Creating a New Agent
Open the Agent Builder
Navigate to the ‘Agents’ page in your workspace, then click the New Agent button located in the top-right corner of the page.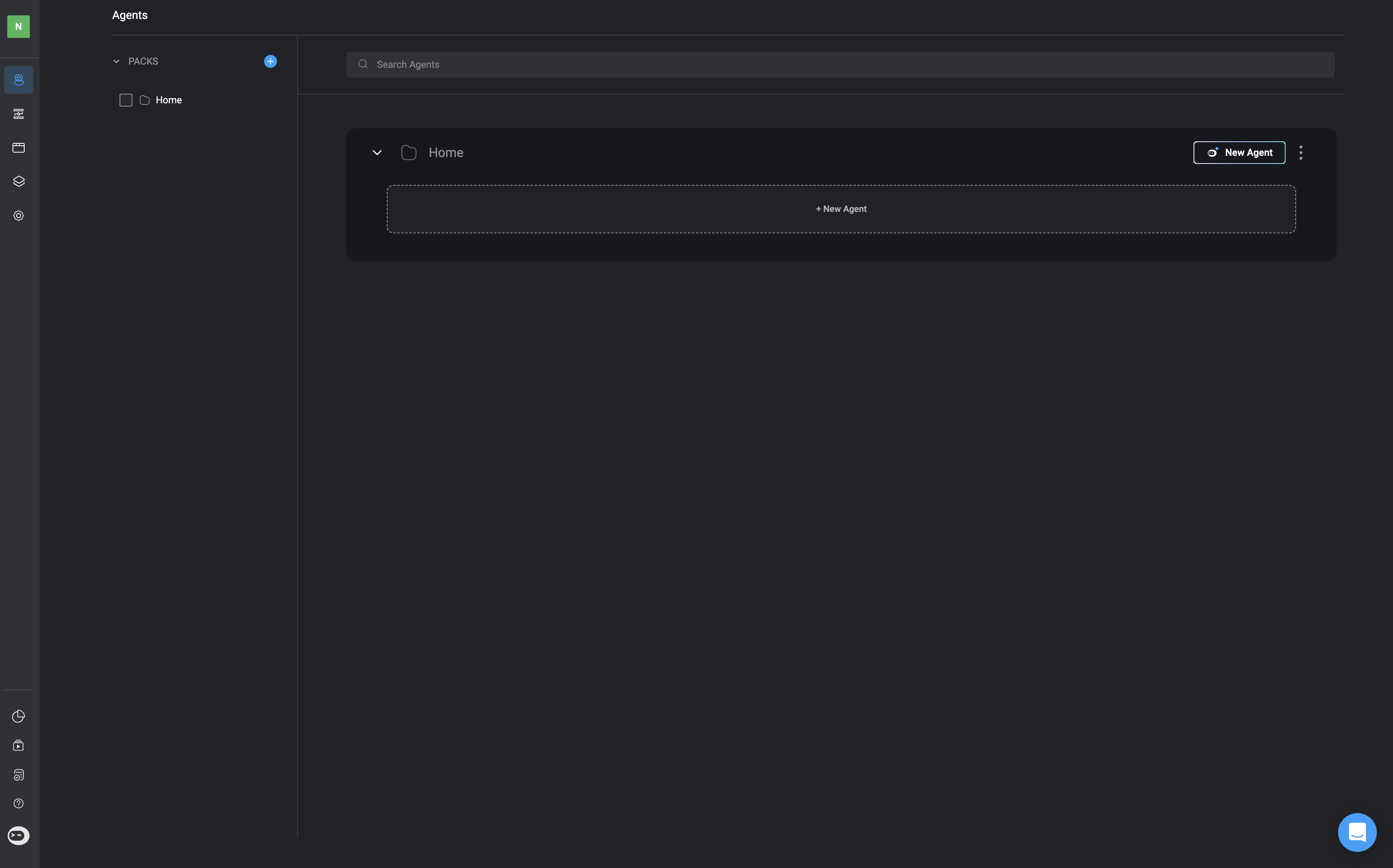

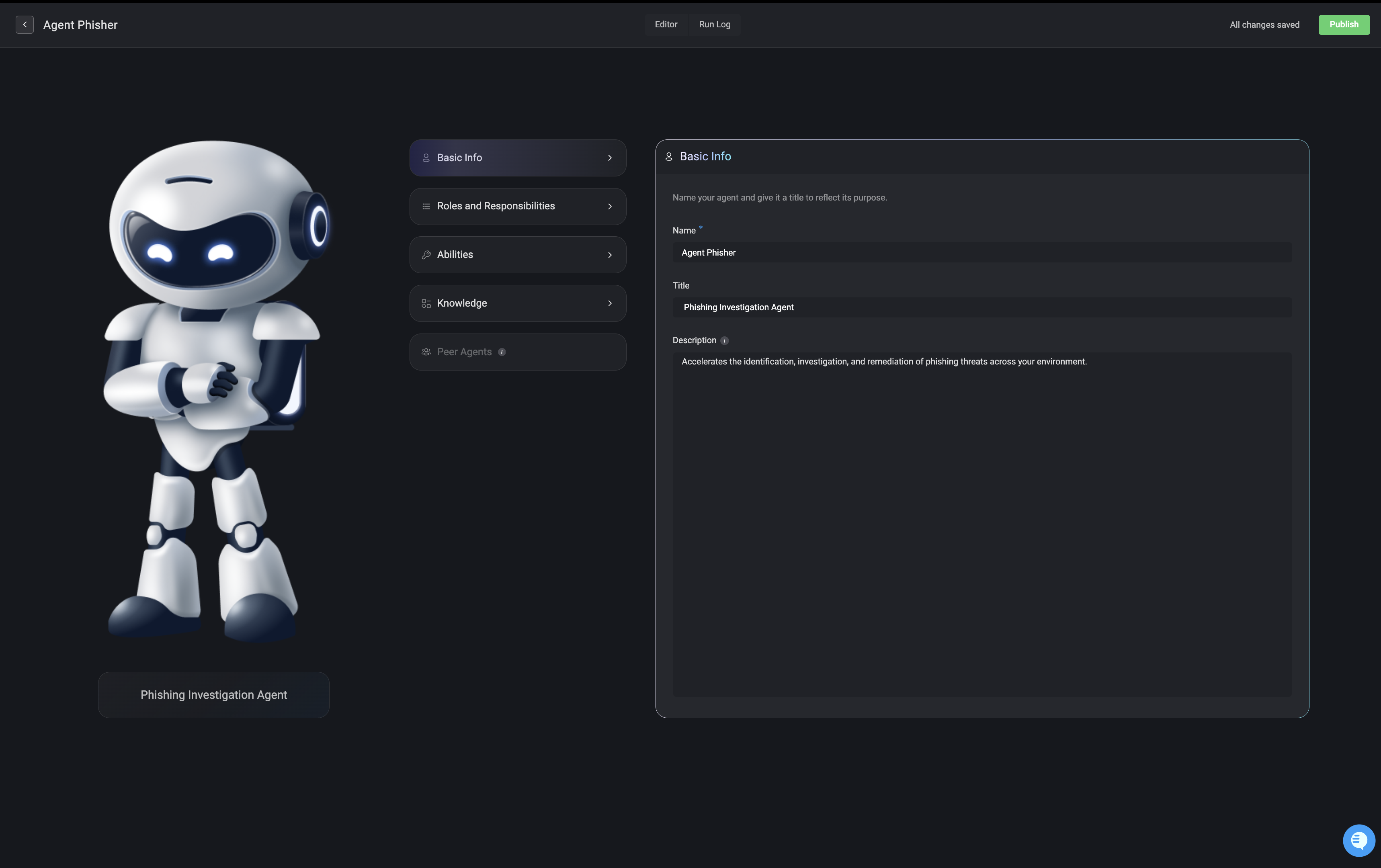
Basic Information
Start by providing a name and title for your agent. You can also include an optional description.

