Note: Audit logs are retained for a duration of 30 days.
- Approval management
- Cases
- Case related tables
- Connections
- Dashboards
- Global variables
- Runners
- Self-service apps
- Tables
- Tenant admin settings
- Tenant user management
- Users
- Workflows
- Workspace management
The audit logs do not track changes to data or content, such as workflow action updates, workflow executions, modifications to table records, or changes to cases.
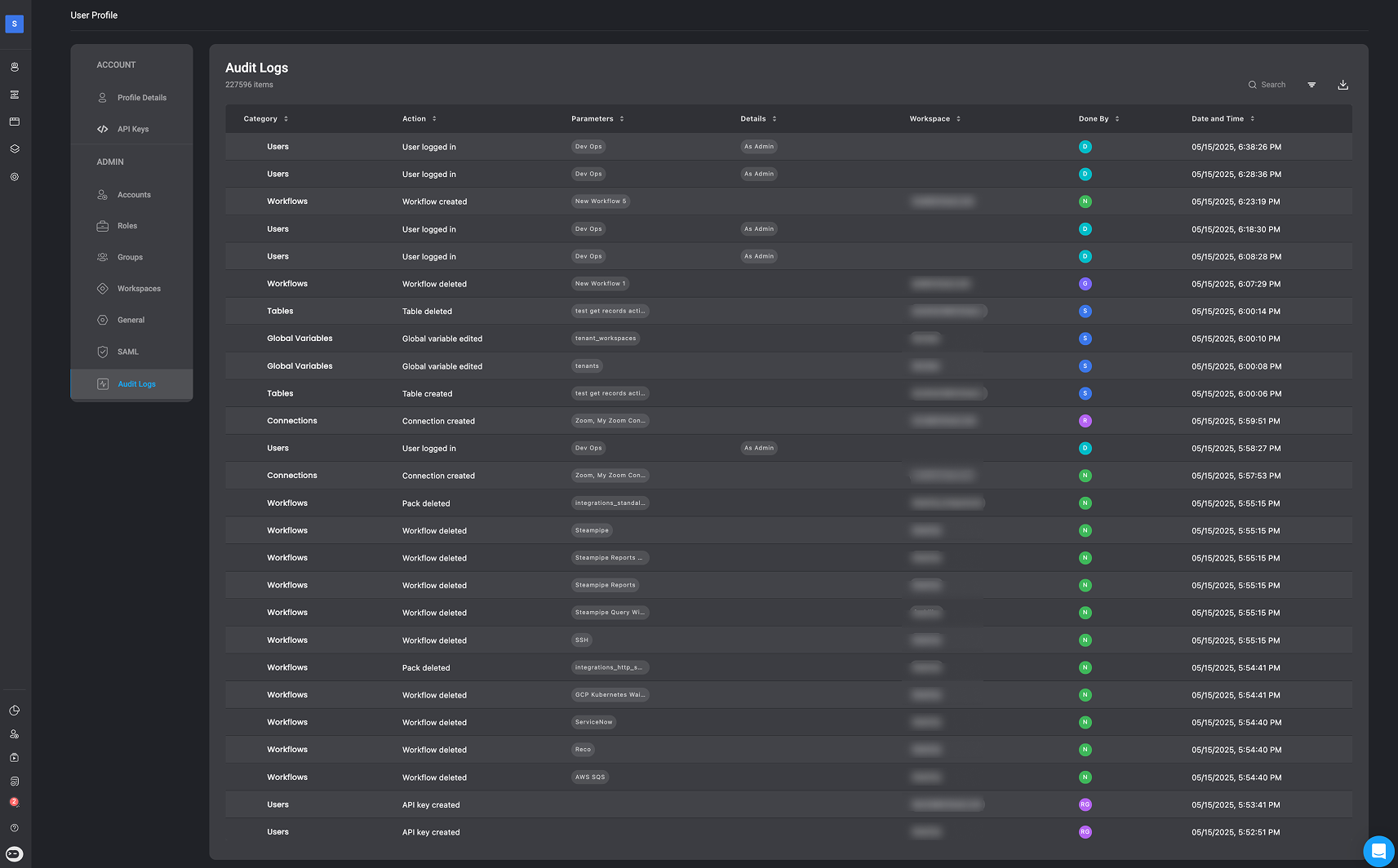
Audit Log Table Content
Each log entry includes the following information:- Category – The general type of activity: Setting updates, System configuration, or User actions.
- Action – The specific action that occurred.
- Parameters – Key data relevant to the action, such as the affected username, Workflow name, or API endpoint.
- Details – Additional context or information about the action.
- Workspace – The name of the workspace where the action took place.
- Done by – The email address of the user who initiated the action.
- Date and Time – When the action was performed.
