Use Microsoft Sentinel to Trigger Workflows in Blink
Prerequisites
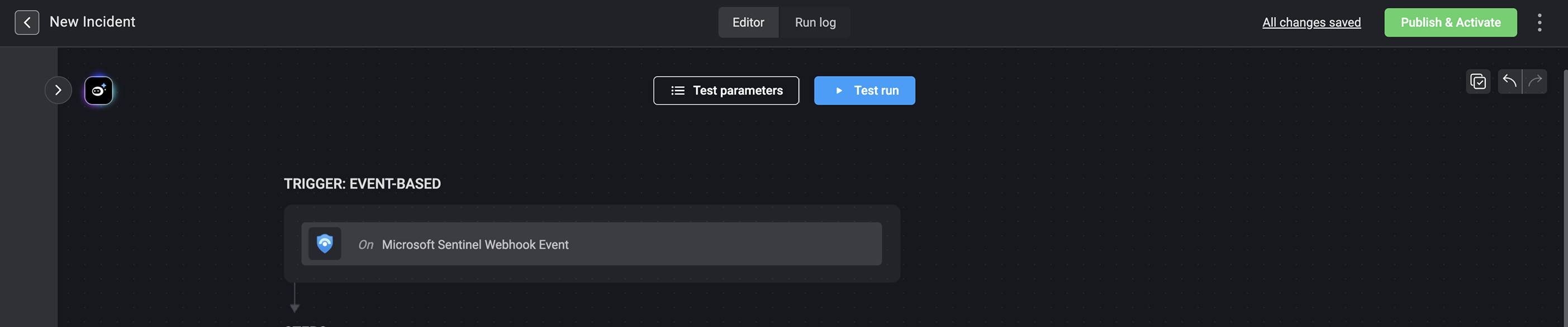
Create an Event-Based Workflow in Blink that is configured to trigger via webhook
- In your Blink workspace, use the left-hand menu to navigate to Workflows, then click New Workflow.
-
In the dialog box that opens, enter a name for your new workflow and set the Trigger Type to Event-based. Click Create Workflow.
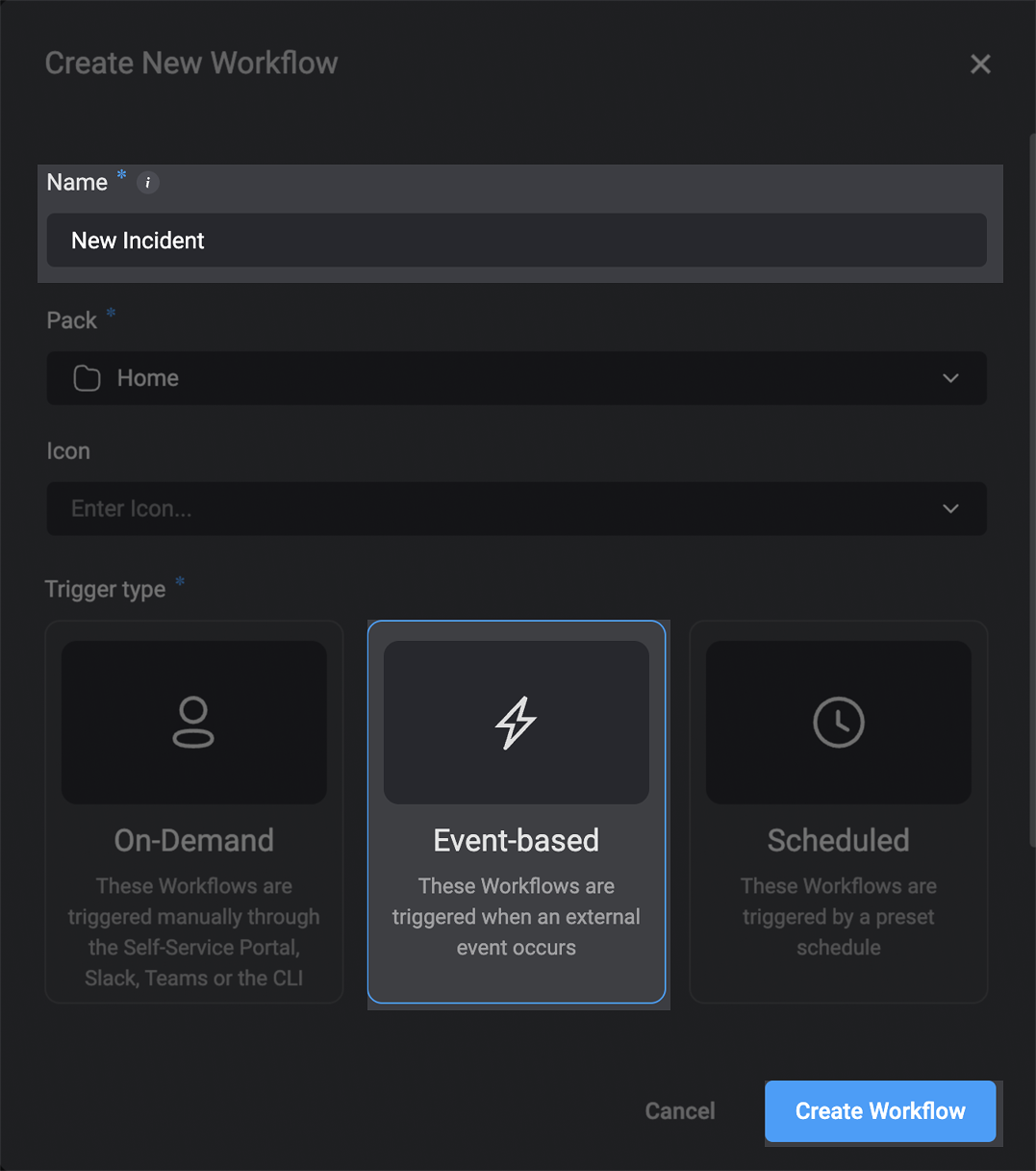
-
Click the event-based component in the new workflow.
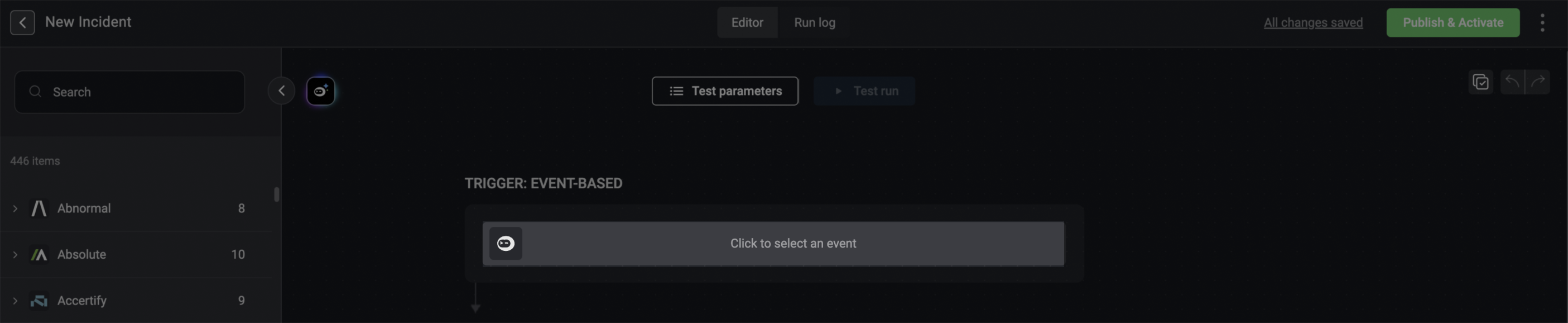
-
Search for Microsoft Sentinel trigger types and select Microsoft Sentinel Webhook Event.
