Security principles
Minimal trust methodology Blink has adopted a minimal trust methodology to keep customers as independent as possible from Blink when it comes to their security posture. Blink is designed to serve as an abstraction & automation level over existing SaaS services that are being used by the customers, and by that prevents granting power/trust to Blink to take actions on customer’s behalf. Data security To create a secure environment for users, data security measures in all aspects are taken. Security of data in transit, stored data, secured backups, strict data access principles, cloud security posture etc. have been taken into account during the creation and maintenance of the Blink platform. Role-based access control (RBAC) Blink allows granular RBAC permission management, using roles, permissions, workspaces, groups, and resources. Using Blink’s RBAC, customers are able to import existing permissions of users from their existing SaaS permissions, as well as utilizing different authorization approaches under RBAC within the account.Data security
Blink SaaS data flow diagram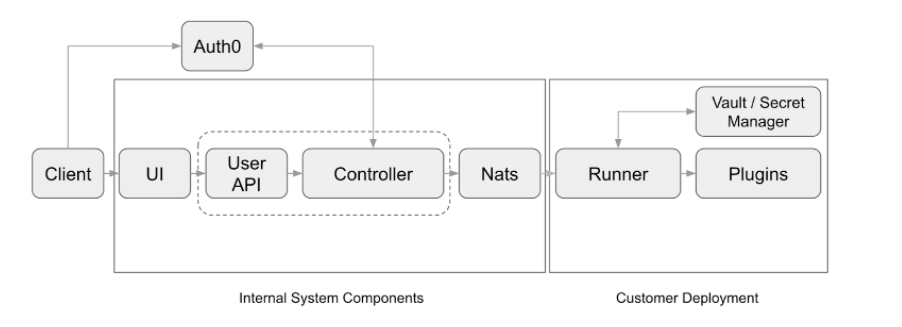
- Account metadata
- User details
- Automation content
- Resources names & types
- Logs of Automation executions
- User credentials
- Users Automations
- Step outputs
Main security measures
Customer identity Any action performed by Blink users is signed by a JWT token. The identity token is generated by an external authentication provider and is validated through the customer’s request. By enforcing the performed action signature, Blink mitigates the risk of Man In Middle and Request forgery attack vectors. Credentials Security (Credentials Jail)- Blink is relying on external credentials in order to allow users to integrate and interact with external SaaS services. To avoid dangers related to credentials, Blink on-prem solution allows the user to keep all credentials usage on-premise. Blink will integrate to the customer’s secret manager. Currently supported secret managers include Hashicorp Vault and AWS Secret Manager.
- Usage of credentials on a runner-based system where running code is allowed, imposes the risk of credentials leaking - either by accident or by adversary action. Blink mitigates this risk by applying a Credentials jail - credentials are exposed only to pre-built and acknowledged system actions, rather than being directly exposed to arbitrary usage.
Additional security measures
Environment Isolation Blink offers two run modes in terms of isolation:- Shared environment - Use the main Blink cloud service, which is shared across multiple accounts. Data is separated by per-tenant separation.
- Dedicated SaaS namespace - Network, data flow, data storage and all business logic is completely separated at this mode. Data is separated on a DB per customer basis.
Security & Privacy policies and standards
In addition to the security measures detailed in this document, Blink acts upon the highest industry standards on security topics. Blink can provide documentation related to these topics at the customer’s request. These topics include the following:- Compliance
- Password management
- Permission access management
- Privacy policy
- Risk assessment
- Third-party vendor management
- Key management and information security
- Incident response
- Auditing
- Environment security
- Data retention and erasure
- Backup policy
- Endpoint security