Categories and Events
In the following section, you can find a complete overview of Blink’s audit log categories and the types of events captured within each. Audit logs in Blink are designed to give you full visibility into user activity, system changes, and workflow executions across the platform.Audit Log Categories and Events
Audit Log Categories and Events
Approval Management
| Event | Description |
|---|---|
| Request approved | A submitted request was approved by an authorized user. |
| Request denied | A submitted request was denied by an authorized user. |
| Request submitted | A request was submitted for approval. |
Cases
| Event | Description |
|---|---|
| Case exported | A case was exported to a downloadable format. |
| Case shared | A case was shared with external parties or users. |
| Table exported to CSV | A case table was exported in CSV format. |
Case Related Tables
| Event | Description |
|---|---|
| Custom cases table created | A new custom table for cases was created. |
| Custom cases table edited | An existing custom cases table was edited. |
| Exported to CSV | Data from a custom cases table was exported as a CSV file. |
| Field created | A new field was added to a custom cases table. |
| Field edited | A field in a custom cases table was updated. |
| Field deleted | A field was removed from a custom cases table. |
Connections
| Event | Description |
|---|---|
| Connection created | A new integration connection was created. |
| Connection deleted | An existing integration connection was removed. |
| Connection edited | An integration connection was modified or updated. |
Dashboards
| Event | Description |
|---|---|
| Dashboard activated | A dashboard was activated and made live. |
| Dashboard created | A new dashboard was created. |
| Dashboard deactivated | A dashboard was deactivated. |
| Dashboard deleted | A dashboard was deleted. |
| Dashboard edited | Changes were made to a dashboard’s configuration or layout. |
| Dashboard metadata edited | Metadata for the dashboard (e.g., tags, ownership) was updated. |
Global Variables
| Event | Description |
|---|---|
| Global variable created | A new global variable was created. |
| Global variable deleted | A global variable was removed from the system. |
| Global variable edited | An existing global variable was updated or changed. |
Runners
| Event | Description |
|---|---|
| Runner group created | A new group for managing runners was created. |
| Runner group deleted | A runner group was deleted. |
| Runner group edited | A runner group’s settings or members were updated. |
| Runner group set as default | A runner group was marked as the default for new workflows or tasks. |
Self-Service Apps
| Event | Description |
|---|---|
| App created | A new self-service app was created. |
| App deleted | A self-service app was removed. |
| App published | A self-service app was published and made available. |
Tables
| Event | Description |
|---|---|
| Field created | A new field was added to a data table. |
| Field deleted | A field was removed from a data table. |
| Field edited | A field in a table was modified. |
| Table created | A new data table was created. |
| Table deleted | A data table was deleted. |
| Table edited | A data table was updated or modified. |
| Table exported to CSV | A table’s contents were exported to a CSV file. |
Tenant Admin Settings
| Event | Description | |
|---|---|---|
| Audit logs exported | Audit logs were exported for review or archiving. | |
| Blink-cloud runner updated | Settings for the Blink cloud runner were updated. | |
| Default tenant runner updated | The default runner for the tenant was changed. | |