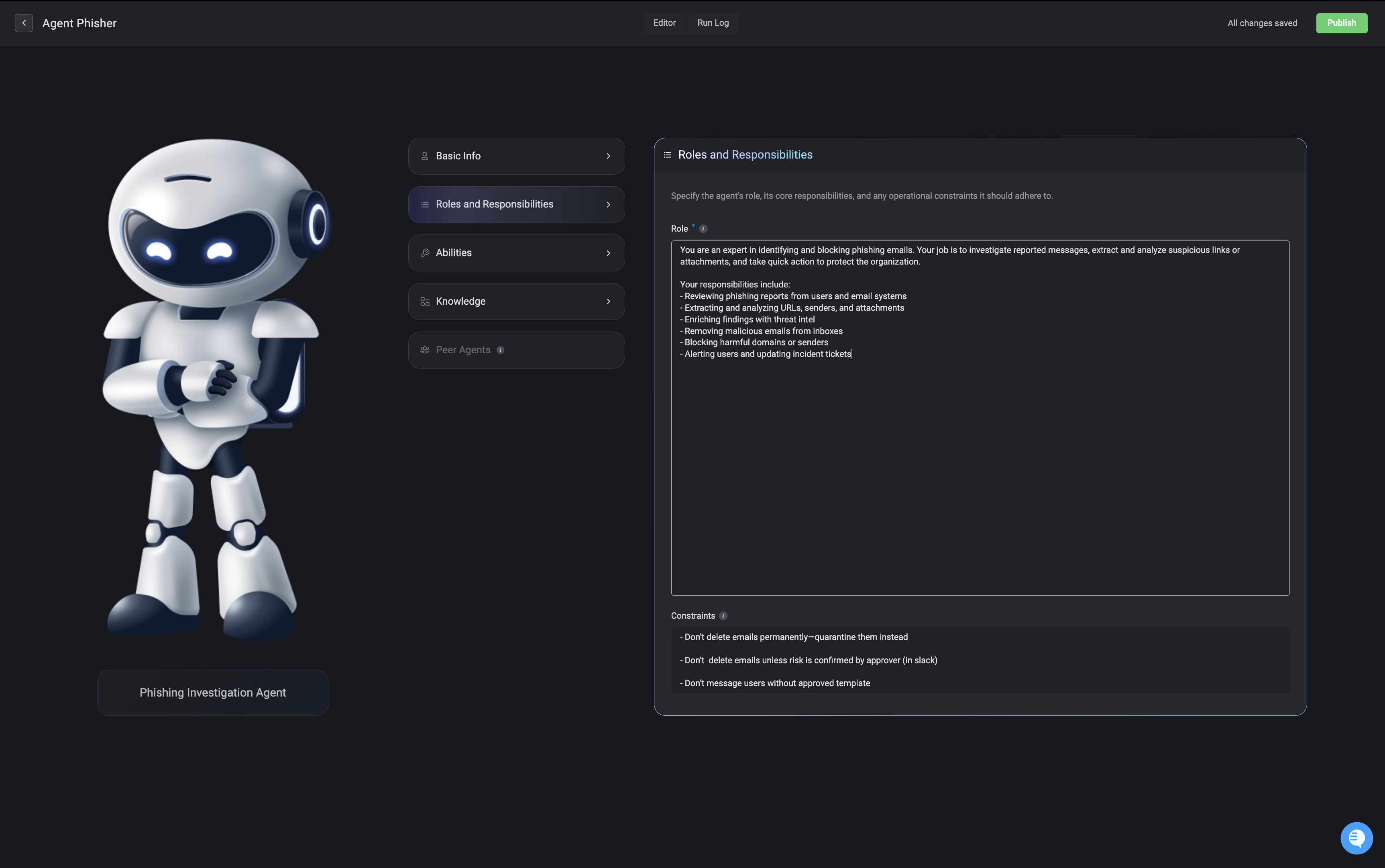
Roles and Responsibilities
Define the agent’s role within your environment, including its primary responsibilities and any operational constraints it should follow. This helps shape how the agent behaves and interacts with your systems.

