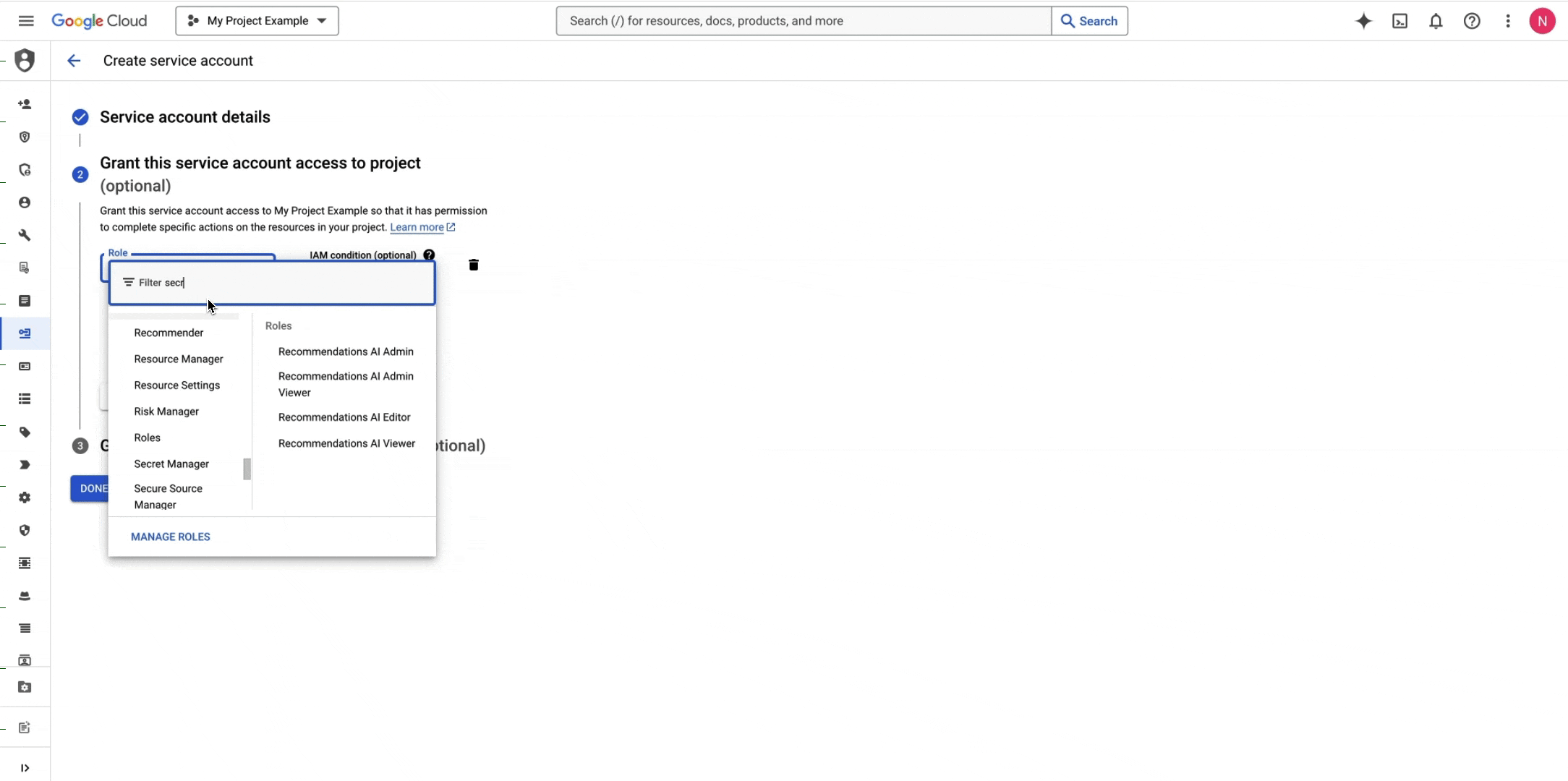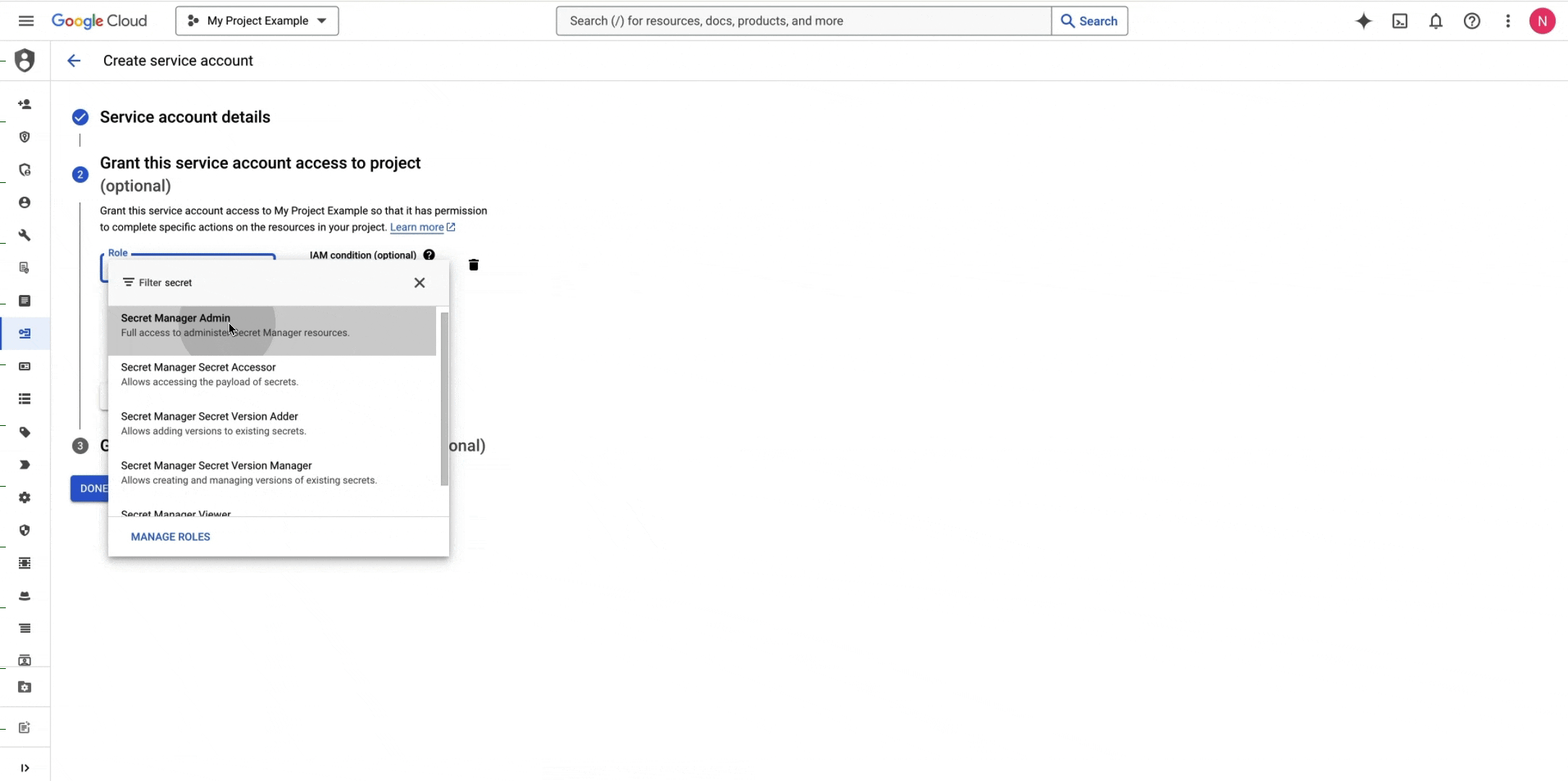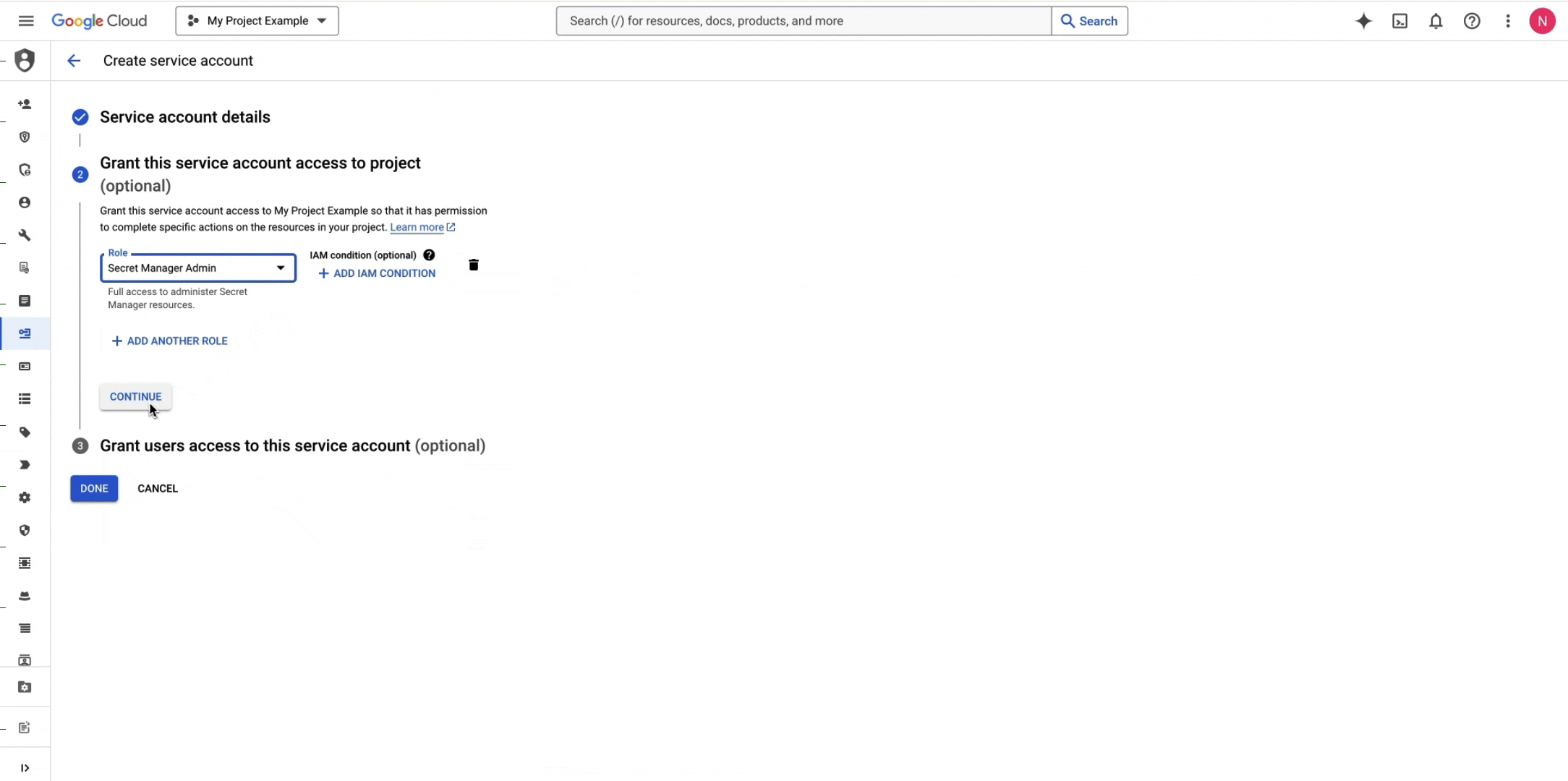
