v9.0
The Response- Main Router subflow is a key part of the alert processing parent workflow. It is responsible for deciding how to respond to different types of alerts and carrying out the appropriate actions automatically.
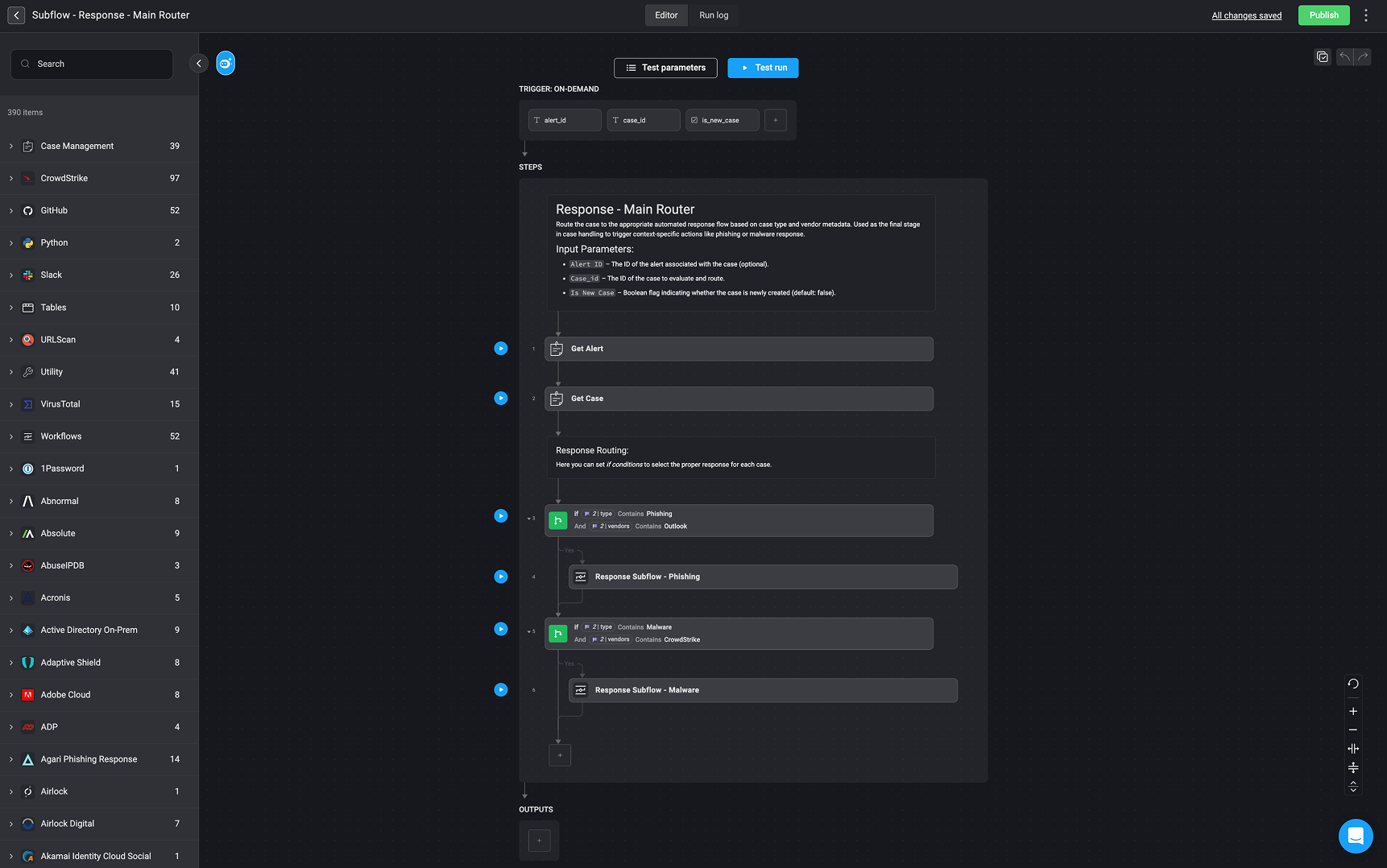
How its Works
In this example, the subflow starts by looking at information collected and enriched in earlier steps of the workflow. For instance, it examines alert details such as the type of threat (e.g., phishing or malware) and which security tool detected it (e.g., Outlook or CrowdStrike). Based on these details, the subflow follows one of two paths:-
If the alert is a phishing attempt detected by Outlook:
The subflow routes the alert to a specific process for handling phishing threats. This might involve actions like warning the affected user, blocking suspicious emails, or securing accounts to prevent further issues. -
If the alert is malware detected by CrowdStrike:
The subflow sends the alert to a process for handling malware. This could involve isolating an infected device, notifying the security team, or starting an investigation to analyze the threat.