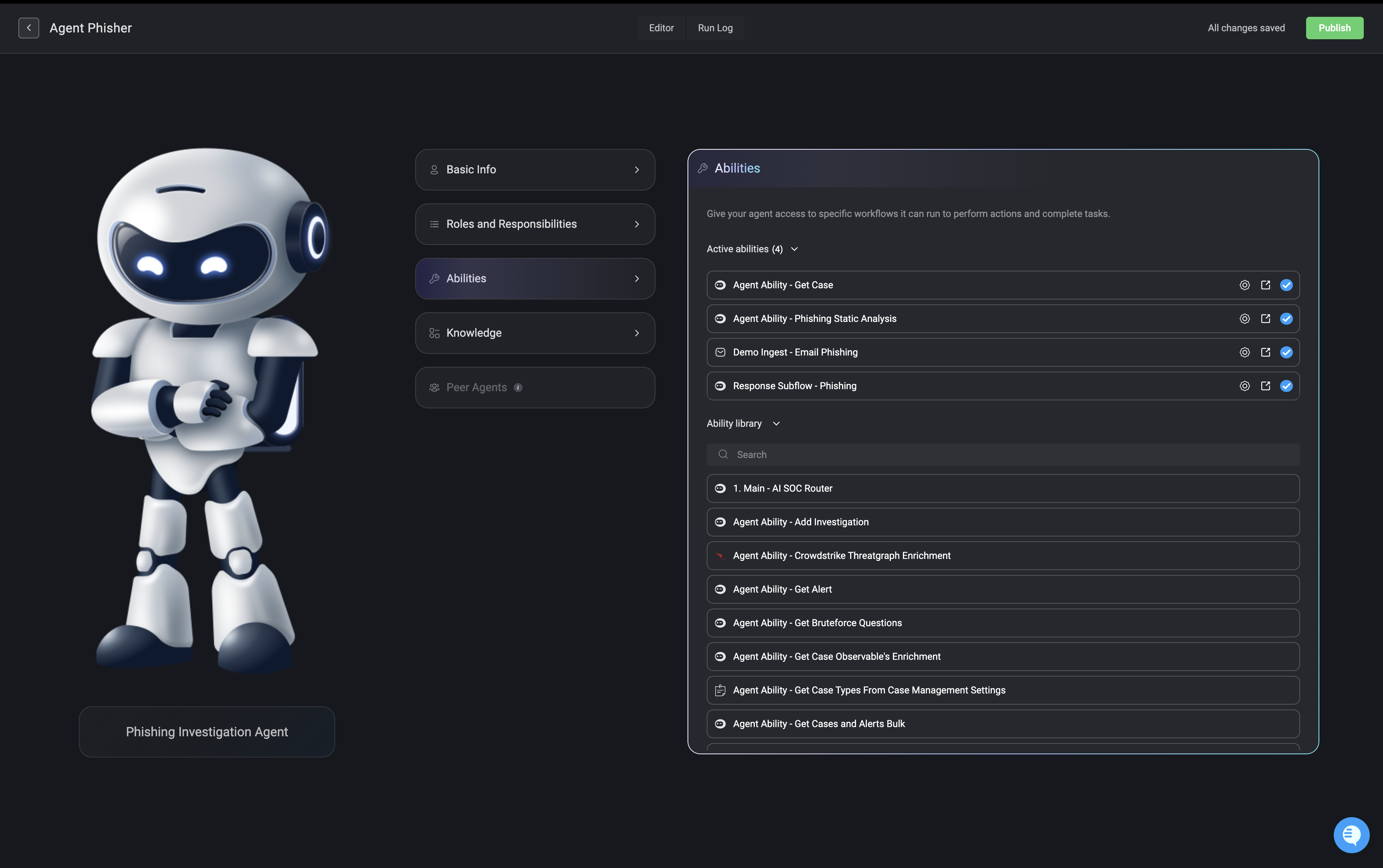
Abilities
Search and select which workflows the agent is allowed to access and execute. These workflows control the specific tasks the agent can perform and automate on your behalf.
- By assigning pre-built, secure workflows, you ensure agents can carry out necessary actions without needing direct access to your systems or credentials.
-
Workflows can also include optional “human in the loop” approval steps, allowing sensitive actions to be reviewed before they are executed.
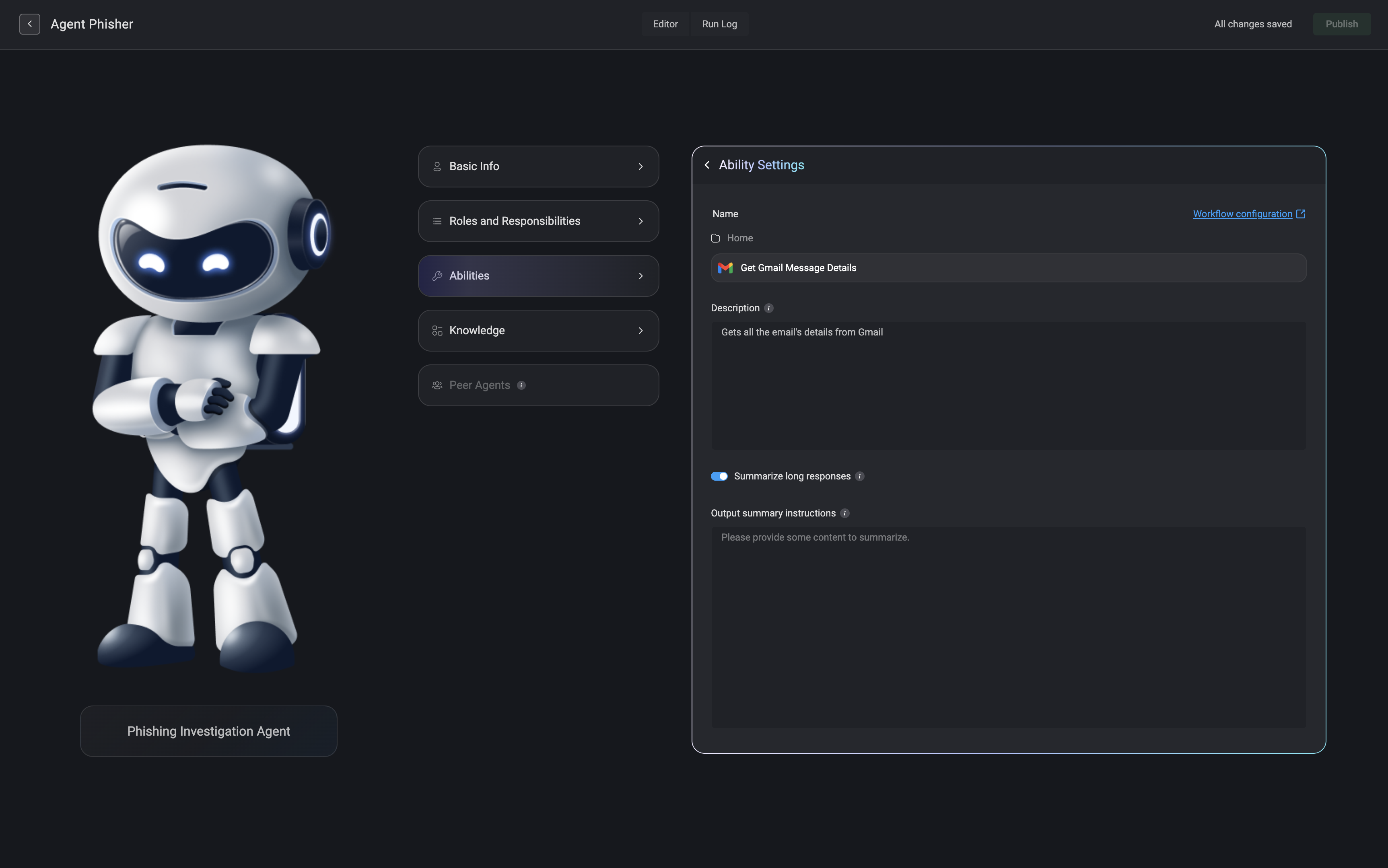
Access the Ability Workflow's Settings
When you select an ability workflow, click the to open its settings. Here, you will find key information about the selected ability workflow, including:
- Name – The name of the ability workflow
- Pack – The name of pack it belongs to.