Create a GCP IAM Service Account or navigate to your GCP IAM Service Account if you already have one.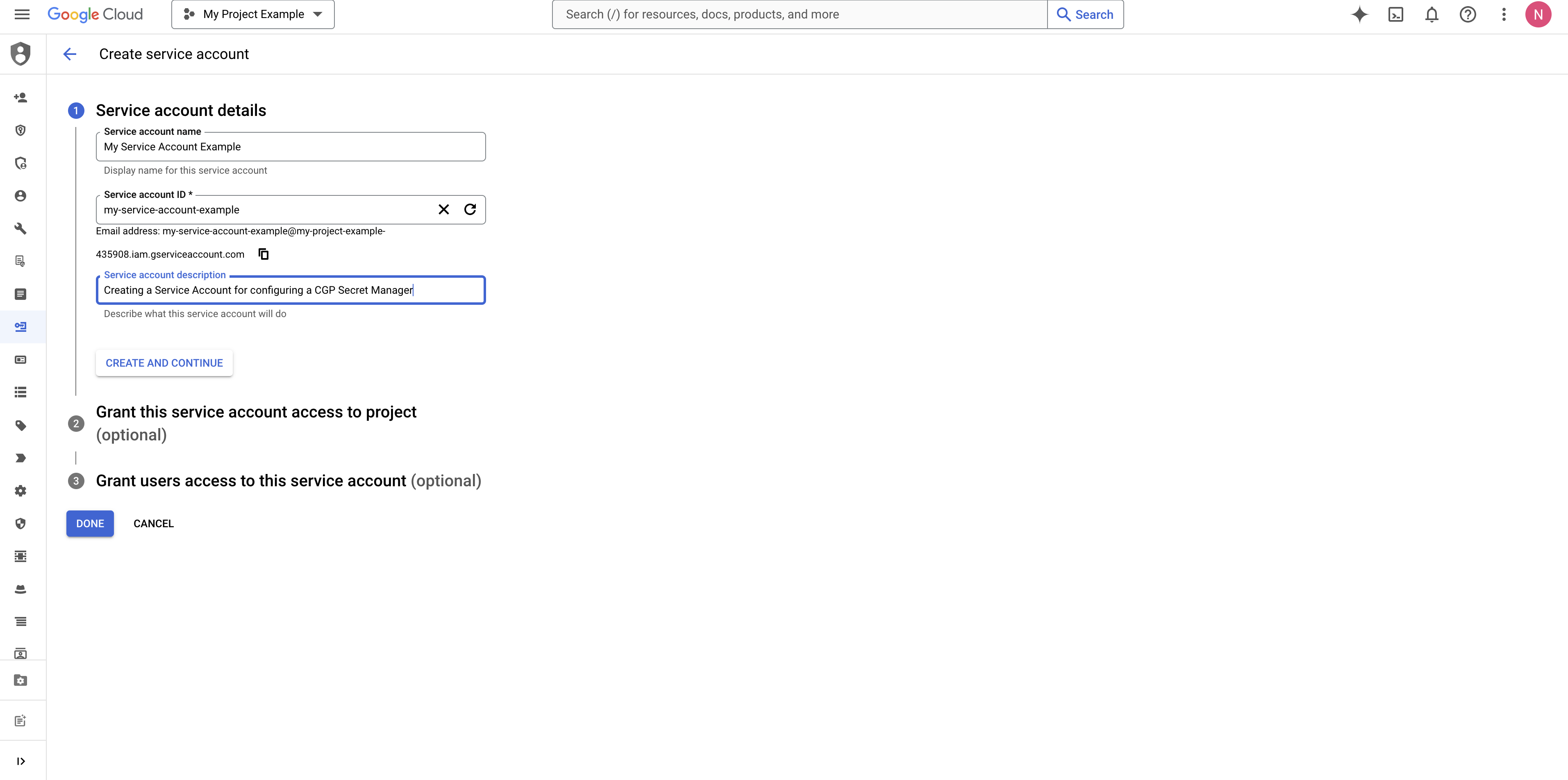