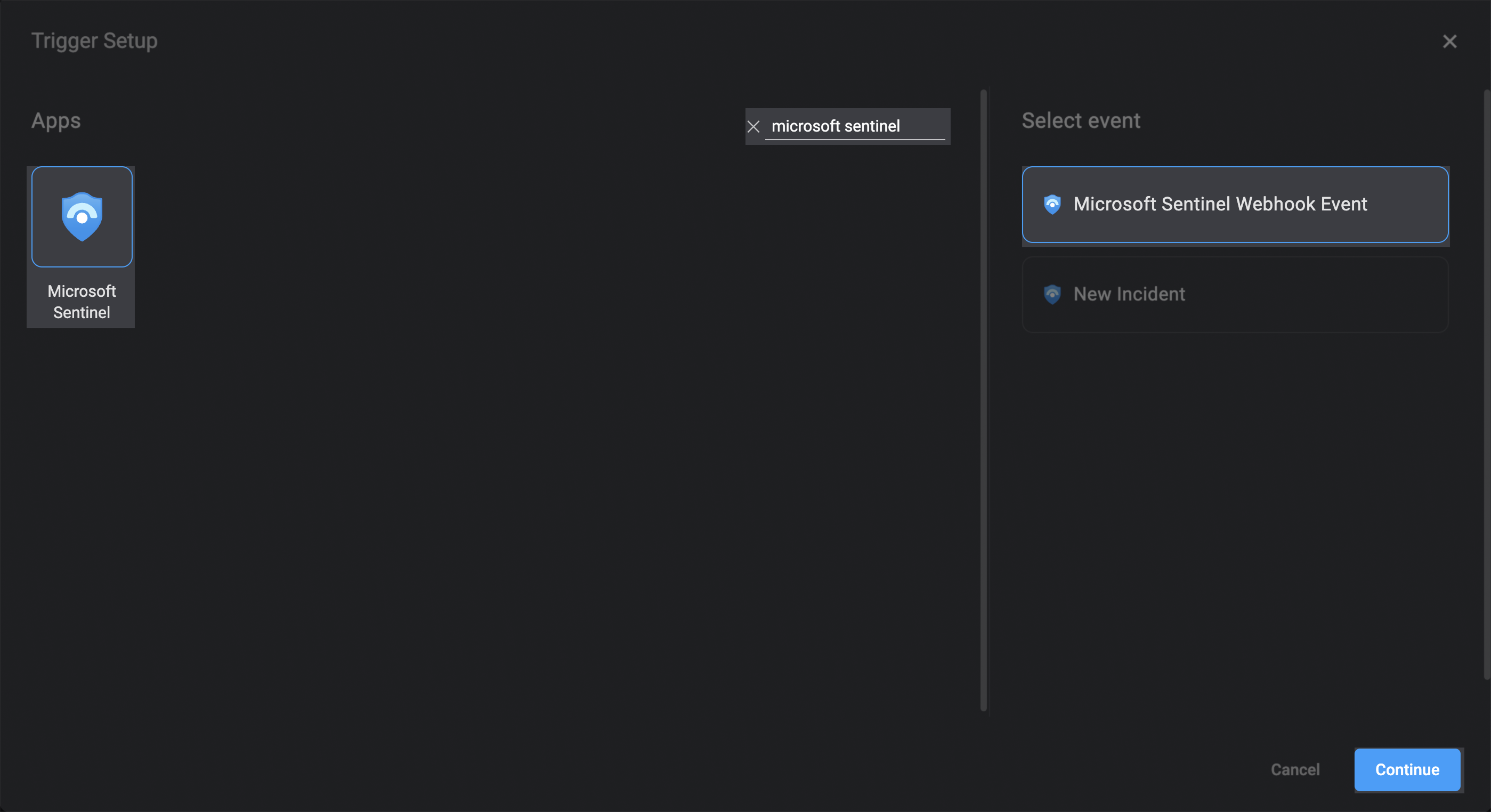
-
In the trigger setup dialog box, copy the Webhook Full URL address, and click Apply.
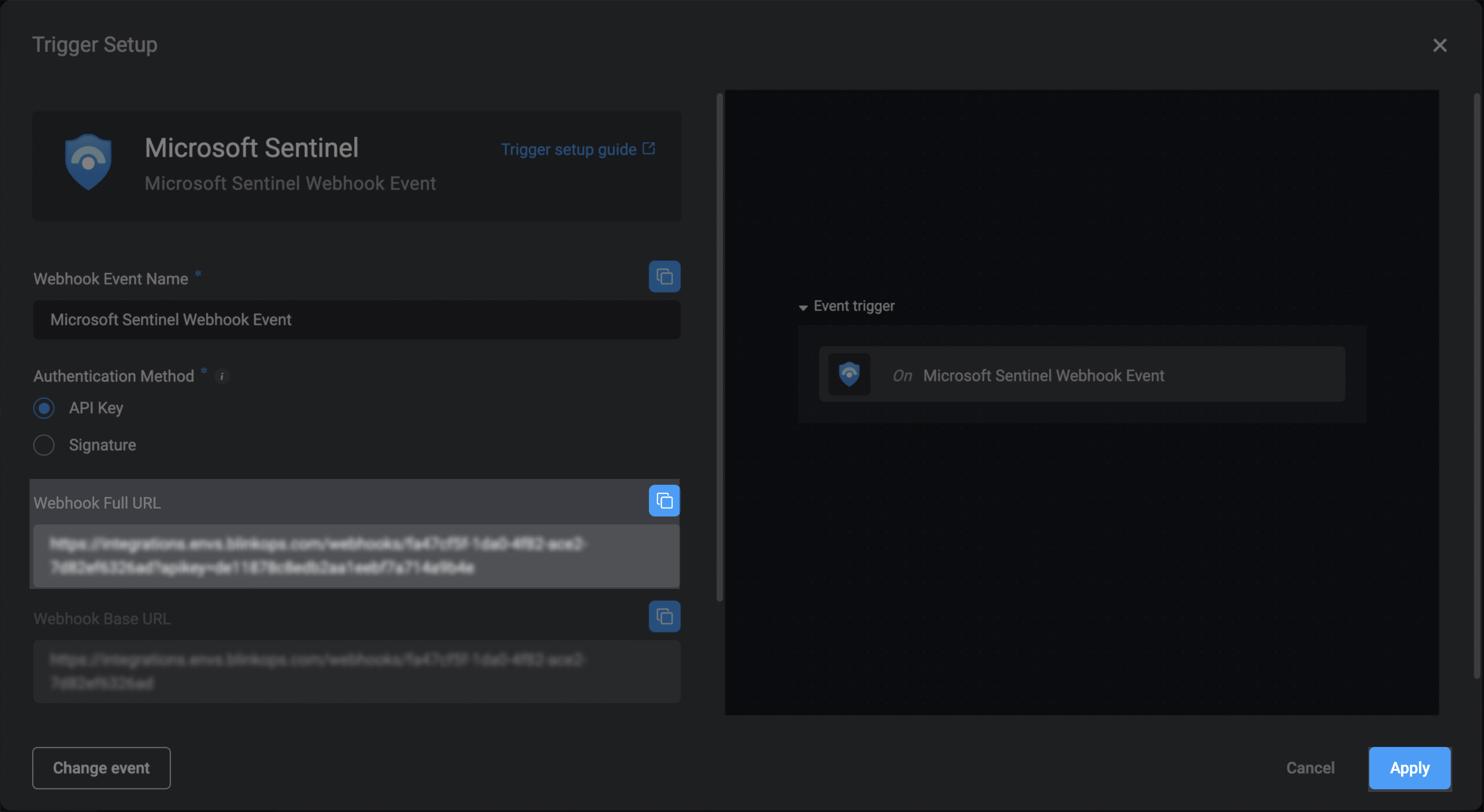
- Add steps to the new workflow to define the logic and actions that will run when the workflow is triggered.