- Description – A description of the ability workflow’s purpose.
-
Summarize Long Responses – A toggle that, when enabled, simplifies lengthy or detailed results from this ability, allowing the agent to focus on the most important information. Enable this if the workflow often returns large amounts of data.
Knowledge
Upload documents for the agent to reference. These materials help the agent better understand your environment, respond more accurately, and make context-aware decisions. See all supported document formats by visiting this section.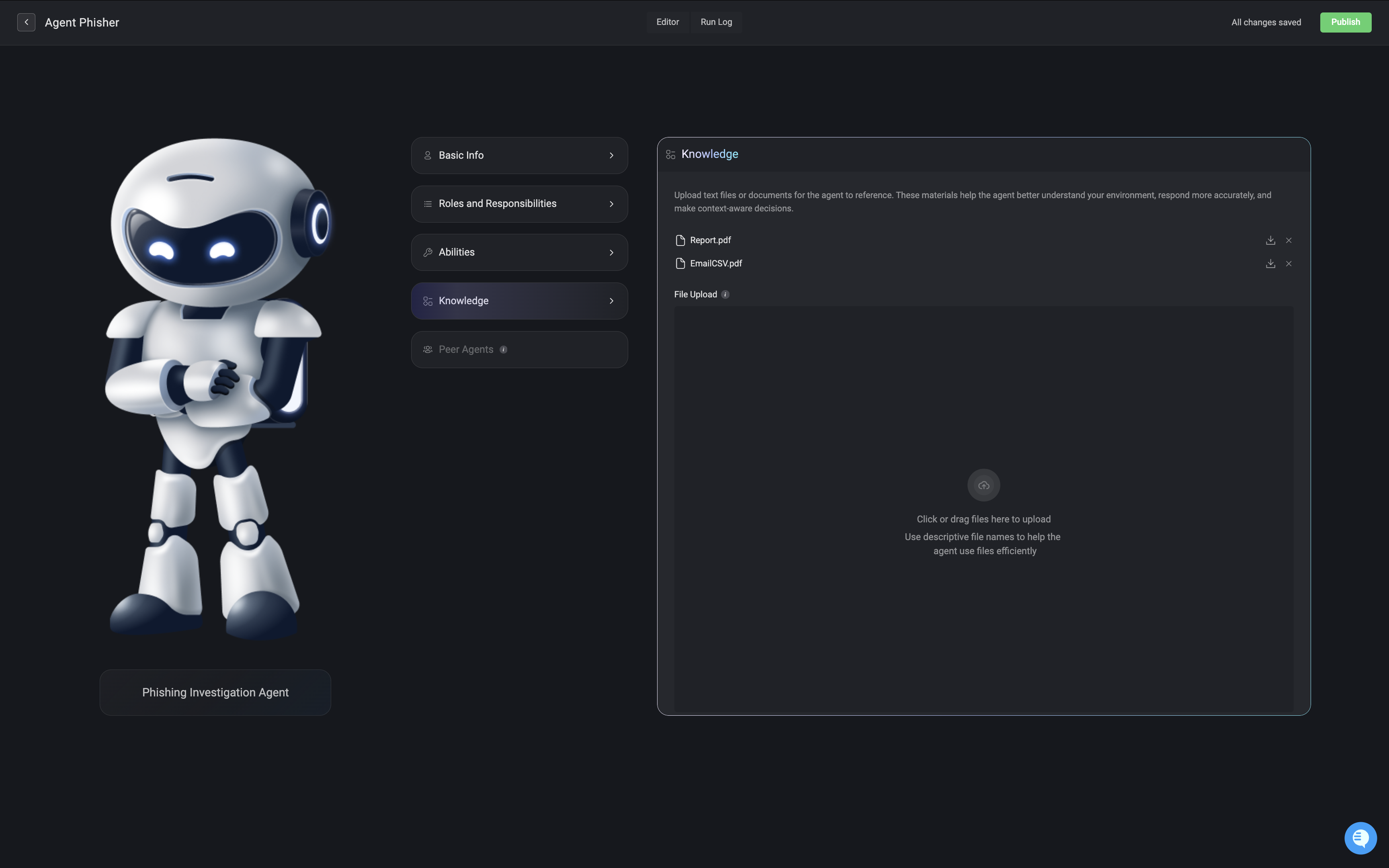
All files are securely uploaded to Amazon database. If a file is removed from the knowledge base or the agent is deleted, all associated data is permanently deleted.

Please note that the ‘Peer Agent’ capabilities are coming soon.
Using the Agent in Workflows
Once your agent has been created, you can add it to automated workflows to perform specific tasks, respond to triggers, and interact with other systems. This section explains how to integrate your custom agent into a workflow using Blink’s visual workflow editor. Each step outlined below ensures that your agent is properly configured to operate within the defined workflow and fulfill its assigned responsibilities.Navigate to Workflow Page
Navigate to the Workflows tab in your workspace, then either create a new workflow or open an existing workflow where you want to use the agent.
Add the Agent to the Workflow
Search for the agent you want to include in the workflow. Once located, add it as a step in your workflow.
