Safe Use of AI
It is important that Blink does not use customer data for AI training. We adhere to industry standards to ensure your data remains secure, never stored or utilized for these purposes.
Using the Analyst Copilot
Through the Analyst Copilot’s chat interface, analysts can enter a question or prompt, to quickly gather relevant information, execute enrichment tasks, and take remediation actions based on a case’s predefined details. The Copilot can also leverage Ability Workflows that provide additional insights and automate tasks. Any output generated by these workflows is automatically added to the session context, keeping all relevant information in one place. By combining AI guidance with automated workflows (Ability Workflows), the Analyst Copilot accelerates case resolution and provides actionable insights throughout the investigation process.For more information about Ability Workflows, navigate here

| Component | Description | |
|---|---|---|
| 1 | Prompt / Question | A predefined or user-entered instruction that the Analyst Copilot will use to analyze the case, summarize details, or perform an investigation task. |
| 2 | Answer | The Copilot’s generated response based on the prompt. This may include summaries, analysis, recommended next steps, or insights derived from the case data. |
| 3 | Text Field to Enter the Prompt | The input field where you can type a question or command for the Analyst Copilot. Each entry generates a new response within the active session. |
| 4 | Copilot Abilities Tab | A panel displaying all the linked copilot capabilities available to the Analyst Copilot. This includes enrichment actions, investigation helpers, and workflow-driven tools. |
| 5 | Copilot Abilities | Workflows that the Analyst Copilot can invoke to support case investigation, enrichment, remediation, and other actions. Any workflow results are automatically added to the session context. To add additional abilities, see the next section on exposing on-demand workflows to the Analyst Copilot. |
Expose Abilitty Workflows to the Analyst Copilot
Ability workflows are on-demand workflows that extend the Analyst Copilot, enabling more detailed analysis and investigation. In any on-demand workflows, you can enable the Analyst Copilot by toggling the Analyst Copilot workflow button in the workflow’s settings or on the Workflow Overview page. Once enabled, the workflow is added to the Analyst Copilot as an ability workflow. This setting gives the Analyst Copilot access to the workflow’s configuration and outputs, supporting deeper analysis, informed decision-making, and guided response. With visibility into the workflow’s structure and data, the Copilot can more effectively assist analysts throughout the investigation process.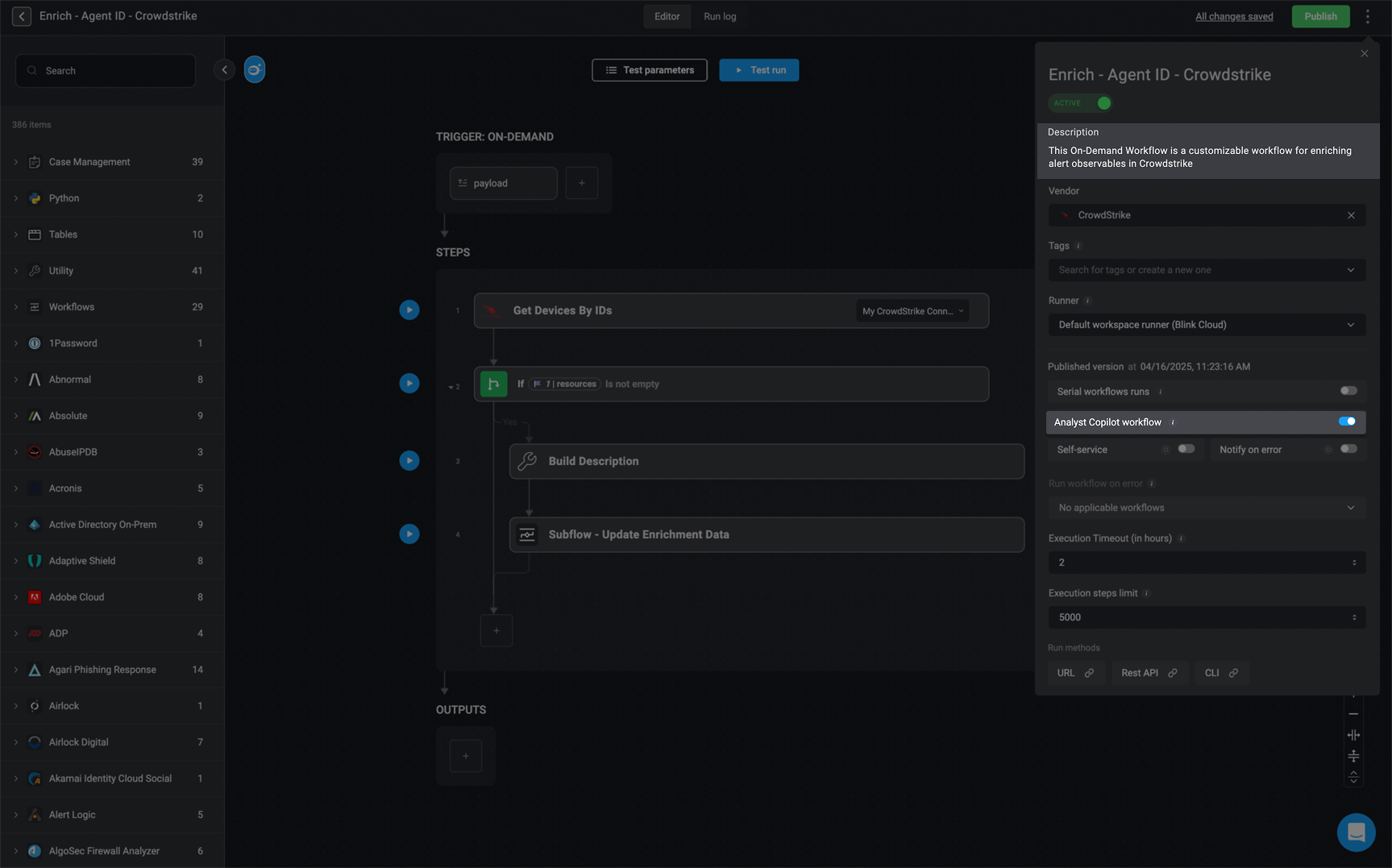
Analyst Copilot Ability Workflow’s Activity
When the Analyst Copilot triggers an ability workflow, it is automatically recorded and displayed in the Case Management timeline. The log records both the name of the triggered ability workflow and the user who executed it. This ensures full visibility into all Copilot-driven actions and helps analysts easily keep track of Analyst Copilot activity throughout the investigation.
Use Case Examples: Analyst Copilot in Case Management
Use Case Example: Generate a timeline of events based on the case activity
Use Case Example: Generate a timeline of events based on the case activity