-
Click Publish & Activate to start listening on events.
Add the Playbook from Sentinel’s Content Hub
-
In Microsoft Sentinel, use the left-hand menu to go to Content management > Content hub. Search for
Blinkin the search bar, select the displayed solution, and click Install.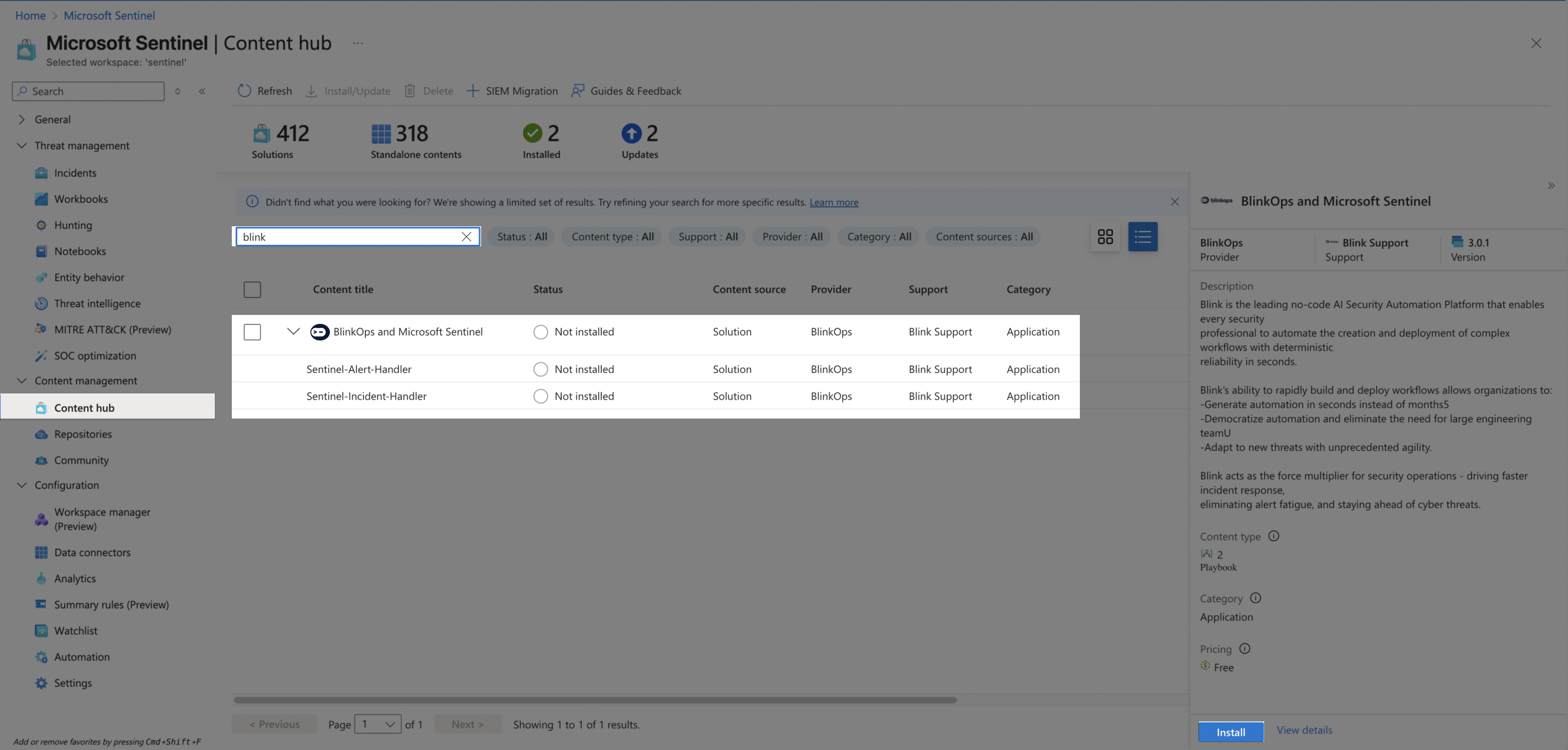
-
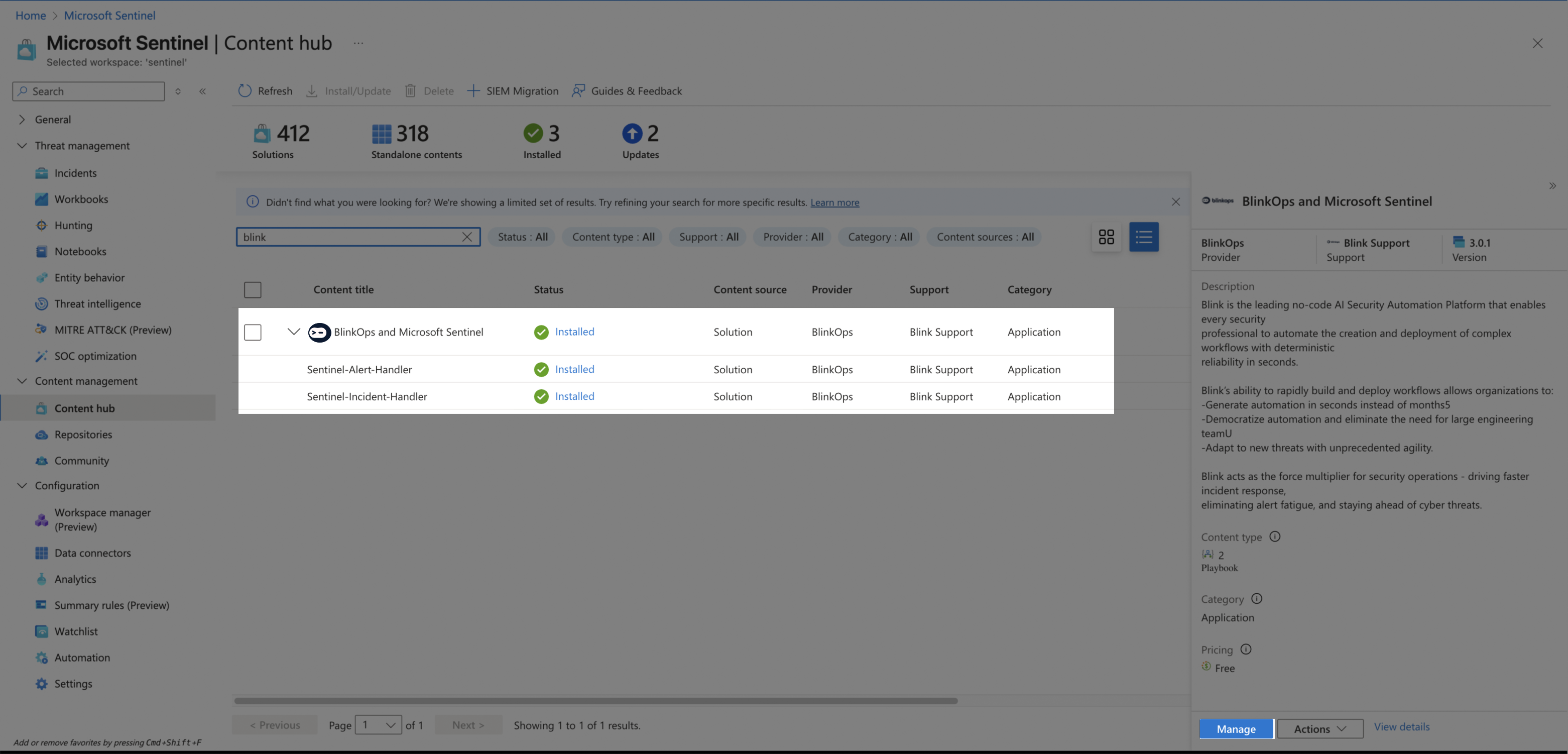