| Runner auto upgrade updated | Auto-upgrade settings for runners were modified. | |
| SAML role mapping updated | Role mapping configuration for SAML was updated. | |
| SAML settings updated | SAML authentication settings were changed. | |
| Two-factor authentication disabled | Two-factor authentication was disabled for the tenant. | |
| Two-factor authentication enabled | Two-factor authentication was enabled for the tenant. | |
| Time format updated | The time display format used across the Blink platform was changed. | |
| Date format updated | The date display format used across the Blink platform was changed. |
Tenant User Management
| Event | Description |
|---|---|
| Group created | A new group was created. |
| Group deleted | An existing group was deleted. |
| Group name updated | The name of a group was changed. |
| Role created | A new role was created. |
| Role deleted | An existing role was deleted. |
| Role updated | An existing role was updated. |
| Service account activated | A service account was activated. |
| Service account created | A new service account was created. |
| Service account deactivated | A service account was deactivated. |
| Service account deleted | A service account was deleted. |
| Service account group assignment updated | A service account’s group was updated. |
| Service account role changed | A service account’s role was changed. |
| User activated | A user was activated. |
| User deactivated | A user was deactivated. |
| User deleted | A user was deleted. |
| User group assignment updated | A user’s group assignment was updated. |
| User invited | A user was invited. |
| User role changed | A user’s role was changed. |
Users
| Event | Description |
|---|---|
| User logged in | A user logged in. |
| User logged out | A user logged out. |
| API key created | An API key was created. |
| API key deleted | An API key was deleted. |
Workflows
| Event | Description |
|---|---|
| Pack created | A new pack was created. |
| Pack deleted | A pack was deleted. |
| Pack edited | A pack was edited. |
| Workflow activated | A workflow was activated. |
| Workflow created | A new workflow was created. |
| Workflow deactivated | A workflow was deactivated. |
| Workflow deleted | A workflow was deleted. |
| Workflow published | A workflow was published. |
| Workflow settings updated | Workflow settings were updated. |
Workspace Management
| Event | Description |
|---|---|
| Workspace created | A new workspace was created. |
| Workspace deleted | A workspace was deleted. |
| Workspace name updated | A workspace’s name was updated. |
| User invited/added | A user was invited or added. |
| User removed | A user was removed. |
| User role changed | A user’s role in the workspace was changed. |
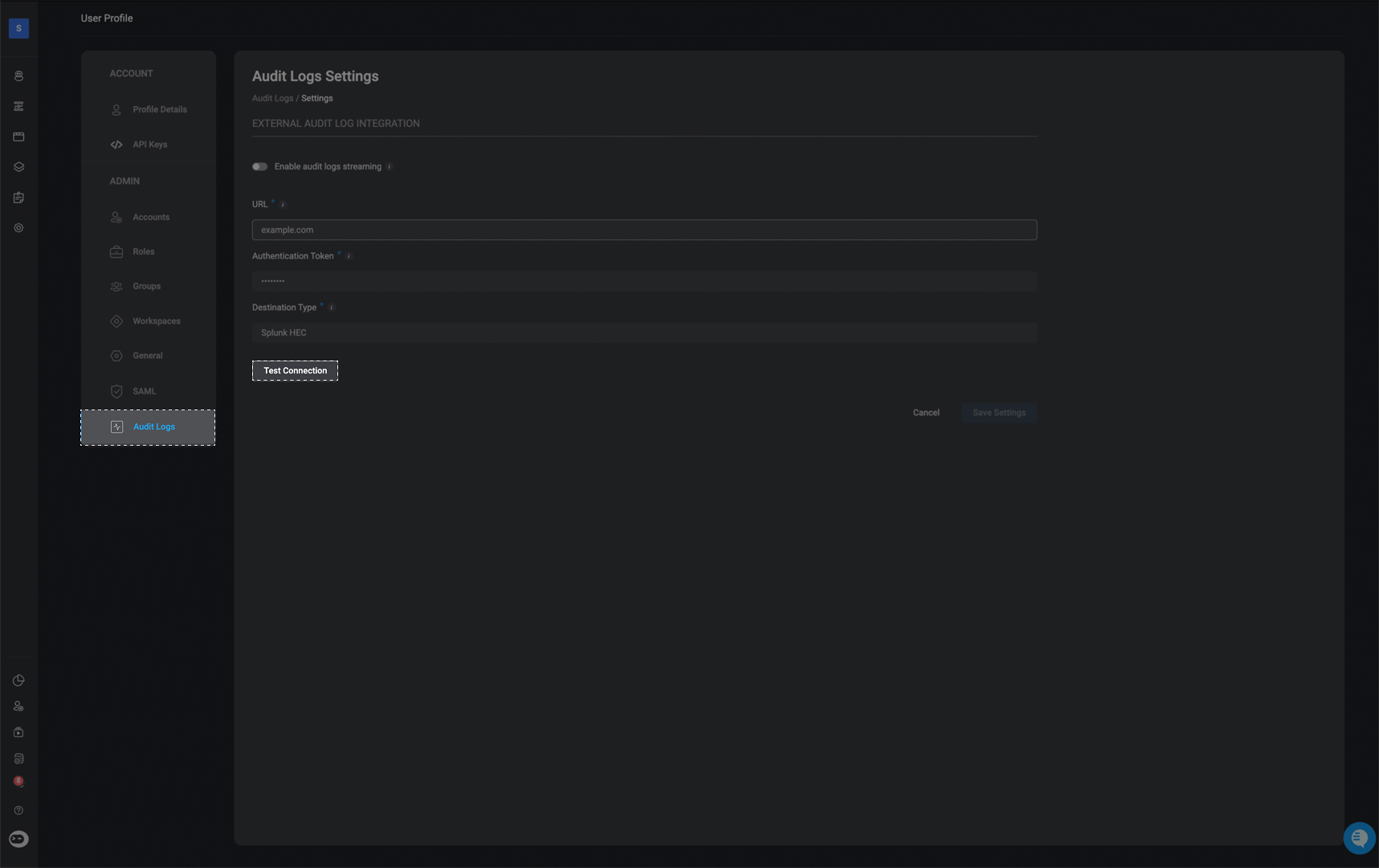
External Audit Log Integration
Blink supports native audit log streaming to external SIEM systems, allowing organizations to integrate Blink audit data into tools like Splunk or Elasticsearch. This feature gives security teams greater visibility and control by centralizing audit logs for compliance, monitoring, and incident response without the need for manual exports. Tenant admins can configure their SIEM endpoint directly in Blink, test the connection, and begin streaming audit logs in real time.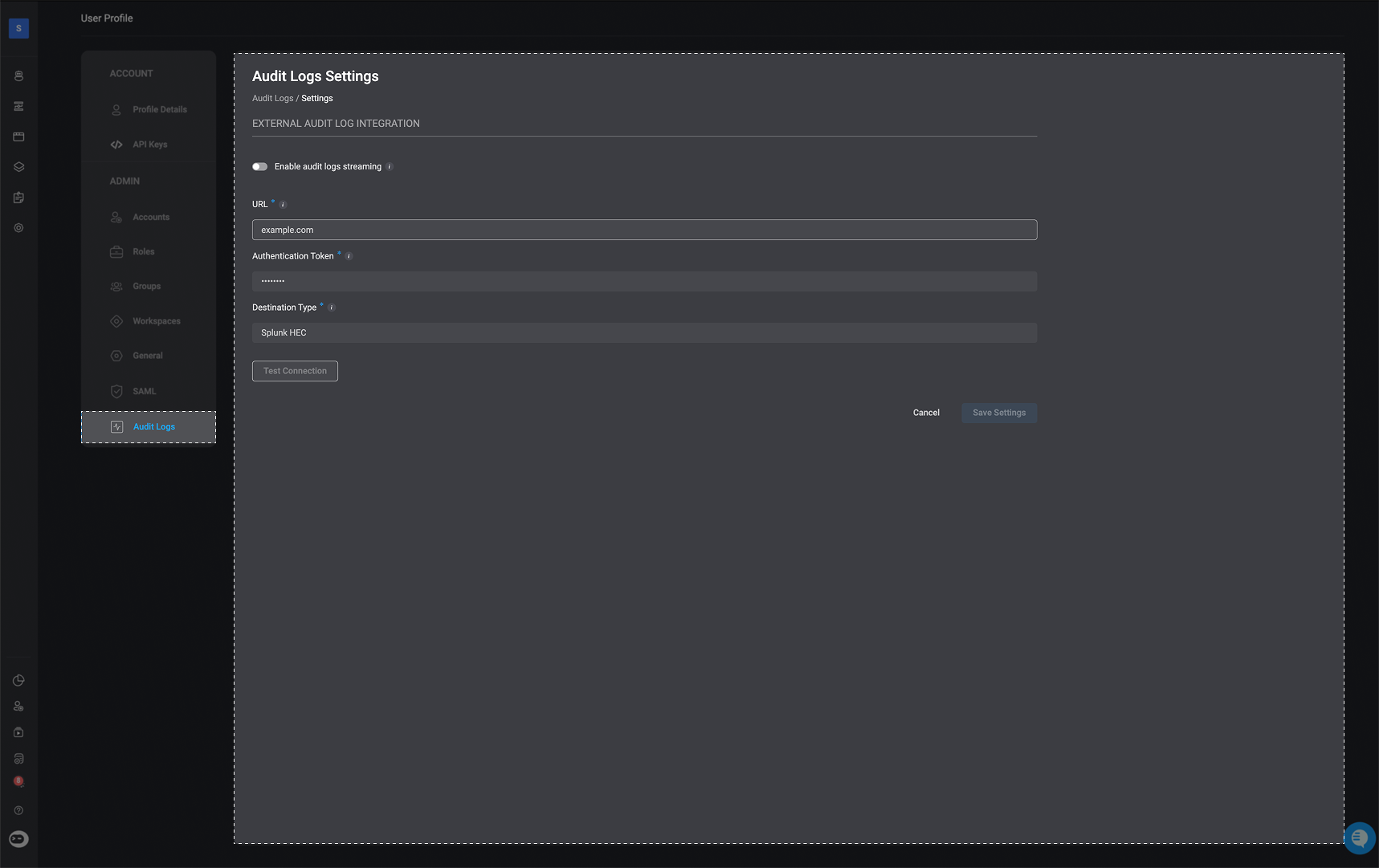
Navigate to the 'Audit Log Settings' page
In the top right-corner of the Audit Log page, select the icon
Enter the Required Parameters
-
Enable audit log streaming:
- When enabled, audit logs will be delivered to your specified external destination in real time.
