If you are using Case Management version
9.0, you should refer to this pageCase Management Automated Processes
Alert Ingestion
In the Alert Ingestion process, alerts are harvested from external systems, such as SIEMs (Security Information and Event Management) or other monitoring tools, in real time. This step collects raw alert data as soon as it is generated by the vendor. The primary action in this stage is to open an alert record, which stores the received payload for further processing. This is the starting point of the workflow where data enters the system.Alert Processing
The Alert Processing phase extracts key observables from raw alert data using predefined templates in the Alert Templates Table. The system checks whether each alert has already been processed and flags unprocessed alerts for further attention, ensuring efficient and accurate data handling.Enrichments
The Enrichment process is designed to enrich and maintain the enrichment of observables. This phase is fully customizable for each customer, allowing adjustments based on their specific toolset and preferred enrichment methods. It consists of vendor-specific subflows, which can be selected or tailored per client.Response
The Response process is designed to automate the response process for cases. This phase can be fully customized to suit each customer’s specific tools and preferred workflows.Flow Diagram Showing the Case Management Automated Processes
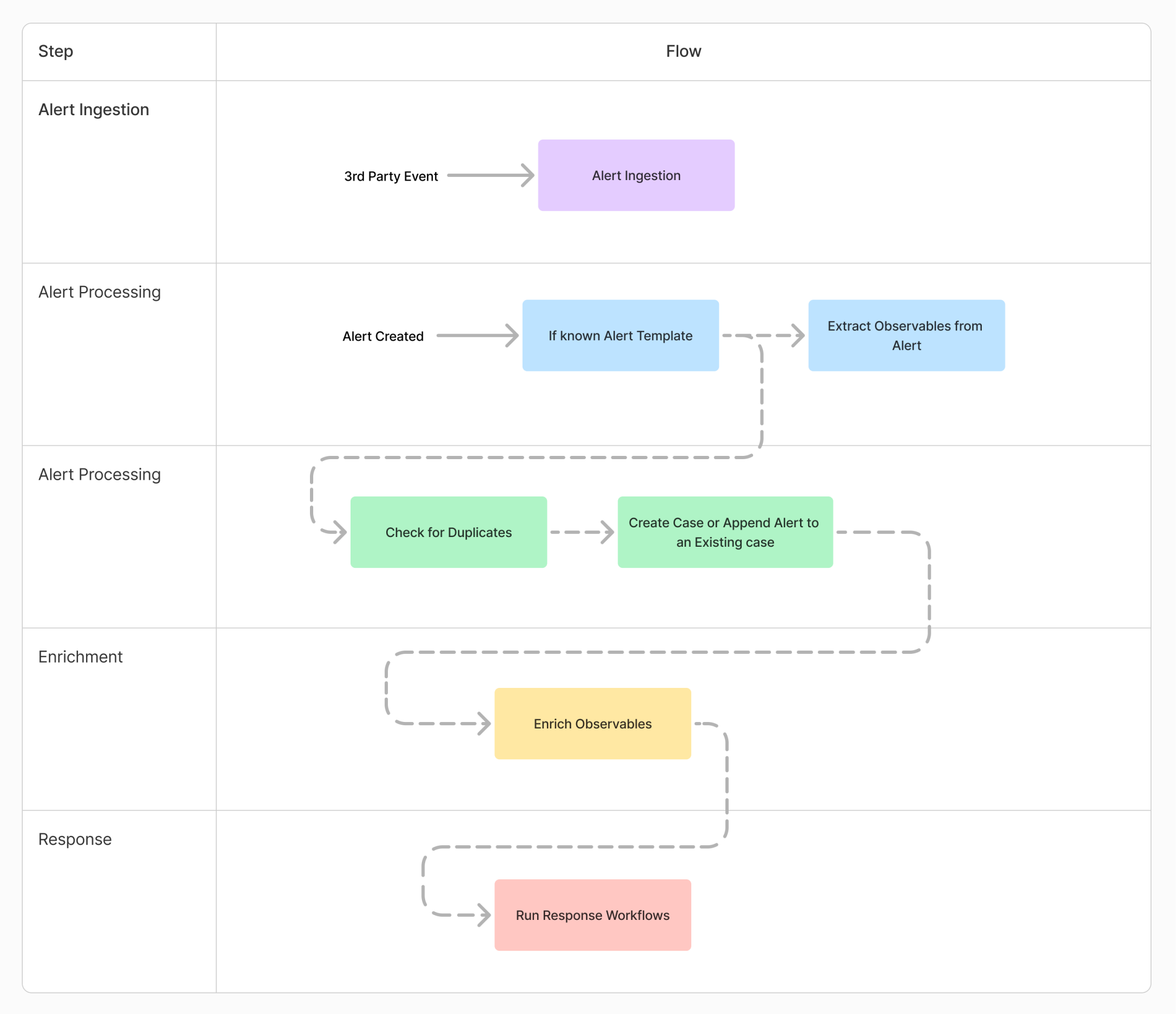
Detailed Guide of Flow Diagram
This guide provides an in-depth explanation of how Blink handles alert and case processing, offering insights into each stage of the workflow, associated subflows, data transformations, and examples for testing.1. Alert Ingestion
- Description: This is the entry point where Blink ingests events from third-party systems or monitoring tools.
- How It Works:
- Events are received via APIs, webhooks, or file-based ingestion methods.
- Blink normalizes and stores the raw data to make it compatible with the workflow engine.
- Data Example:
2. Alert Processing
- Description: Once an alert is created, Blink identifies whether it matches a known alert template and extracts observables for further processing.
- How It Works:
- Templates contain pre-defined rules or patterns to categorize alerts (e.g., by severity, source, or type).
- Observables such as IP addresses, file hashes, or user IDs are extracted for enrichment.
- Example Template Match:
- Extracted Observables:
3. Alert Processing: Dedup Check
- Description: Blink checks for duplicate alerts and either creates a new case or appends the alert to an existing one.
- How It Works:
- A hash or unique identifier is generated for each alert to detect duplicates.
- If duplicates are found, the alert is appended to an existing case for context.
- If no duplicates are detected, a new case is created, associating relevant observables and metadata.
- Data Transformation Example:
- Input Alert:
- Generated Case:
- Input Alert:
4. Enrichment: Observable Enrichment
- Description: Observables are enriched with additional context from internal or external sources.
- How It Works:
- Blink queries threat intelligence platforms, databases, or internal systems to gather more information about observables.
- Examples of enrichment include geolocation data for IP addresses or reputation scores for domains.
- Enrichment Example:
- Input Observable:
- Enriched Data:
- Input Observable:
5. Response: Execute Response Workflows
- Description: Blink triggers automated workflows to respond to the alert.
- How It Works:
- Workflows include actions such as blocking an IP, disabling a user account, or notifying a security team.
- Response steps are configured based on the severity and type of the alert.
- Response Example:
- Triggered Action: Block IP address “192.168.1.1” via firewall.
- Workflow Execution Log:
Sample Data Flow
Input:
Output:
Example of Case Management Workspace and the Automated Workflow’s Processes