Creating an Microsoft Entra ID connection
Use one of the following methods to make a connection:Using OAuth
This method will not work if your Azure User Type is Guest.Creating your connection
- In the Blink platform, navigate to the Connections page > Add connection. A New Connection dialog box opens displaying icons of external service providers available.
- Select the Azure Active Directory icon. A dialog box with name of the connection and connection methods appear.
- (Optional) Edit the name of the connection. At a later stage you cannot edit the name.
- Click Microsoft Entra ID to authenticate using OAuth.
- Sign in using your credentials.
Need admin approval? please refer to the Need Admin
Approval guide.
Using App Registration
To create the connection you need:- A client ID
- A client secret
- A tenant ID
Obtaining the credentials
- Log into the Azure Portal.
-
Go to the Microsoft Entra ID resource.
-
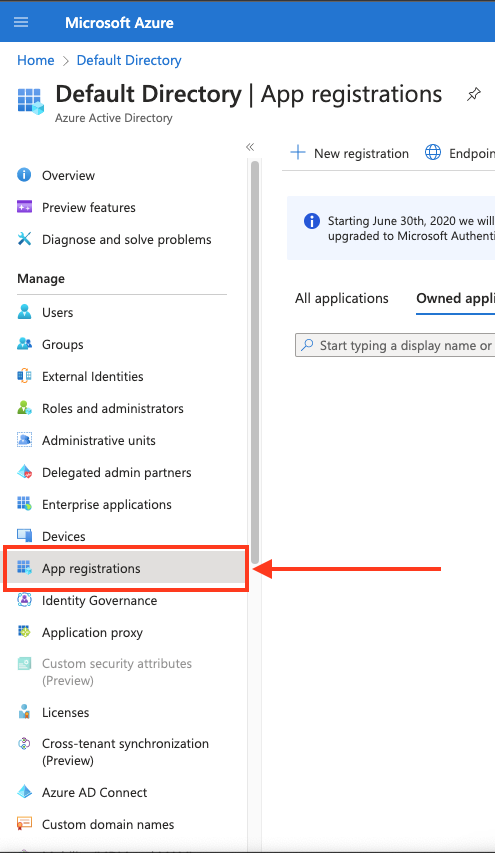
In the left-hand menu, click App registrations.
-
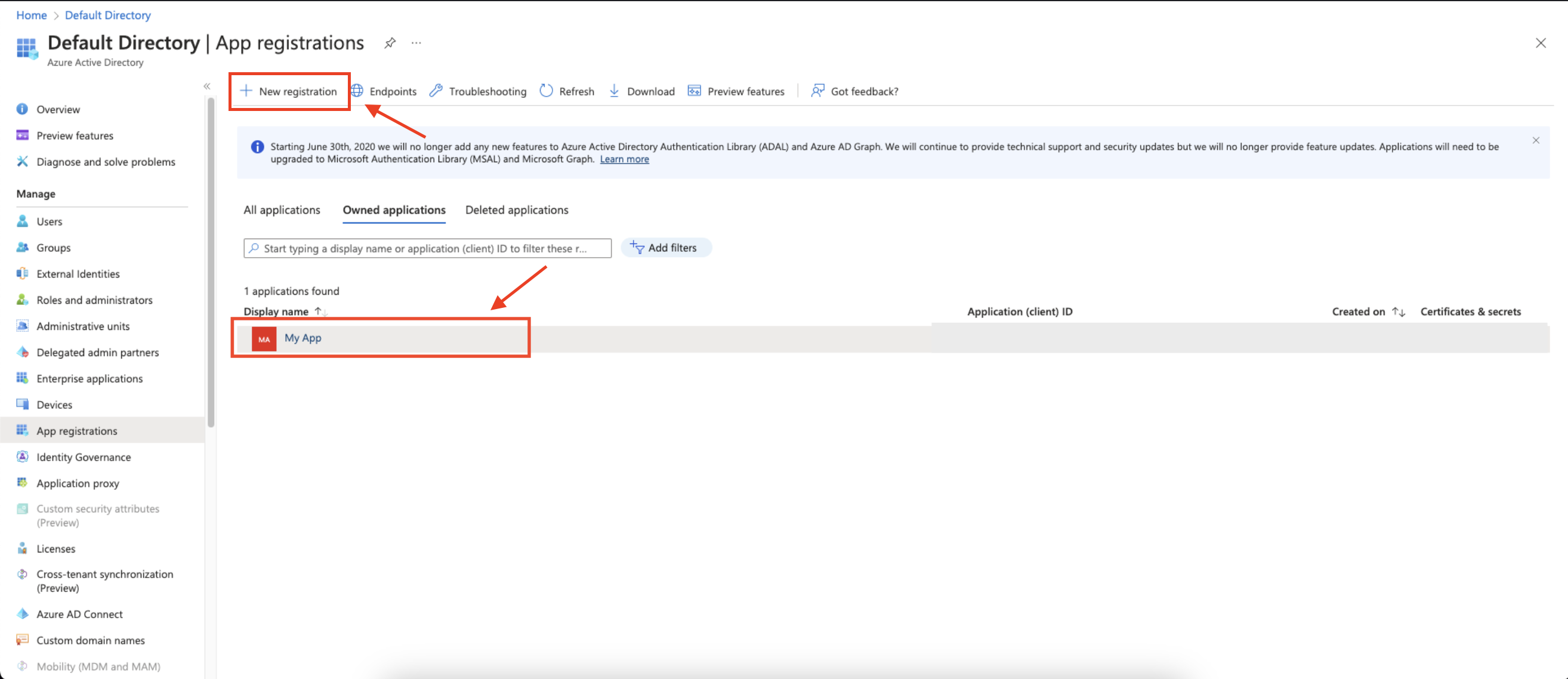
Create a new application registration or click on one of your existing applications.