After the solution has been installed, click Manage.
-
Select the Playbook you want to add and click Configuration.
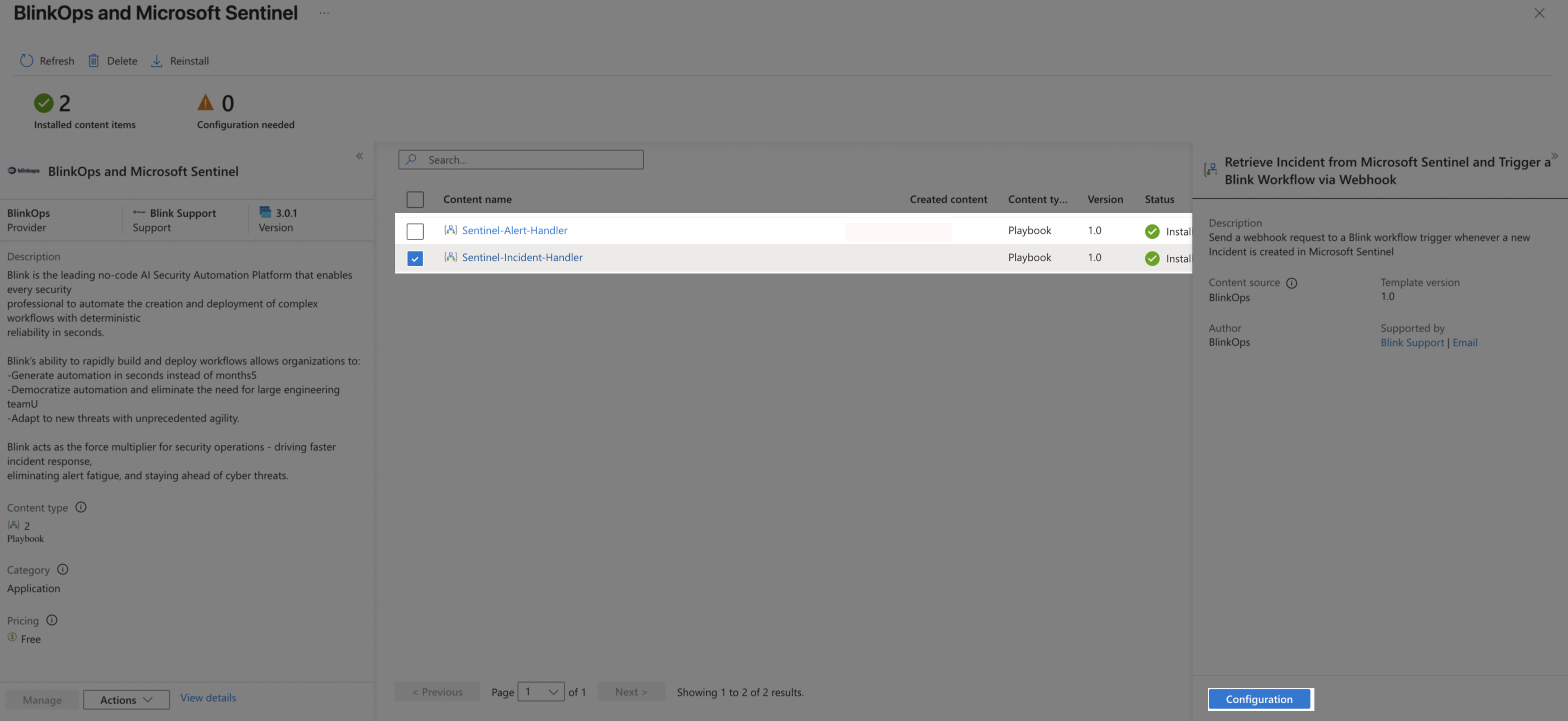
The following steps show how to create the Sentinel Incident Handler playbook. The same process applies to the Sentinel Alert Handler as well.
-
Click Create Playbook.