Create a New Runner in the Blink Platform
Proceed to the Blink Platform and create a new Runner in your Workspace.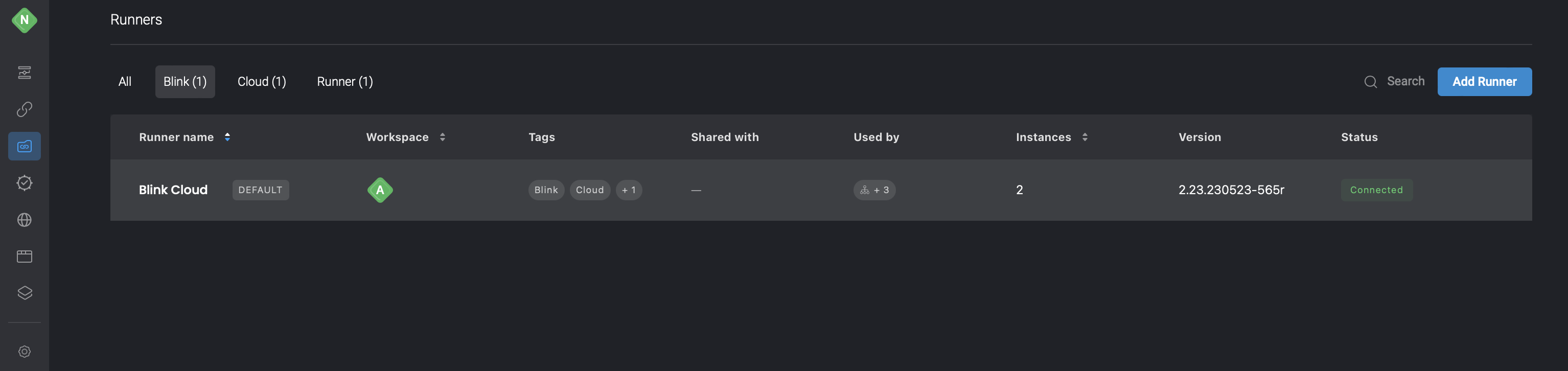

Set the Runner Group as Default (Optional)
Set new runner group as default for workspace. On the Runners page, click > Set as default.