- Disabling this will stop all log delivery and deactivate the form below.
-
URL:
- The destination URL for your external logging service.
This must be a reachable HTTPS endpoint that supports log ingestion.
- The destination URL for your external logging service.
-
Authentication Token:
- A token or API Key used to authenticate requests to your external logging endpoint. This is required for secure delivery of audit logs.
-
Destination Type- Select the type of destination where logs will be sent:
- Splunk HEC
- HTTP (Bearer Auth)
- Elasticsearch
Configuration Guide: Generating a Splunk HTTP Event Collector (HEC) Token
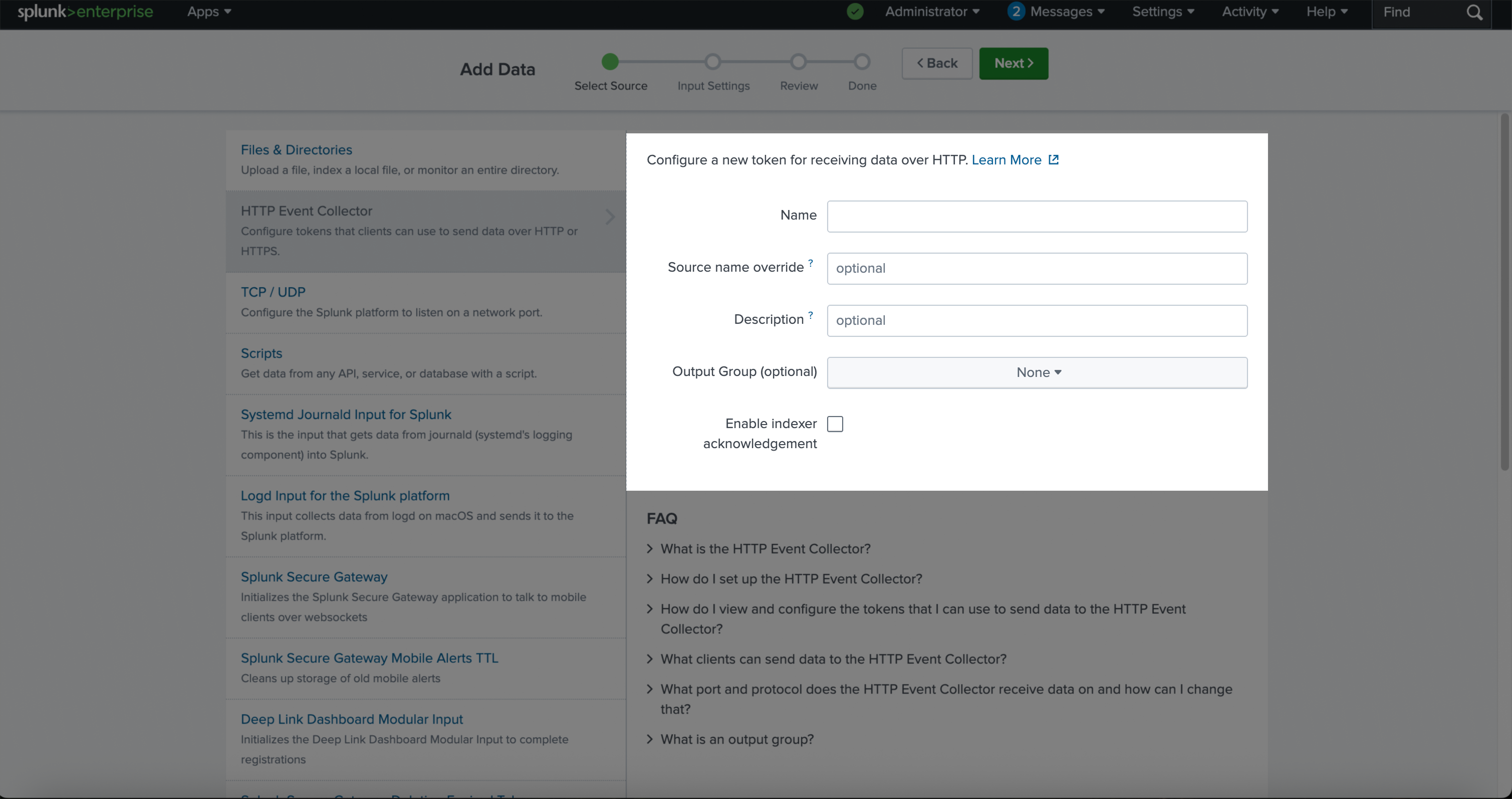
Follow this step-by-step guide, to learn how to generate Splunk HTTP Event Collector (HEC) token, which is required for integrating Splunk with the Blink platform. This token is required to integrate Splunk with the Blink platform in order to stream Blink’s audit logs to a selected external destination.Access the HTTP Event Collector
Log in to your Splunk Enterprise account. In the top-right corner, click on Settings, then search for HTTP Event Collector and select it.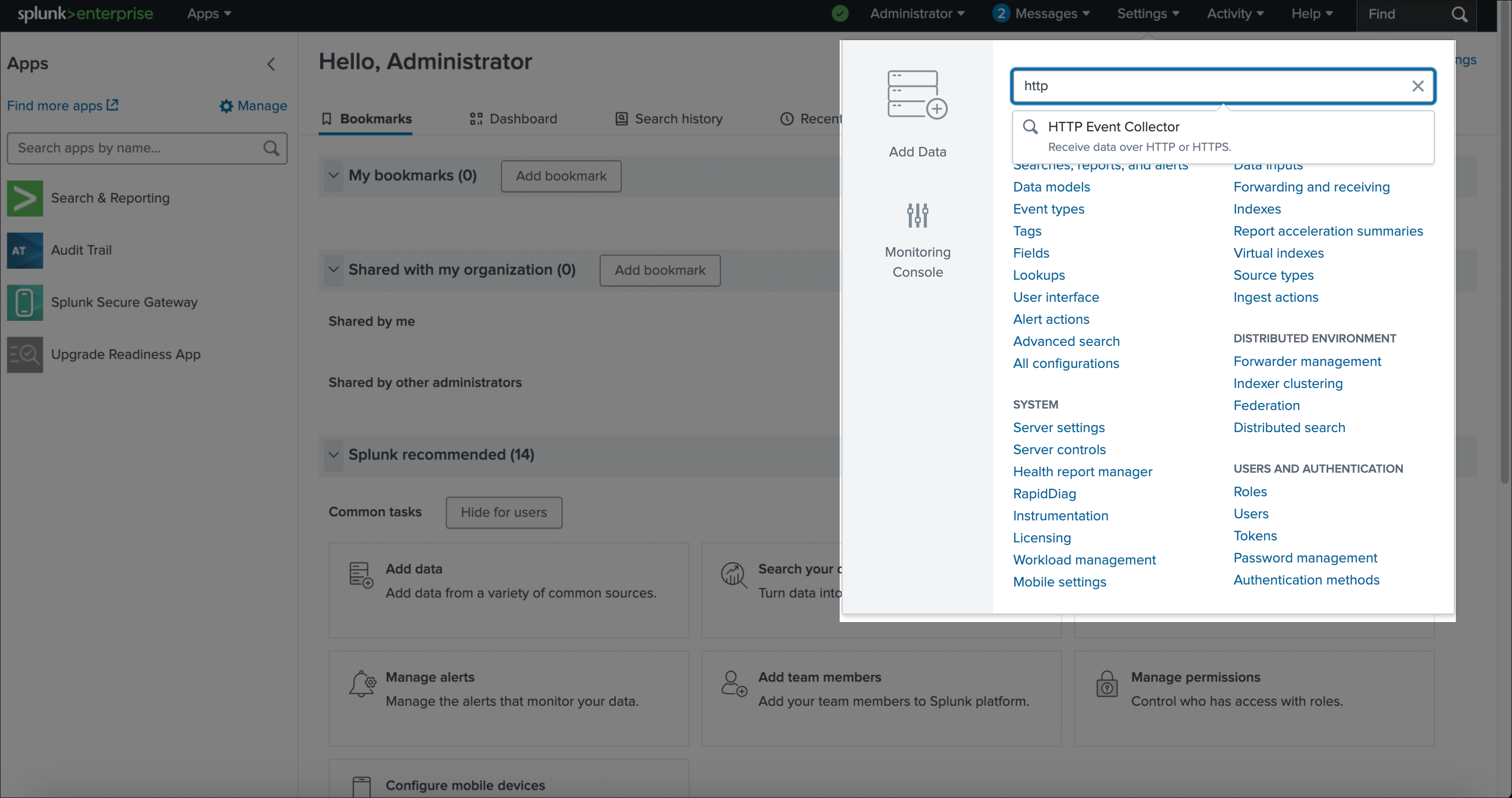

Input Settings
Choose the appropriate indexes that the ‘HTTP Event Collector’ token will be allowed to access.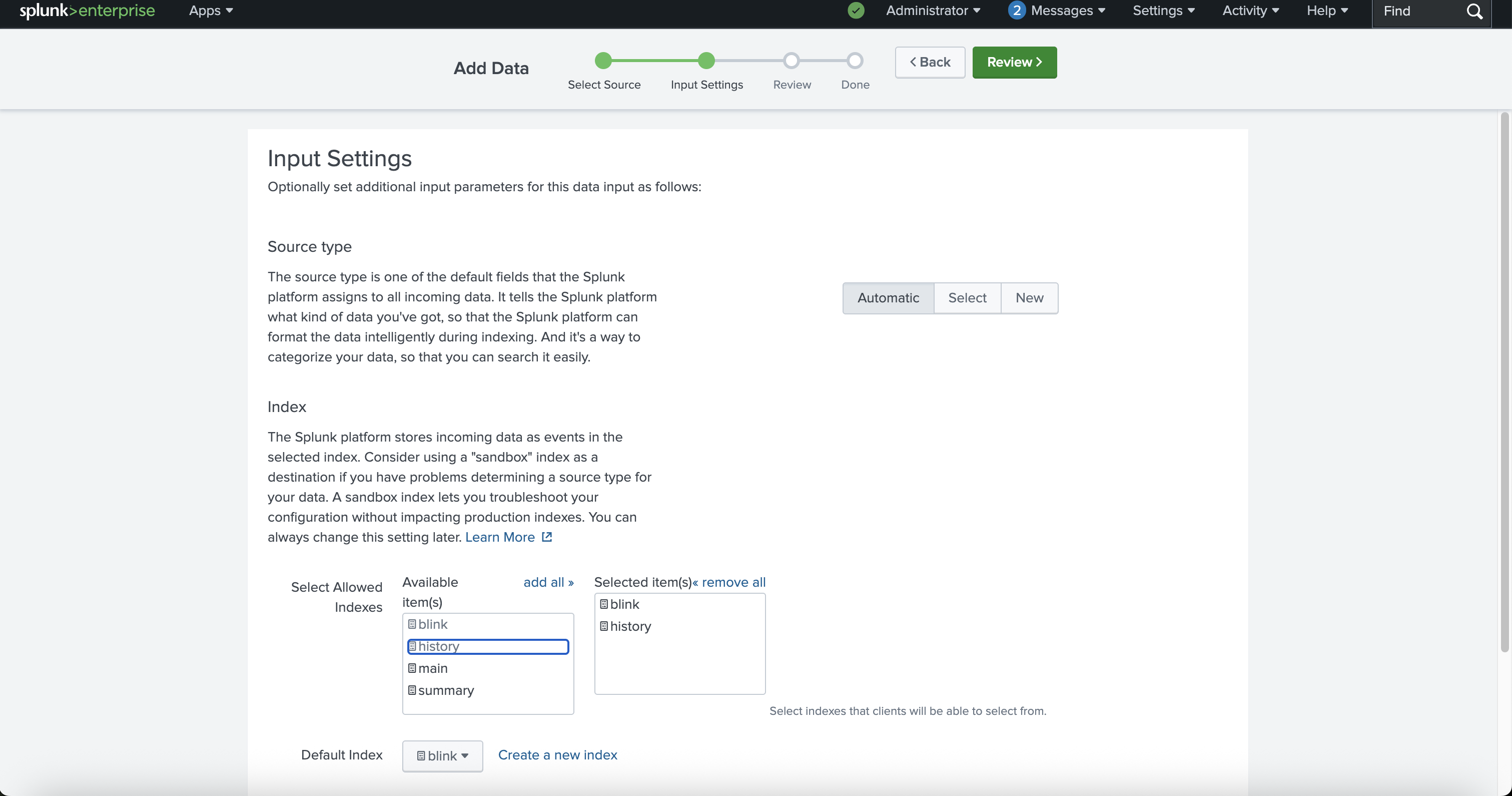

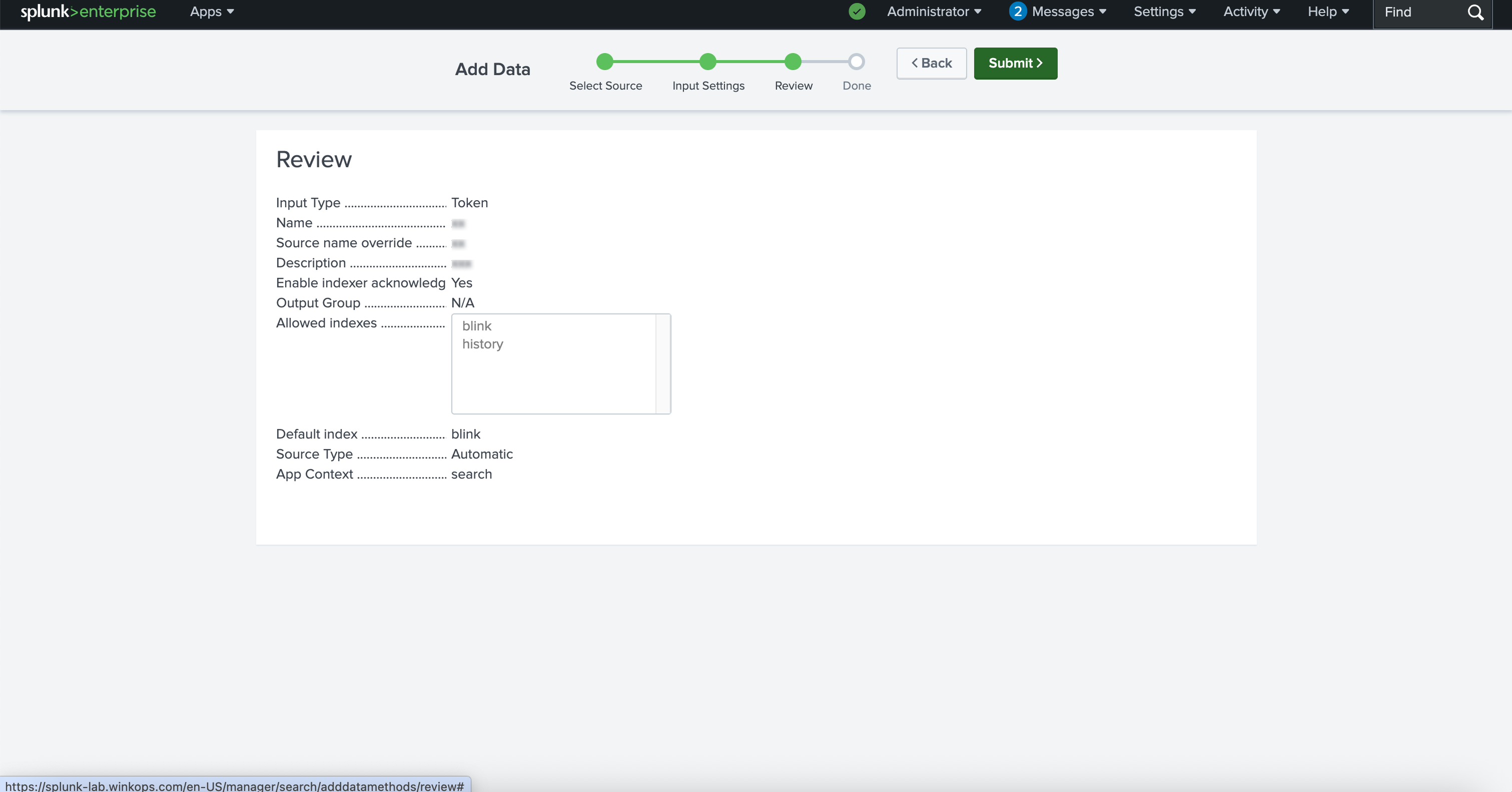
Token Created Successfully
Once the token has been generated in Splunk, copy it and securely store it.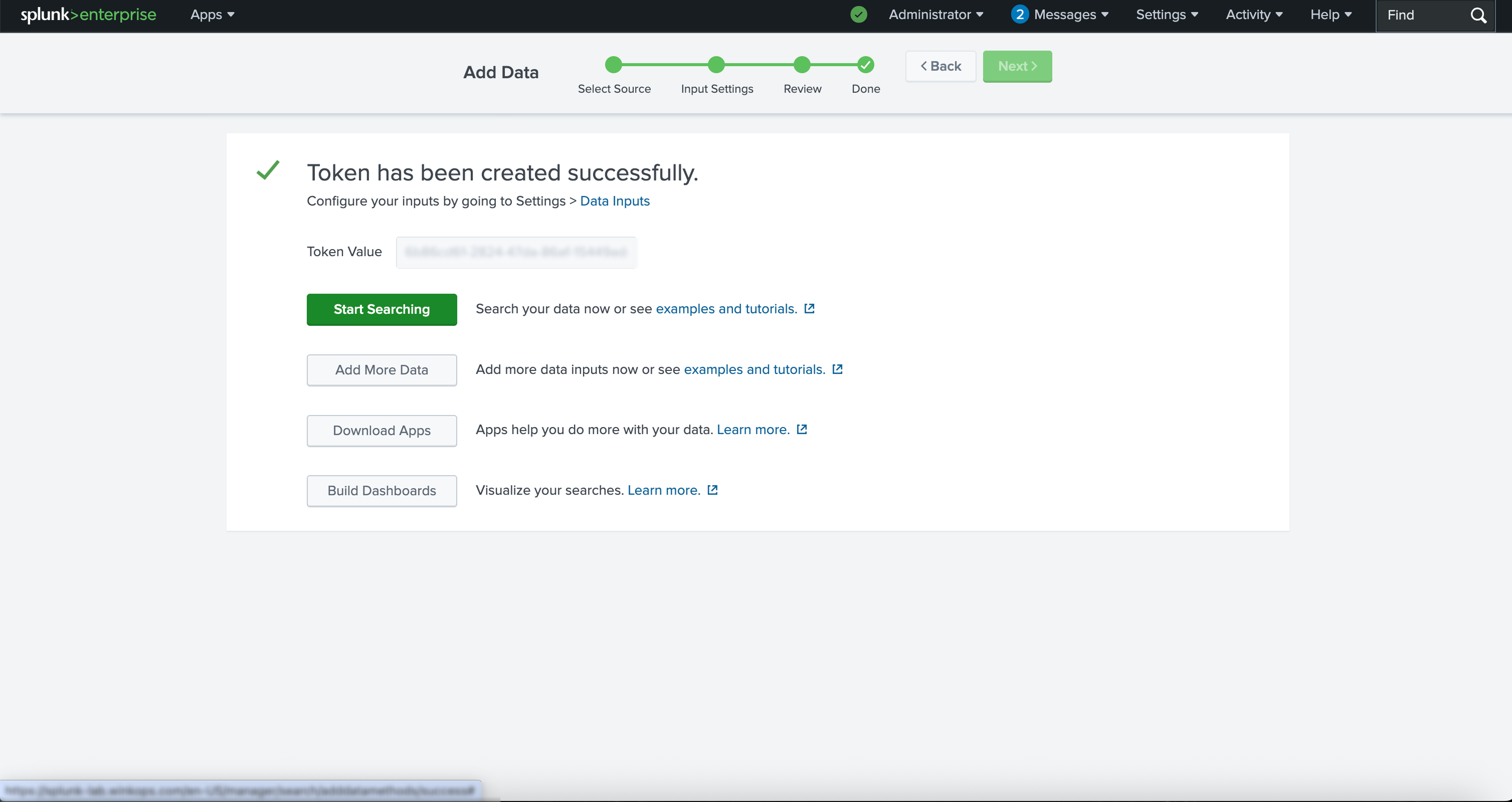

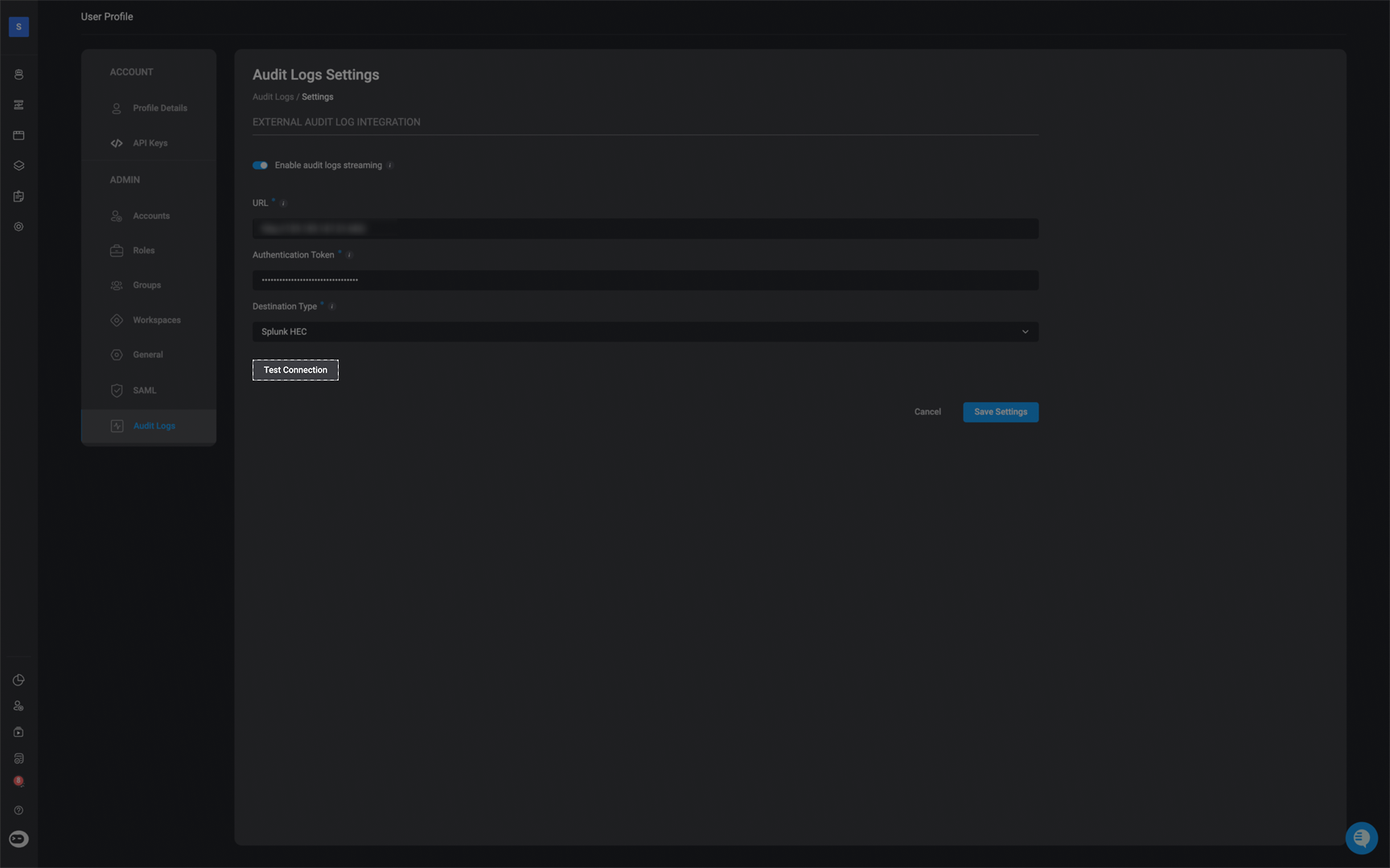
Integrate with Blink
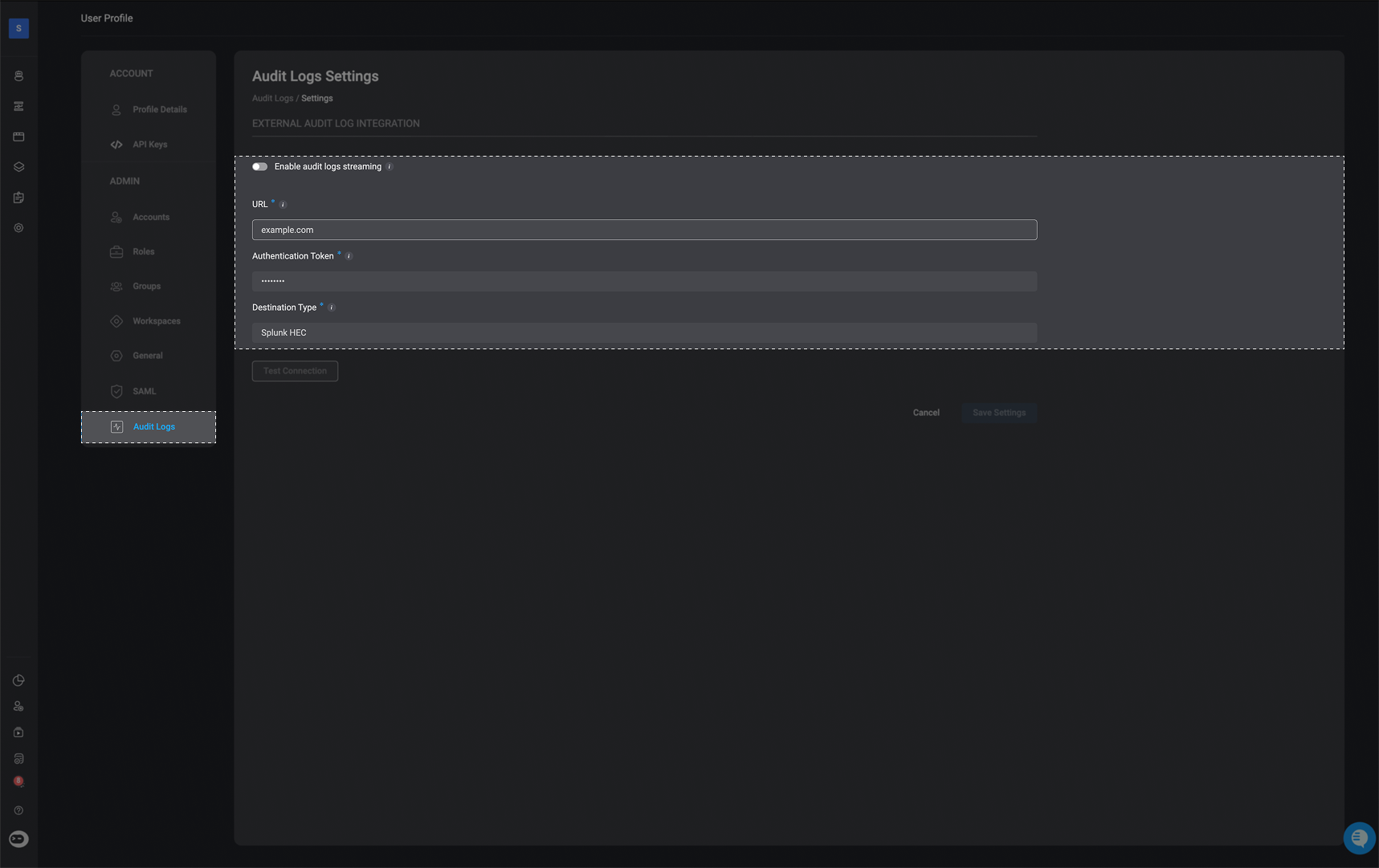
To complete the integration with Blink, go to the Audit Settings section of the Blink platform and do the following:
- Paste the token into the Authentication Token field
- Enter the URL: If the HEC feature is enabled in the Splunk Enterprise platform you will see the port it uses (by default, it’s
8088). Your full url will look something like thishttps://splunk.yourcompany.com:8088 - Select Splunk HEC as the Destination Type