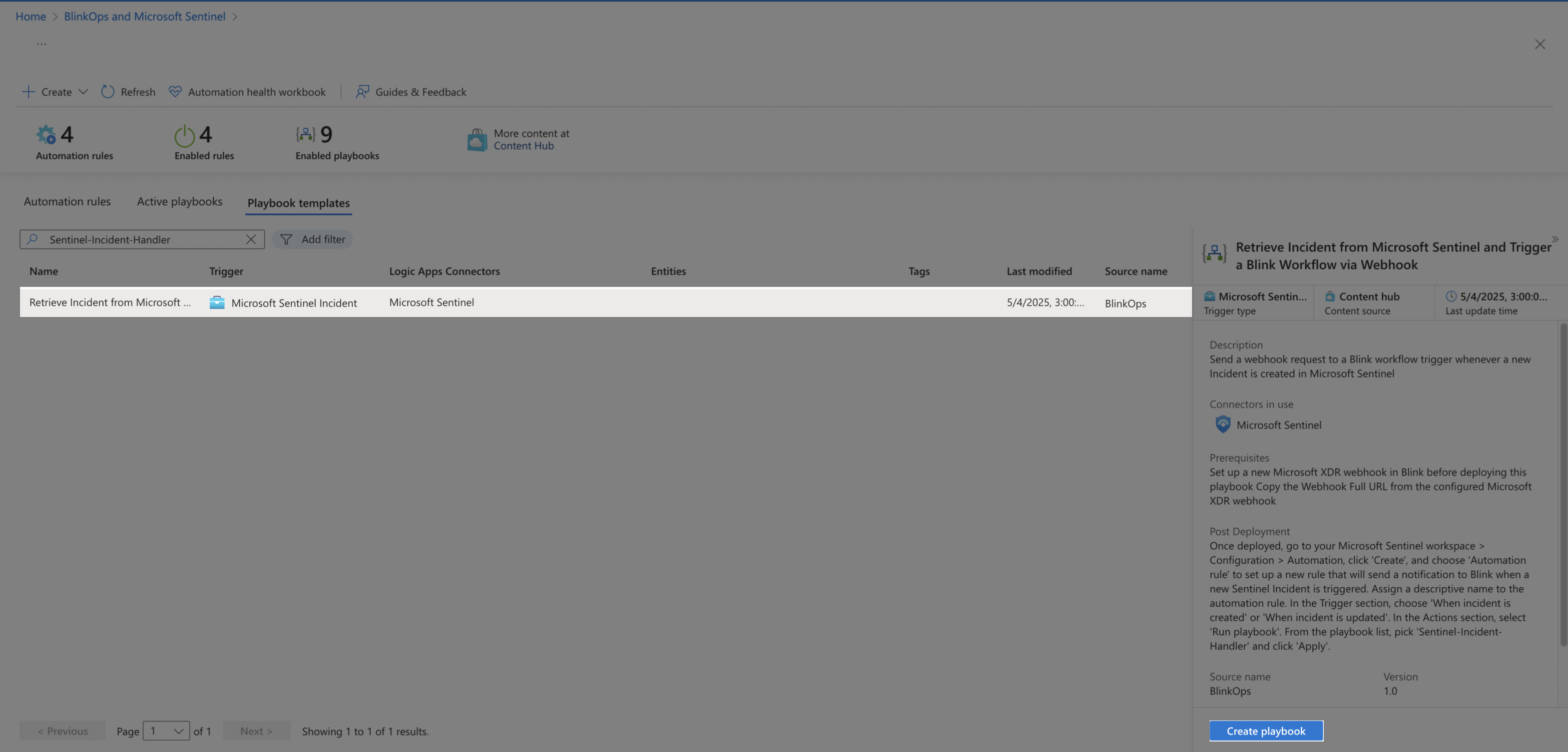
-
Insert Subscription and Resource group. Choose a name and click Next: Connections.
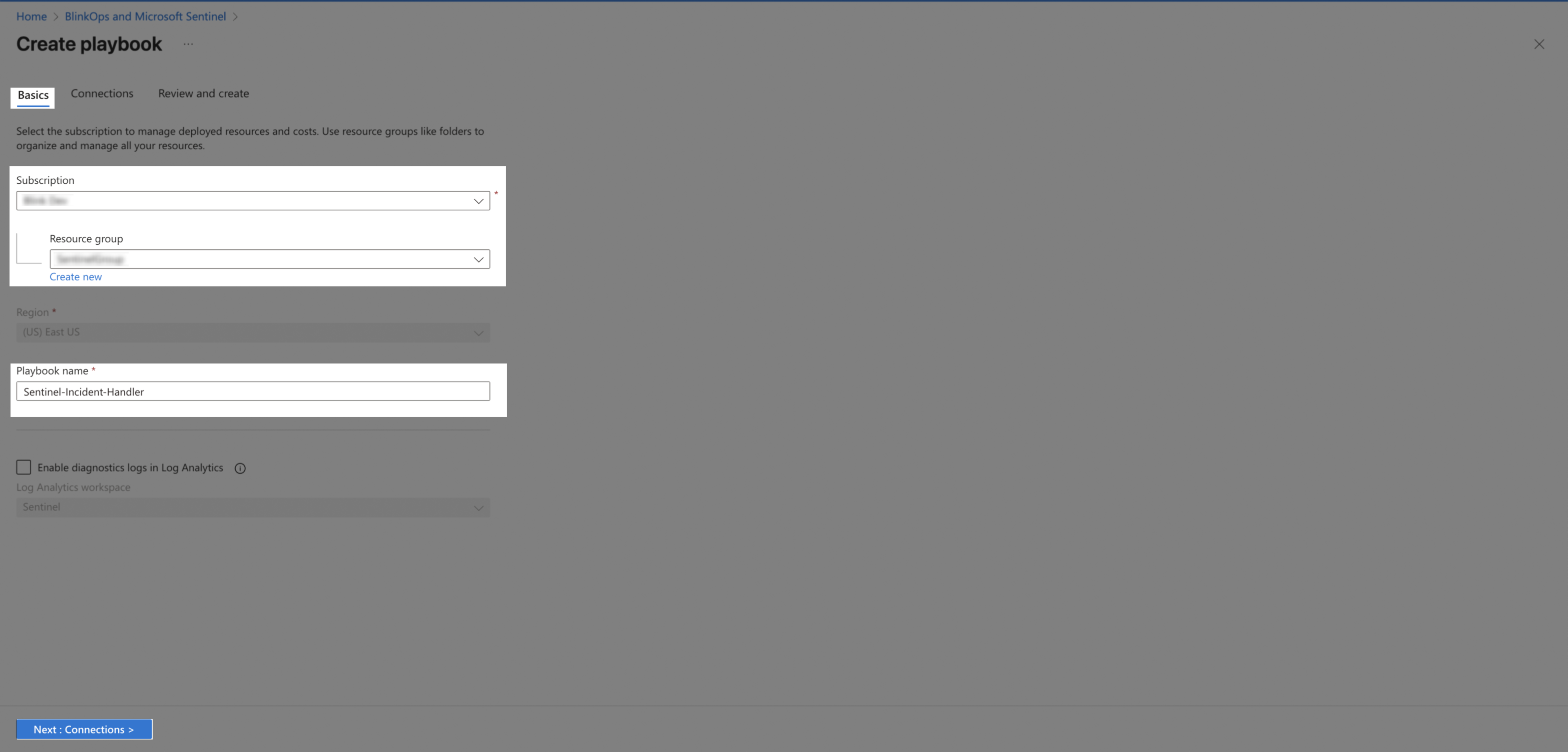
-
Choose a Microsoft Sentinel connection. Click Next: Review and create.