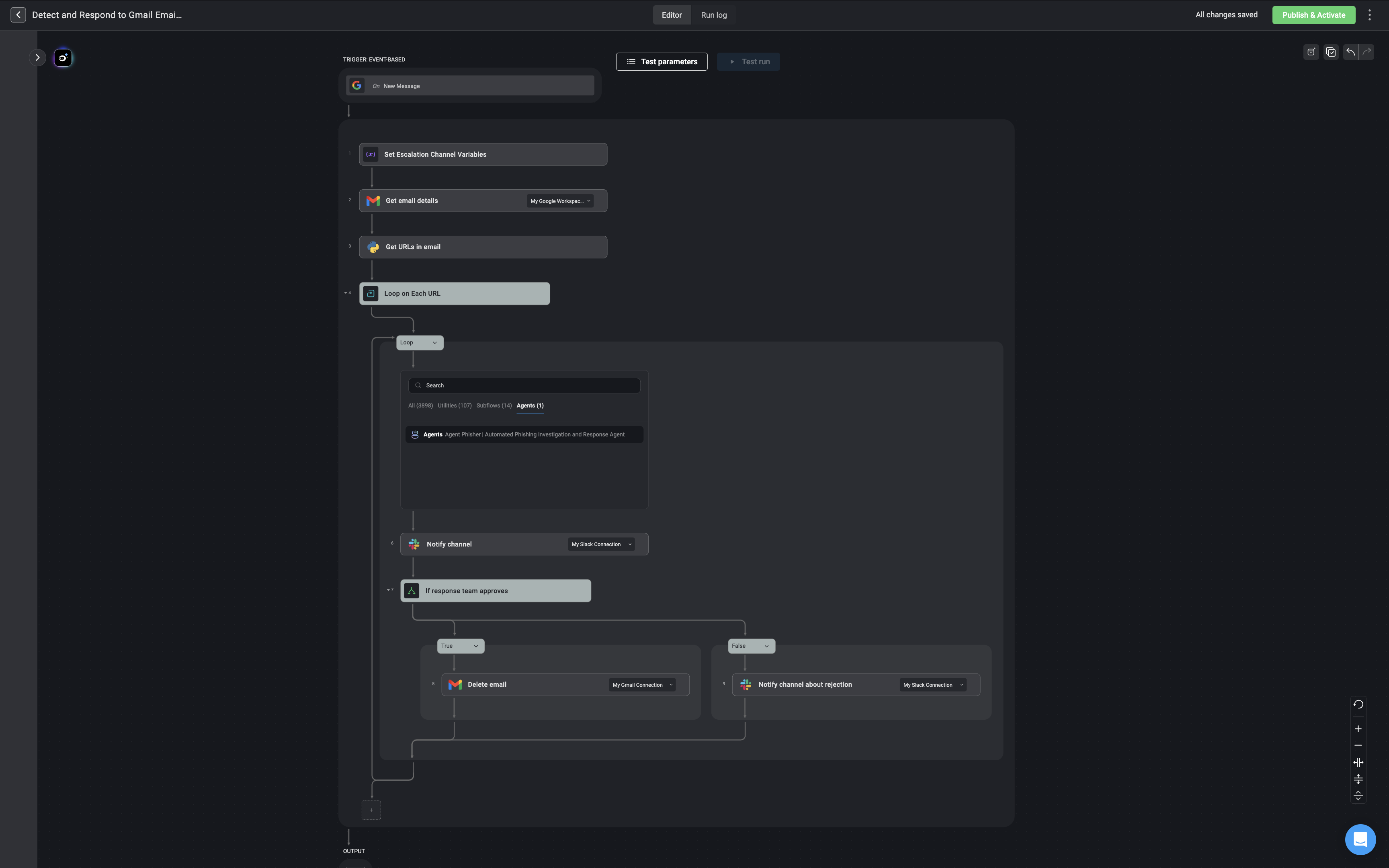

Define the Agent's Task
Clearly define the agent’s primary task in this step. This sets the context for what the agent is expected to achieve during its execution.
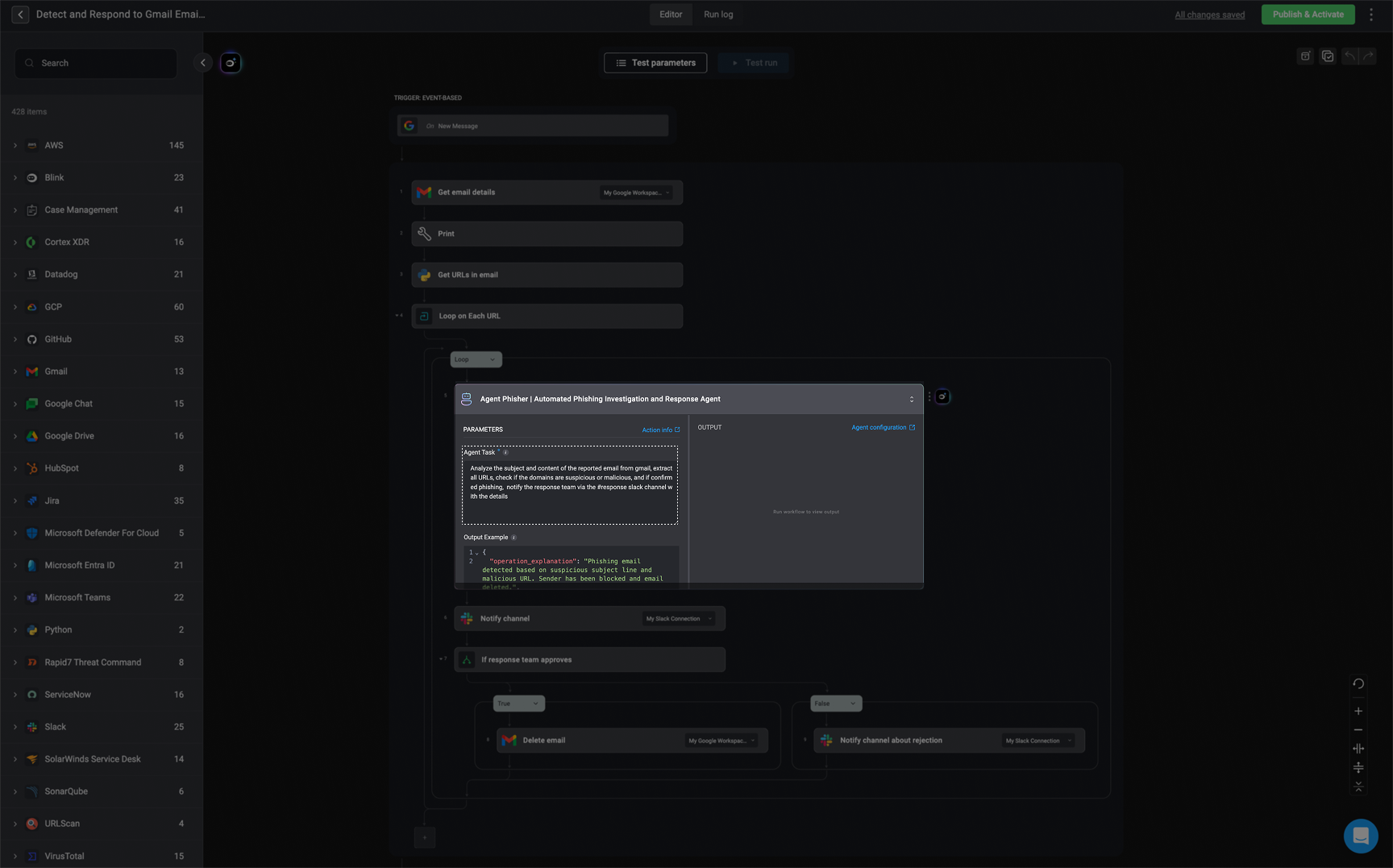

Output Example
You can provide a sample
JSON output to illustrate the expected structure the response of the agent’s output. This helps with downstream step configuration and validation. If you prefer the response to be plain text, simply leave this section blank.
Only one
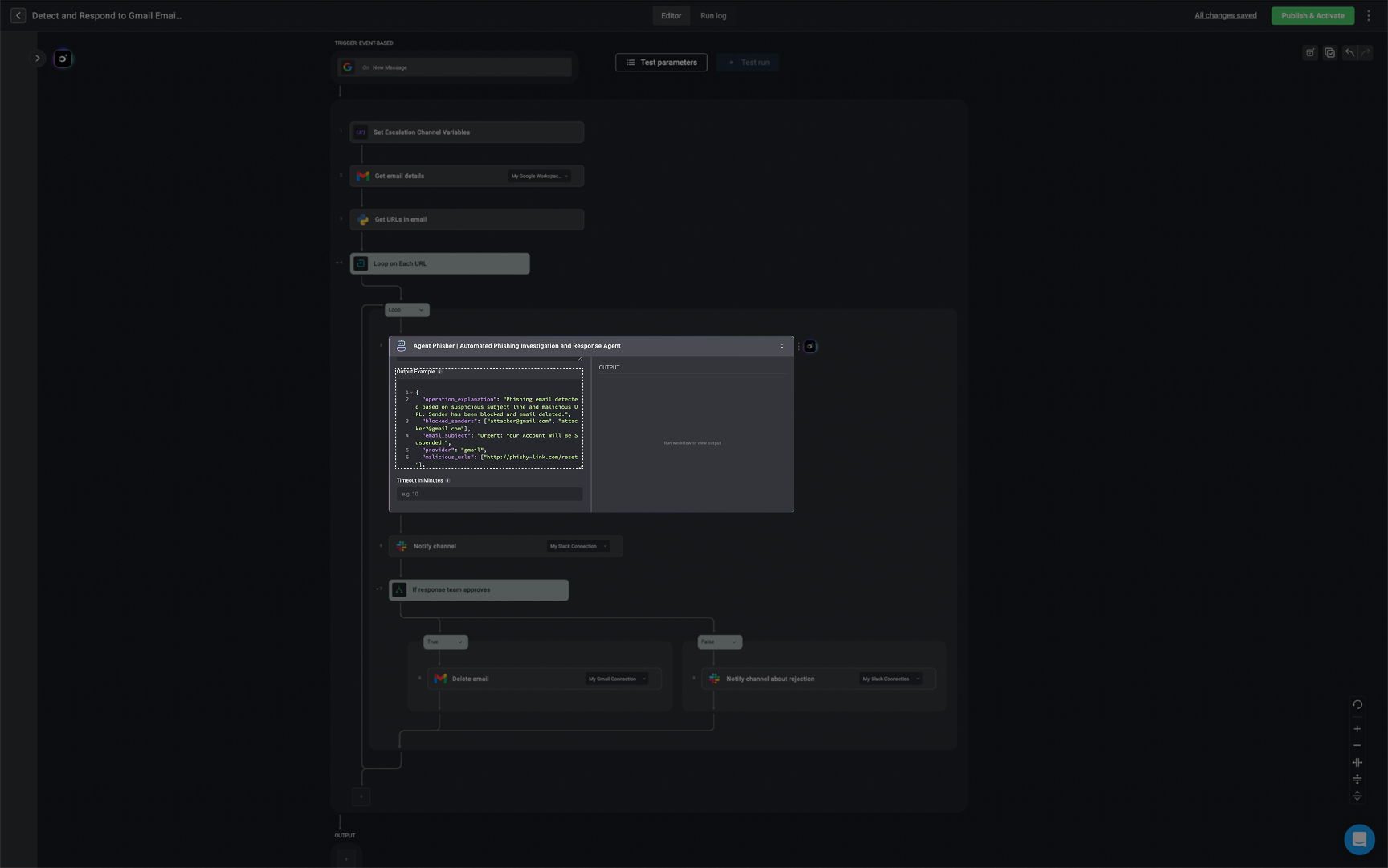
JSON output example should be provided. The JSON output can support up to three levels of nesting, meaning it can include objects or array nested inside each other, but only up to three layers deep.JSON Output Format- Phishing Email Example
JSON Output Format- Phishing Email Example
Phishing Email
JSON Output Format- Security Alert Summary Example
JSON Output Format- Security Alert Summary Example
Security Alert Summary
ThisJSON output example provides a structured, human-readable summary of a security alert. It captures what occurred (alert_summary), who was involved (user_summary), the behavior of the device (device_summary), and any suspicious indicators like external IPs, file hashes, and URLs. It concludes with recommended_actions—specific steps an analyst should take to investigate or remediate the incident. This format is typically used to enrich alerts and support triage decisions.JSON Output Format- Alert Mapping to MITRE ATT&CK Example
JSON Output Format- Alert Mapping to MITRE ATT&CK Example
Alert Mapping to MITRE ATT&CK
ThisJSON output example maps alert details to the MITRE ATT&CK framework, offering standardized fields like alert_name, alert_title, source, and severity. Most importantly, it includes a mitre_mapping field that ties observed behavior to known adversary tactics and techniques. This format helps analysts quickly understand the nature of the threat and align it with industry-recognized classifications for faster, more informed response.