OR Select the checkbox Set as default in Add new runner group.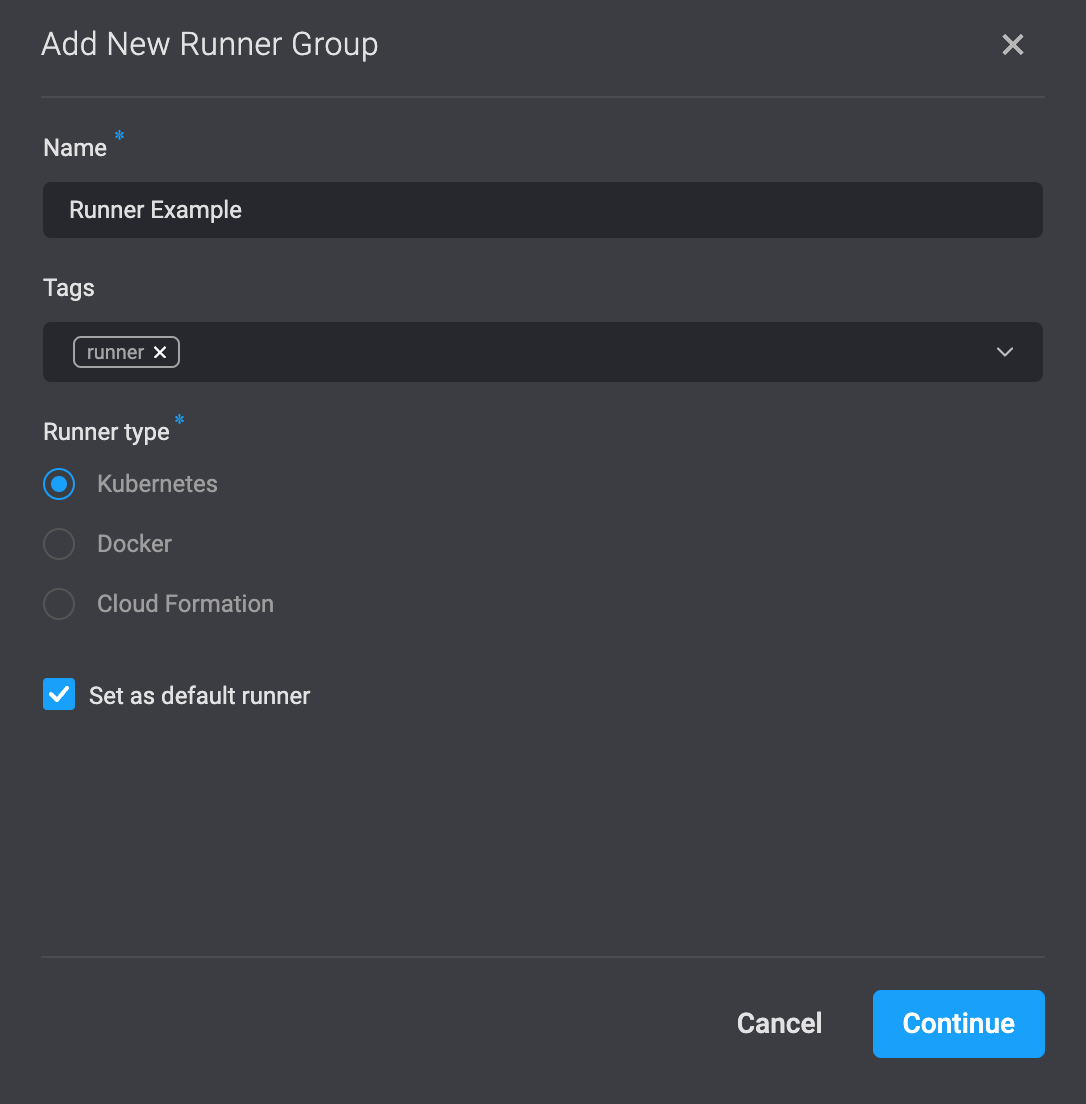
Copy the Runner Installation Command
To proceed, click on the ‘Continue’ button located in the bottom-right corner. This will prompt the opening of a dialogue box where you can access the command required to install the Runner in your environment. Simply copy this command to your clipboard by clicking on the icon positioned in the top-right corner.
Edit and Configure the Runner Command
Edit the command to add the environment variables you obtained when creating a Service Account:
GCP_SECRET_MANAGER_AUTH_TYPE, GCP_SECRET_MANAGER_CREDENTIALS, GCP_SECRET_MANAGER_PROJECT_ID and SECRET_MANAGER_TYPE- Docker example command:
- Kubernetes command example: