If you are using Case Management version
9.0, you should refer to this pageIP addresses, URLs, usernames, file hashes, and hostnames. These observables are critical for understanding the context and impact of an alert, enabling subsequent enrichment, triage, and response actions.
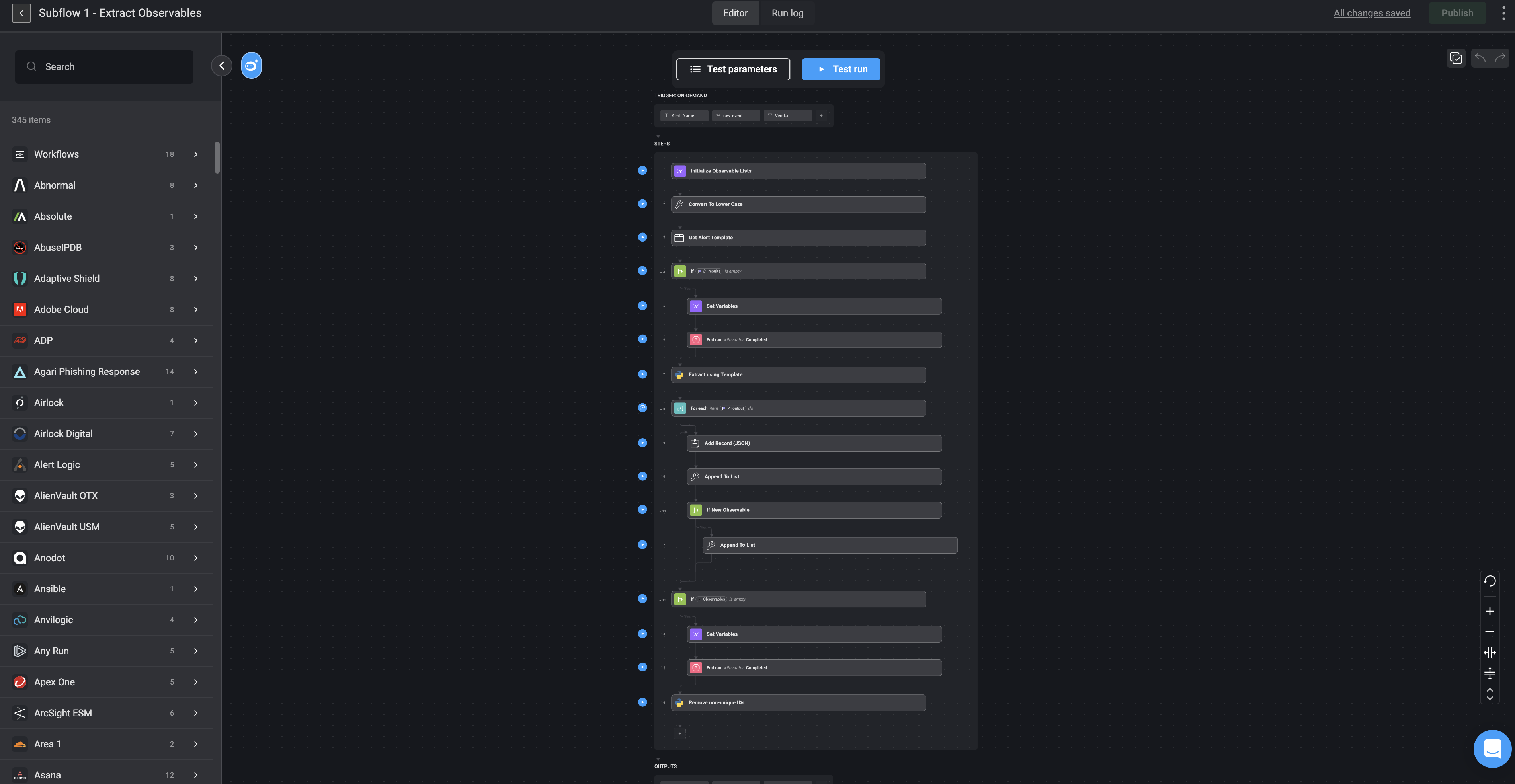
How It Works
-
Initialization and Preprocessing:
- The subflow begins by initializing an observable list to store extracted data points. This ensures all relevant observables are collected systematically and can be processed further.
-
Template-Based Parsing:
-
Using templates from the Alert Template Table, the subflow identifies the specific paths in the alert payload where observables are located. These templates are defined in JSON format, with each key representing a payload path (e.g.,
device.external_ip) and its corresponding value indicating the observable type (e.g., “IP Address”). -
For example, if an alert contains a field
device.hostname, the template maps it as"Target Hostname", ensuring consistent extraction across alerts.
-
Using templates from the Alert Template Table, the subflow identifies the specific paths in the alert payload where observables are located. These templates are defined in JSON format, with each key representing a payload path (e.g.,
-
Extraction and Validation:
- The system converts data into a standardized format (e.g., lowercase for uniformity) and uses the JSON templates to extract observables. It then checks whether each extracted observable is valid and unique, ensuring no duplicate or irrelevant data is processed.
-
Appending Observables:
- Extracted observables are appended to the initialized list, categorized by type (e.g., network observables like
IPs, user observables likeusernames)`. The system dynamically updates the list with valid entries, which is critical for downstream tasks.
- Extracted observables are appended to the initialized list, categorized by type (e.g., network observables like
-
Post-Processing:
- After extraction, any unstructured or unused identifiers are removed from the observable list to maintain efficiency and relevance. This ensures that only actionable data is passed on to the next stages.
Example of Raw Alert Payload
Click here to see the full payload
Click here to see the full payload
Examples of Extracted Observables
- Network Observables:
device.external_ip: Identifies an external IP address potentially involved in an alert.device.local_ip: Captures local IPs within the organization’s network for context.
- Host and User Observables:
device.hostname: Indicates the specific host impacted by the alert.user_name: Extracts usernames related to suspicious activity.
- File-Based Observables:
sha256: Extracts file hashes to identify potentially malicious files.parent_details.sha256: Retrieves parent process file hashes for advanced analysis.
Significance in the Workflow
This subflow ensures that all actionable data is prepared for subsequent stages in the workflow. For instance:- The Enrich Observables subflow leverages these extracted data points to gather additional threat intelligence.
- The Check for Case Duplicates subflow uses these observables to identify if similar alerts already exist in the system, preventing redundancy.