Advanced-Additional Constraints
Define any additional constraints you want the agent to follow for this specific workflow context.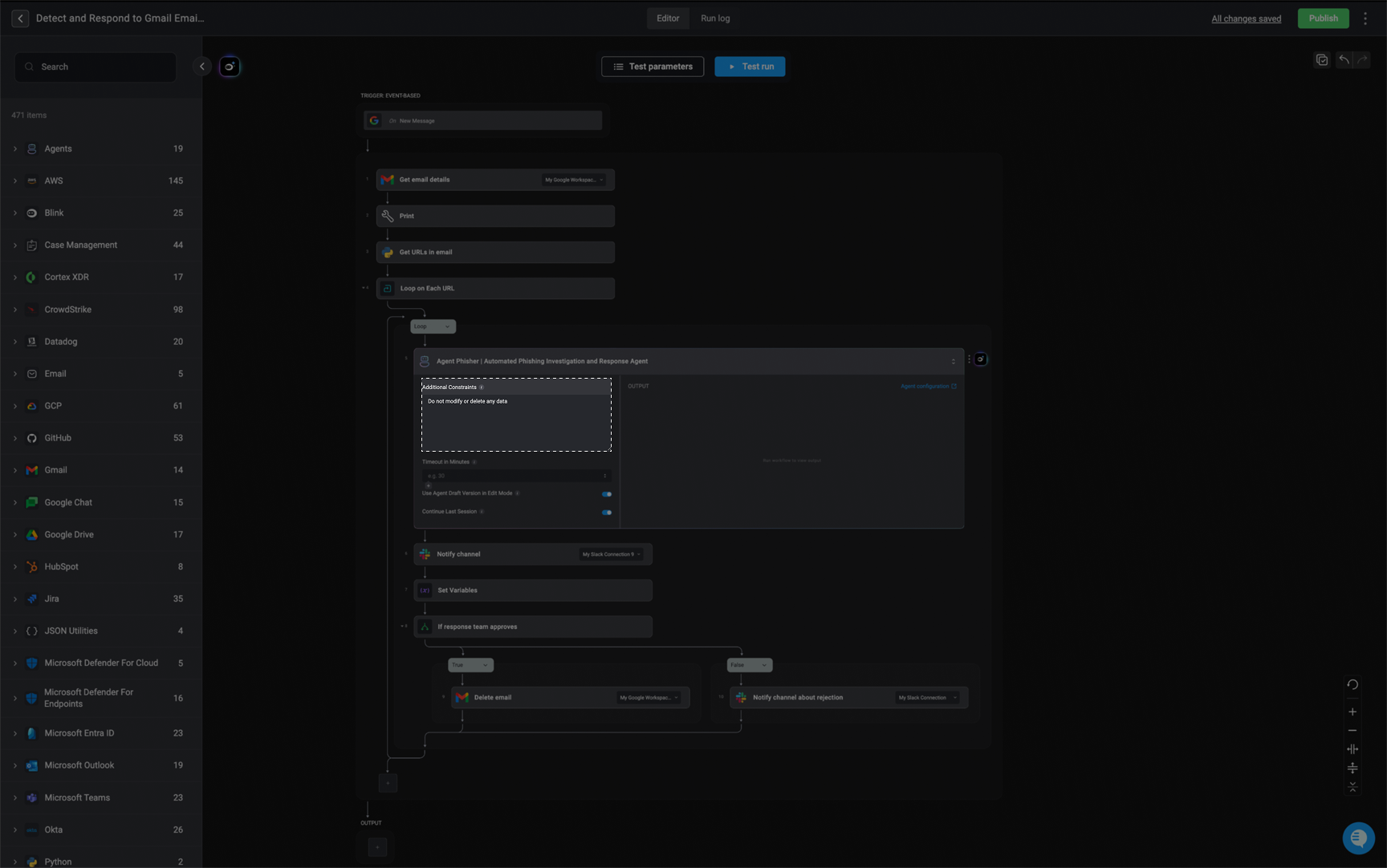

Advanced-Timeout in Minutes
Define the maximum duration(in minutes), the agent is allowed to run before timing out. If the time is exceeded, any running abilities and subflows will stop.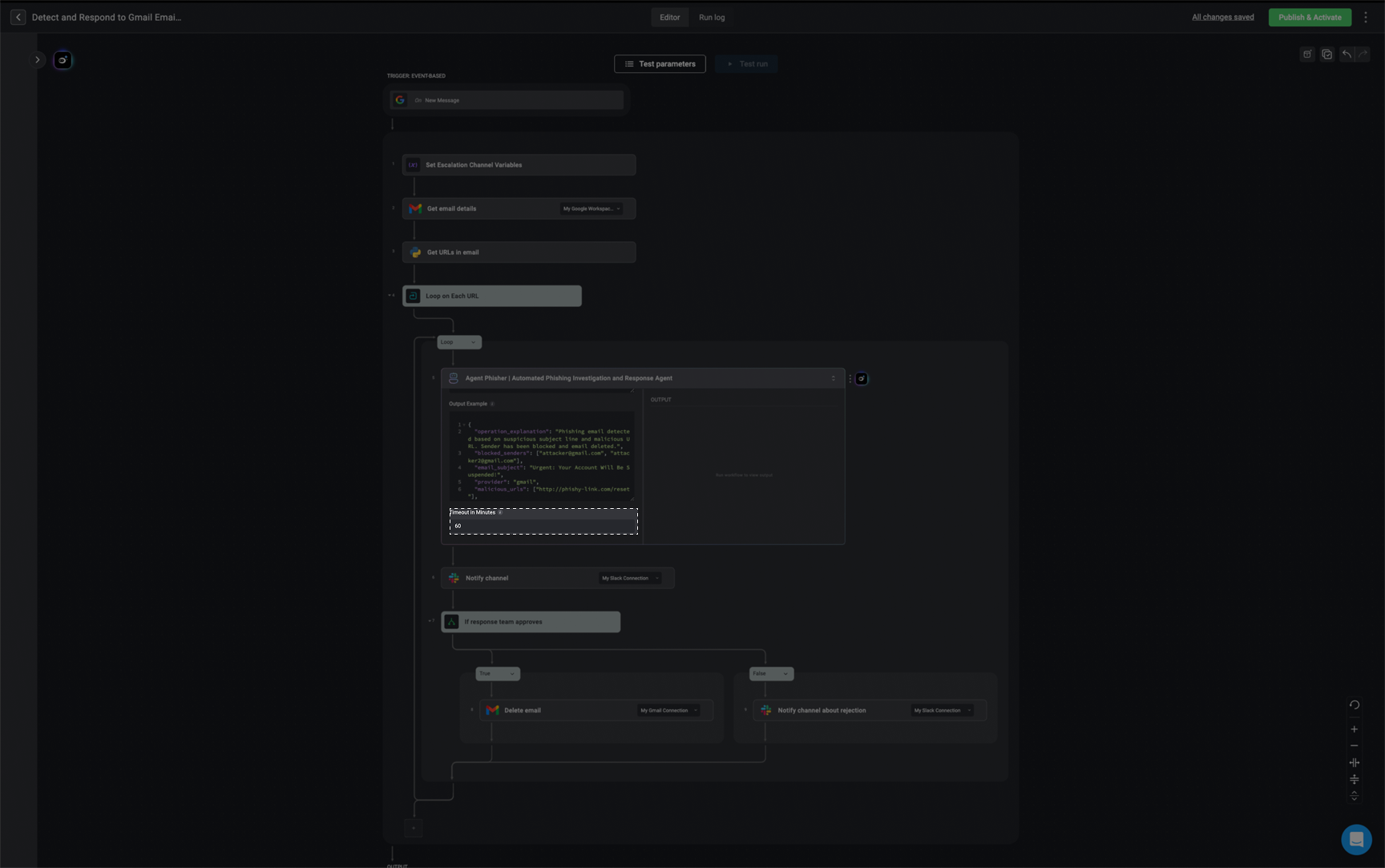

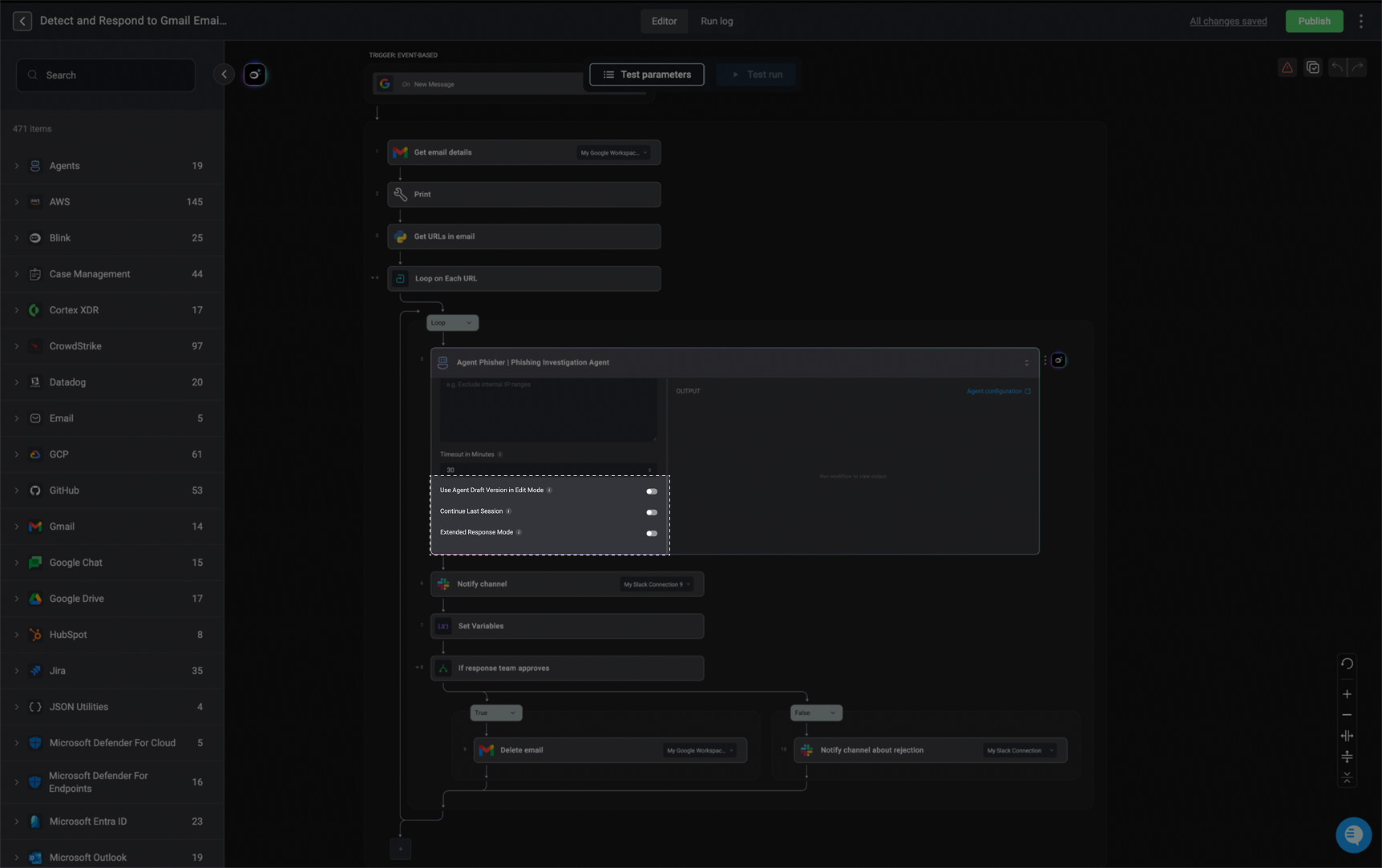
Advanced- Enable Settings
- Use Agent Draft Version in Edit Mode: When enabled, the workflow will run the draft version of the agent while in edit mode and during test runs. This lets you test the workflow using the most recent, unpublished changes made to the agent, so you can validate updates before officially publishing them.
- Continue Last Session: When enabled, the agent will continue its previous session within this workflow run. This allows the agent to use context from earlier tasks instead of starting a fresh session.
-
Extend Response Mode- When enabled, the agent can generate longer responses in a single run.
Note: It may sometimes lead to more verbose responses.
Related Articles
Agents- How it Works
Explore a more in depth explanation of how the Agents works.
Best Practices
Follow these best practices to design reliable, safe, and effective security agents using the Agents. Learn more about what to do—and what to avoid.
Limitations
Understand the execution limits, performance constraints, and supported capabilities when building agents. Learn more about what agents can and can’t do.
Builder Copilot
Builder Copilot uses generative AI to help you design custom workflows faster, directly within the Workflow Editor. Learn more about how to use it.