-
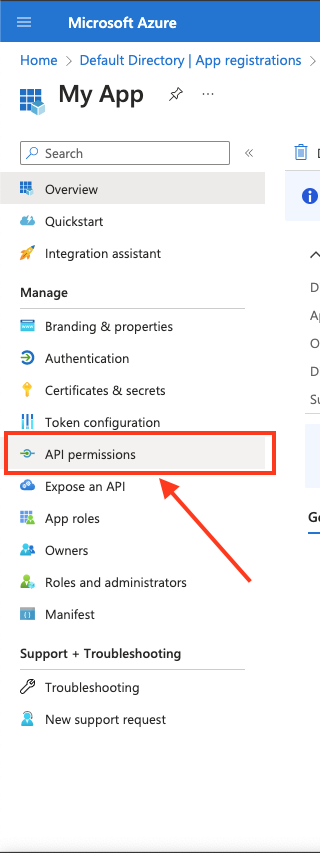
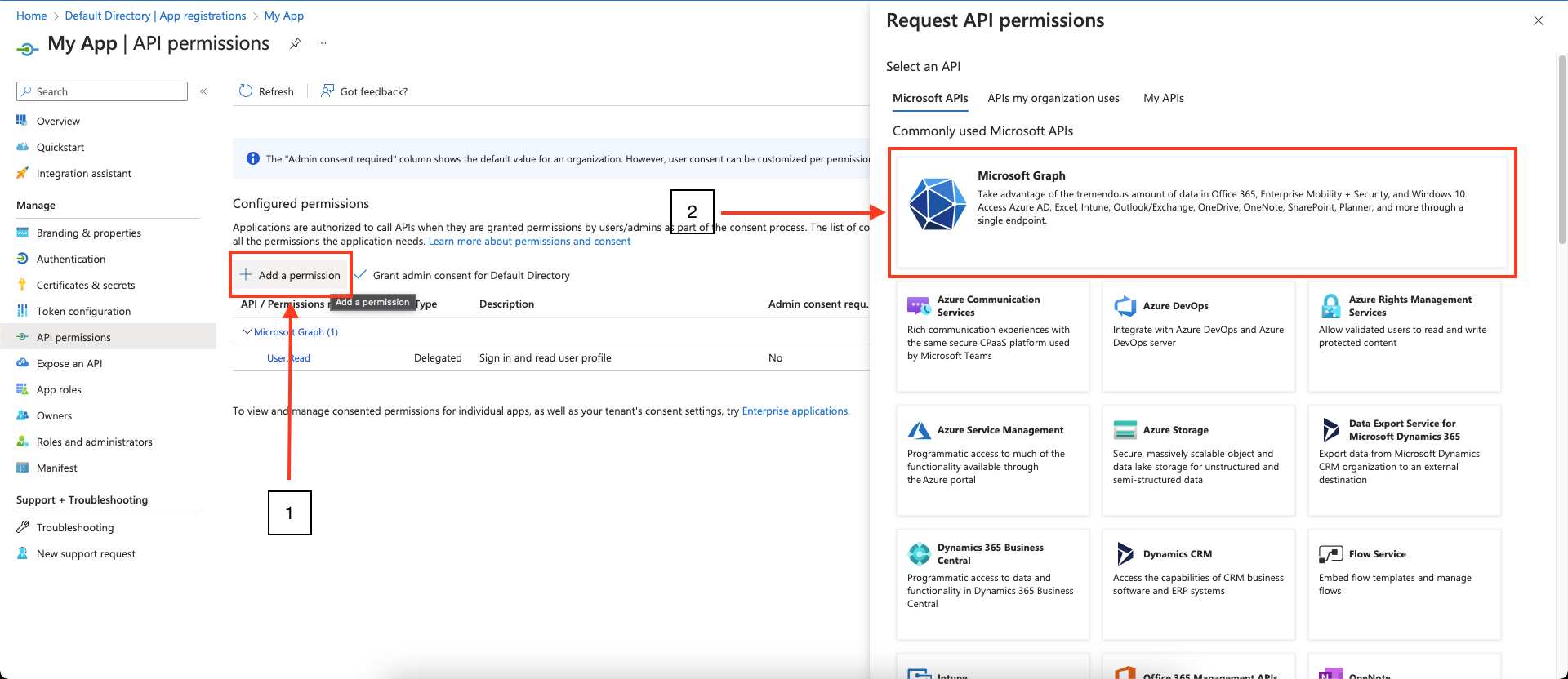
In the left-hand menu, click API permissions.