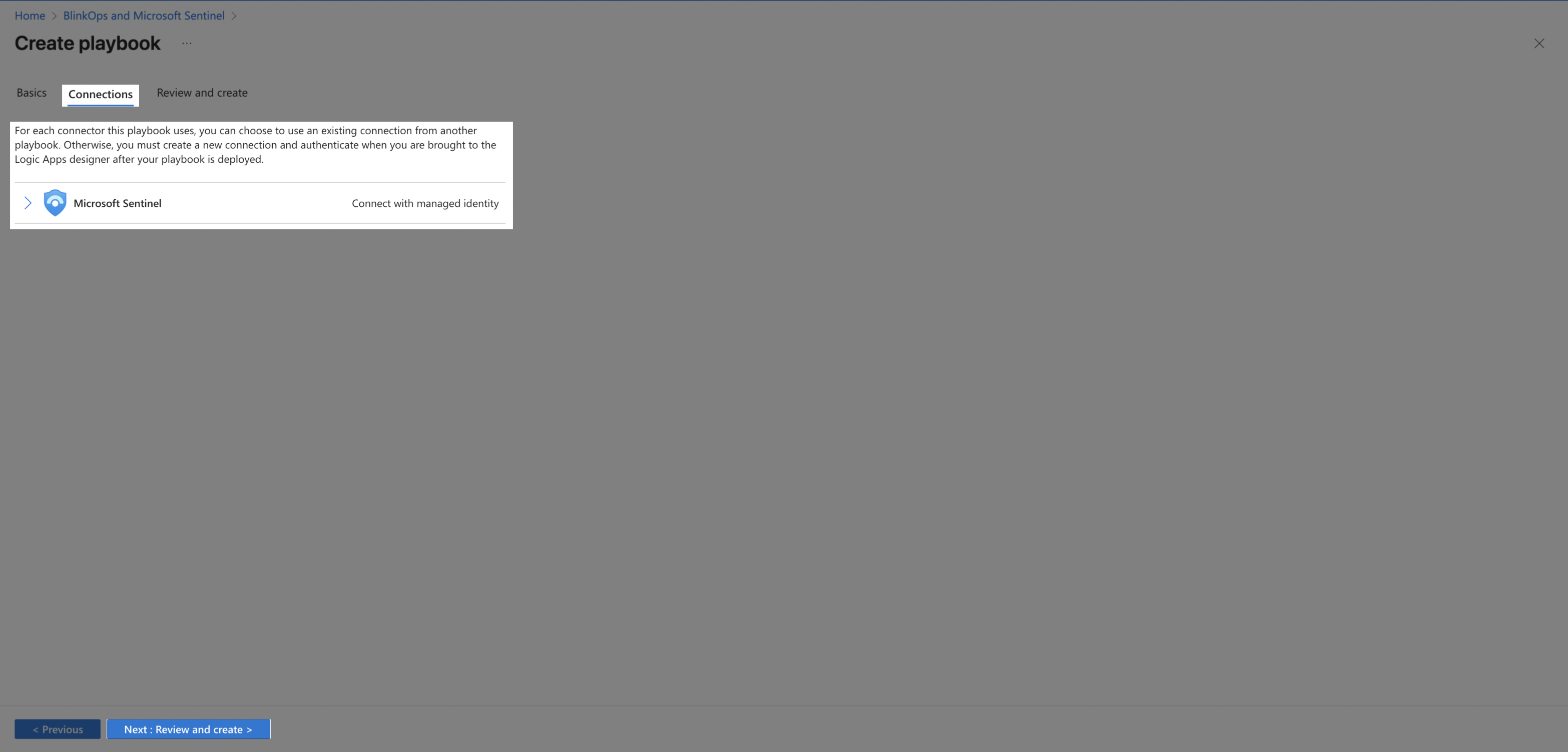
-
Click Create playbook.

-
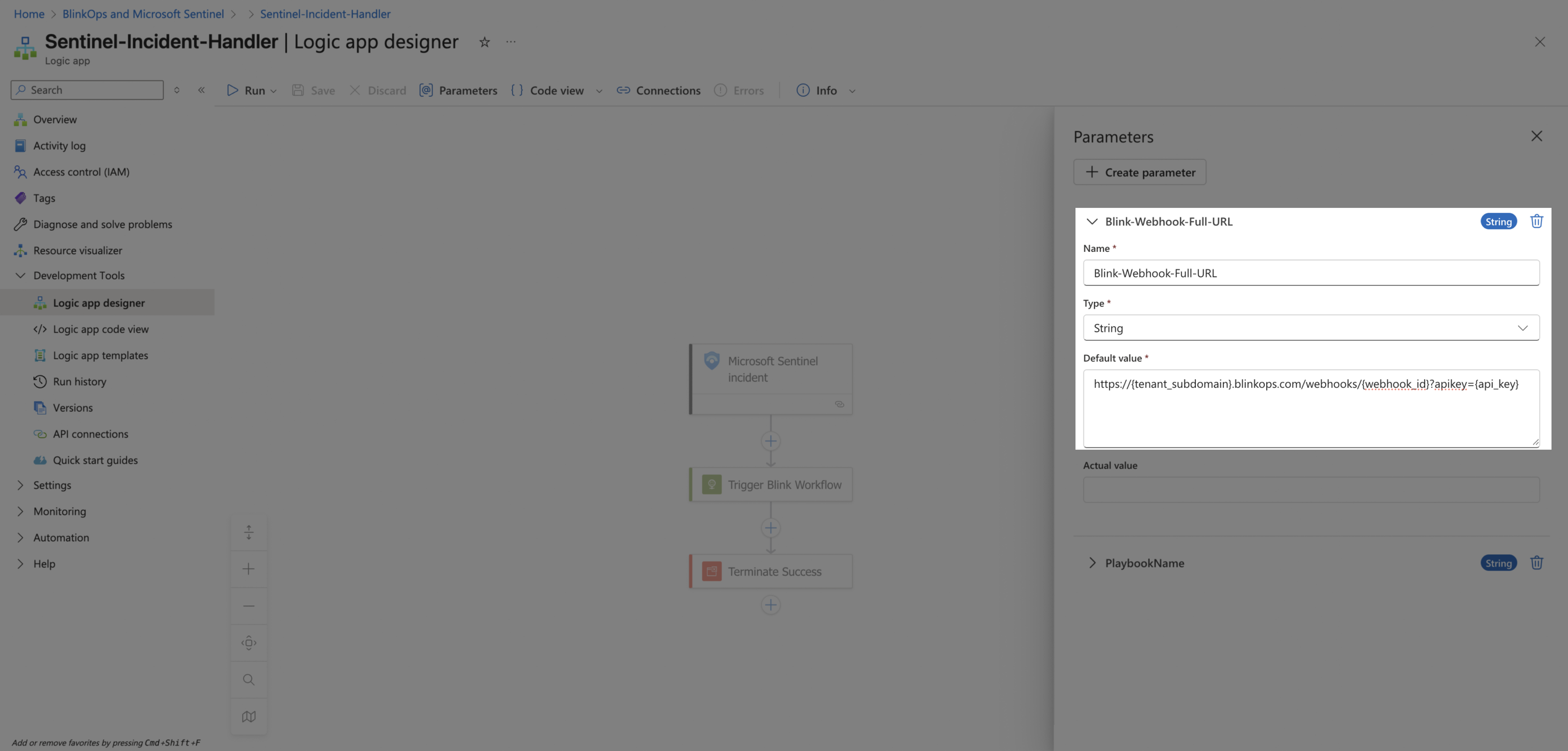
In the playbook designer, click Parameters.
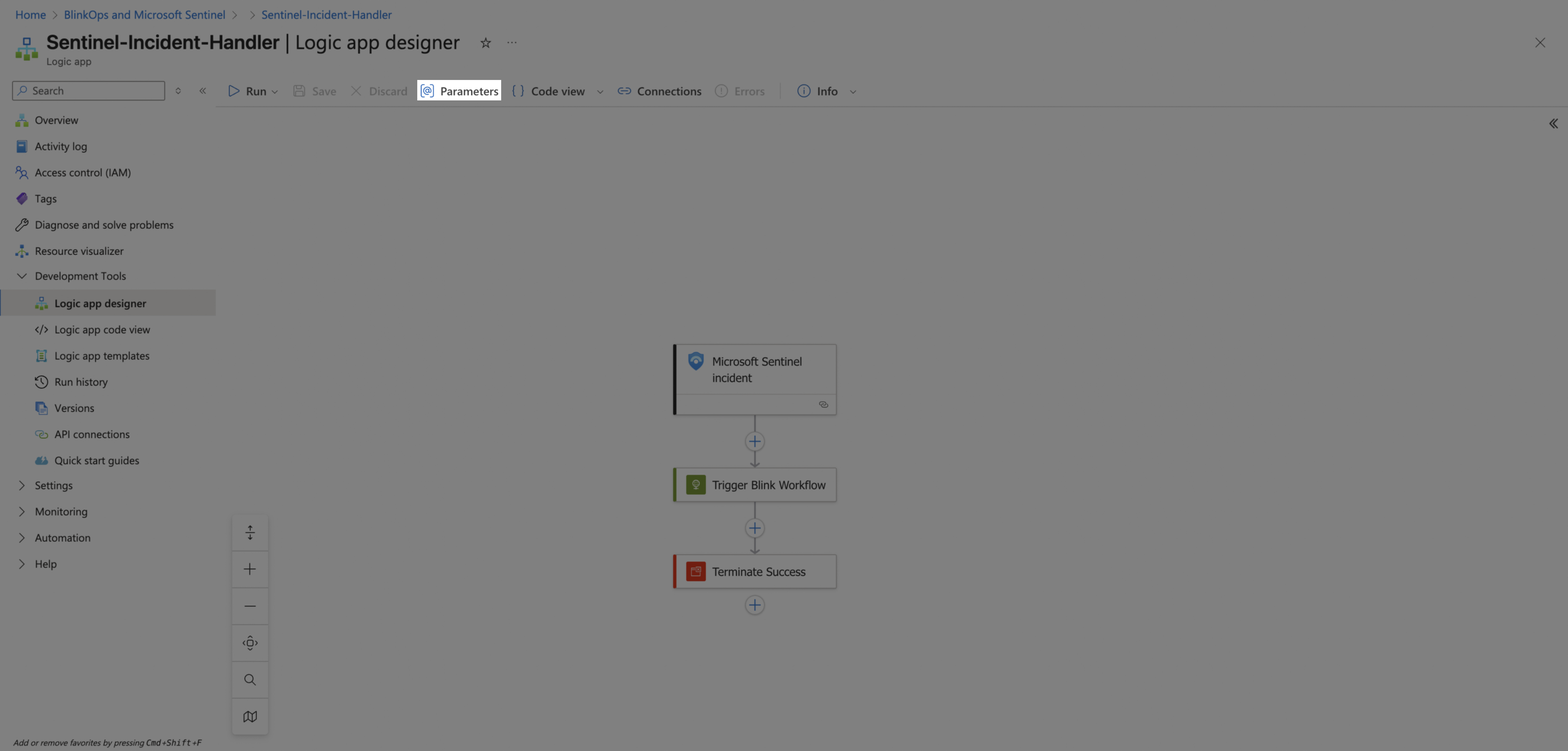
-
Configure the Blink-Webhook-Full-URL parameter. Change the Default value to the Webhook Full URL you copied earlier from Blink.
-
Close the parameters configuration window and Click Save.
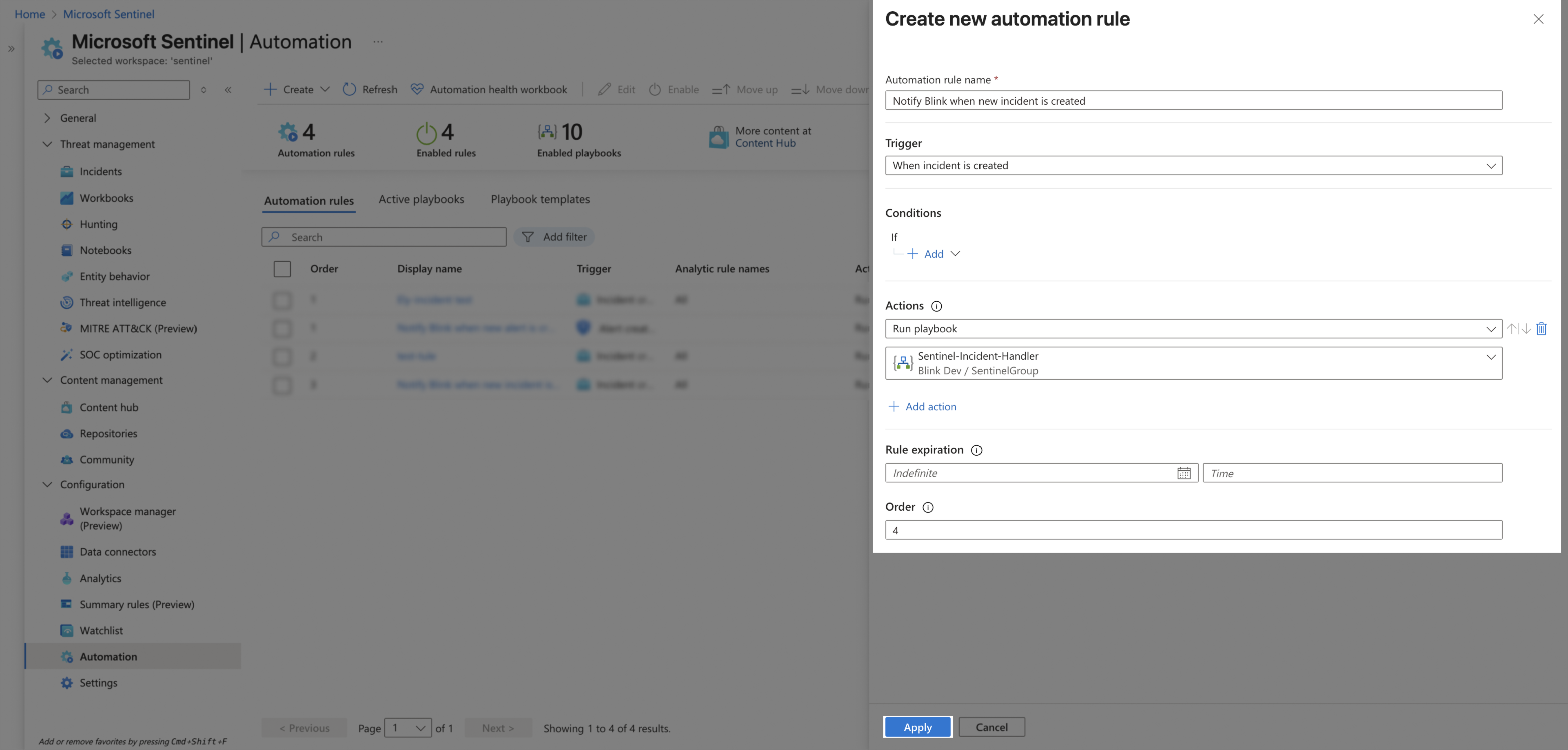
Create an Automation Rule
Next, we will create an automation rule that will trigger the workflow whenever an incident is created. Keep in mind that you can also create rules for new alerts.