Overview
The Analyst Copilot assists security analysts by automatically generating insights and structured timelines for cybersecurity incidents. In this case, it processes details related to a malware-attached email and creates a timeline of events based on case activity.Key Capabilities Demonstrated
-
Automated Timeline Generation
- The Copilot extracts relevant information from the alert and observables sections and structures it into a chronological timeline of events.
- Example:
- Initial detection of a malicious URL.
- Receipt of the malicious email.
- Identification of the malicious attachment.
- Alert generation in Proofpoint security system.
- Case creation in the Blink’s Case Management for investigation.
-
Enhanced Investigation Efficiency
- By automatically summarizing critical case details, the Analyst Copilot reduces manual effort required from analysts.
- This allows analysts to focus on deeper investigations rather than compiling reports.
-
Real-time Case Status Tracking
- The system tracks case status (e.g., “NEW”, “UNDER INVESTIGATION”) and keeps analysts updated.
- Ensures that all stakeholders have a clear progression of events.
Why This is Valuable for Security Teams
- Speeds Up Incident Response – Analysts get an immediate structured summary without manually sifting through logs.
- Improves Accuracy – Extracts key details directly from security tools, reducing human error.
- Enhances Collaboration – Clear, structured timelines help teams coordinate actions effectively.
Use Case Example: Suggest a remediation plan based on this case.
Use Case Example: Suggest a remediation plan based on this case.

Overview
In this use case, the Analyst Copilot assists in responding to a brute force attack involving suspicious login attempts. The copilot helps the analyst review response actions linked to the case, trigger relevant workflows (e.g., DNS lookups), and suggest a detailed remediation plan, all from within the same interface and using natural language commands.Key Capabilities Demonstrated
-
Case Context Awareness
- Identifies and summarizes response actions specific to the case.
- Understands key case elements like involved users, source IPs, and severity.
-
Natural Language Automation Execution
- Executes security workflows based on plain language prompts (e.g., “Investigate source IPs”).
- Automatically maps case data (e.g., IP addresses) to required inputs.
-
Result Interpretation and Next-Step Guidance
- Provides structured output from workflows in plain English.
- Offers follow-up investigation recommendations based on results (e.g., manual IP analysis after NXDOMAIN result).
-
Remediation Planning Support
- Generates a step-by-step remediation plan organized by urgency (Immediate, Short-term, Medium-term, Long-term).
- Takes into account case metadata such as severity, user role, and business impact.
Why This Is Valuable for Security Teams
- Reduces Analyst Workload Automatically surfaces relevant information and actions without needing to manually navigate through multiple tools or tabs.
- Accelerates Incident Response Automations can be executed and interpreted instantly, significantly reducing investigation and response time.
- Promotes Consistent and Repeatable Workflows Ensures incident handling follows a structured process, even for less experienced analysts.
- Enhances Transparency and Documentation Each action is traceable and tied to the case timeline, supporting audit and compliance needs.
- Keeps Momentum Despite Tooling Gaps The copilot doesn’t fail silently, it identifies where coverage is missing and recommends manual next steps, helping teams maintain investigative momentum.
Best Practices
- Be clear and precise: Providing clear and specific instructions will assist Analyst Copilot in understanding your instructions clearly.
- Use complete integration names: For example, instead of using generic terms like Compute Instance, specify the full name of the relevant integrations, such as AWS EC2 Compute Instance.
- Refrain from using unknown or unrecognized vendors in your prompt.
- Keep it simple and concise: To tackle complex workflows effectively, consider breaking your prompt instructions into bullet points, ensuring each bullet point prompt is concise and straightforward.
Related Articles
Case Management
Effectively handle security incident investigations by providing detailed information and logs in one place on a single dashboard
Cases
Track, manage, and resolve cases efficiently.
Alerts
Track, manage, and resolve alerts efficiently.
Observables
Create, Extract and manage observables efficiently.