-
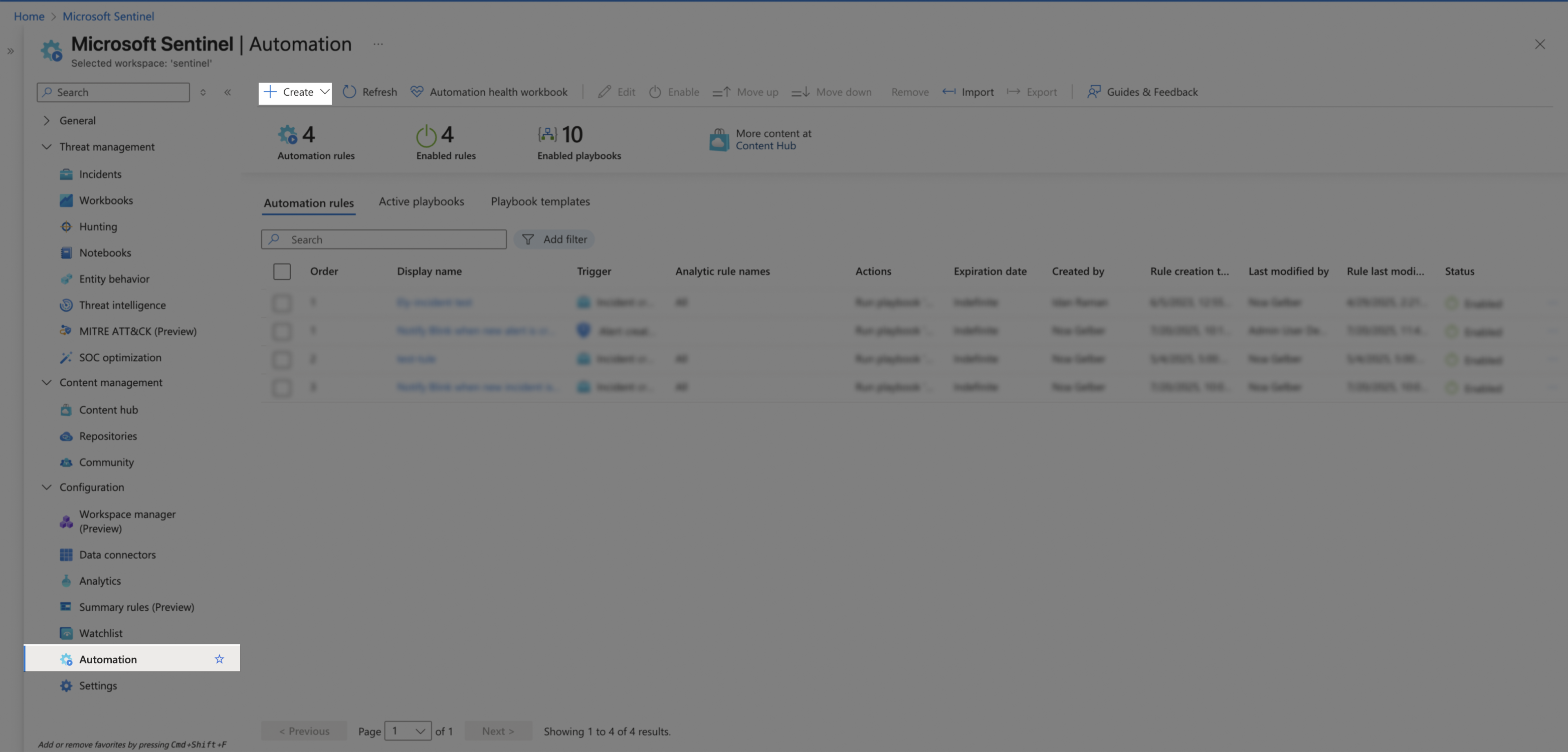
In Microsoft Sentinel, use the left-hand menu to go to Configuration > Automation. Click Create > Automation Rule.
-
Configure the new rule:
- Choose an informative rule name.
- Choose the trigger type When incident is created (Other available options:
When incident is updated/When alert is created).
If you’re configuring an 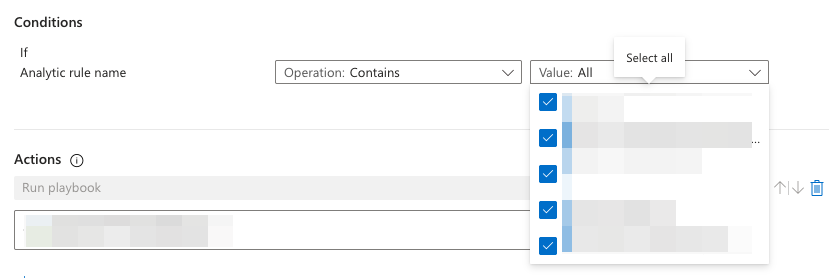
Alert Rule, make sure to check the specific Analytics rule name that will trigger the playbook under the Conditions section (or select all of them).
- Set Actions to
Run playbook, and select the sentinel incident handler playbook. - Optional: set rule expiration date.
- Click Apply.
After completing all the steps, Microsoft Sentinel incidents will automatically trigger your workflow in Blink.