-
Click Add a permission and select Microsoft Graph.
-
Choose Application permissions and mark the permissions you wish to add.
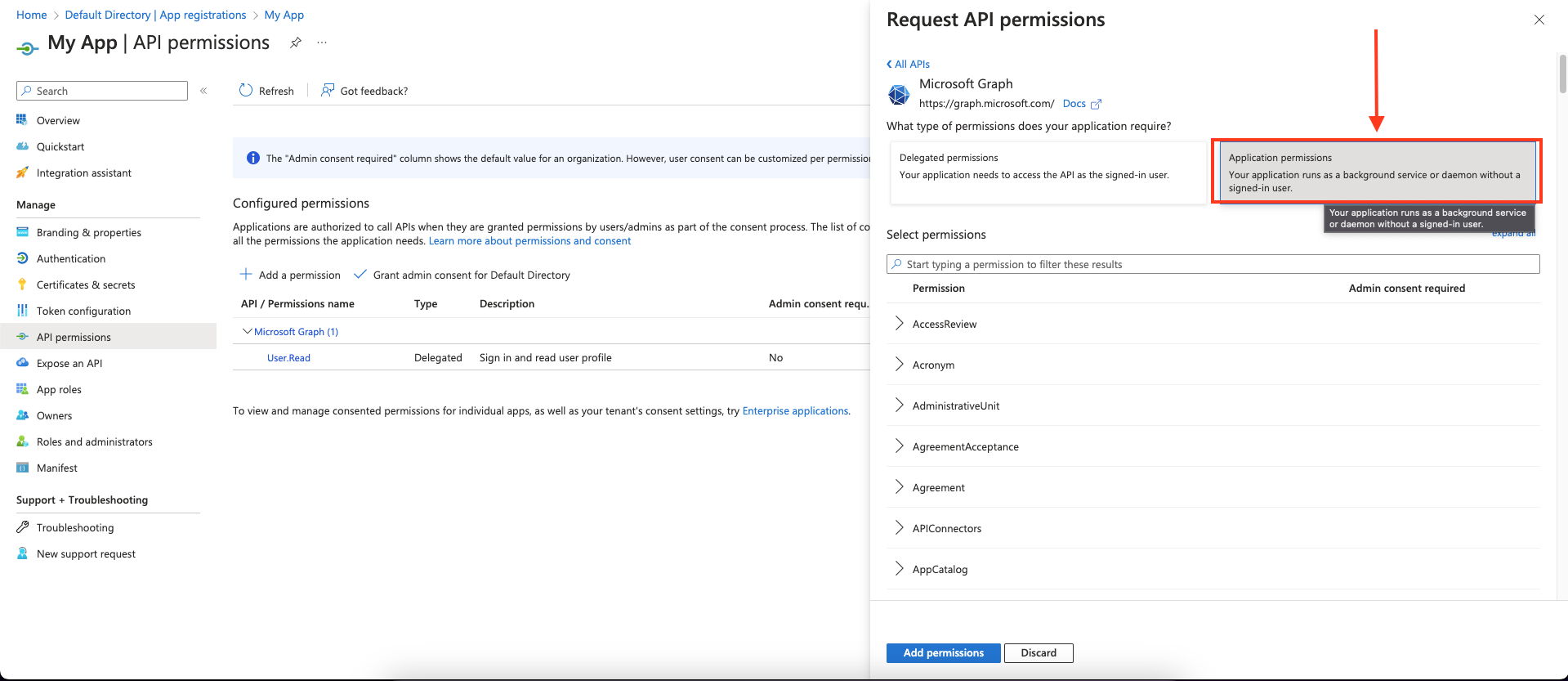
As a best practice, request the least privileged permissions that your app
needs in order to access data and function correctly. Requesting permissions
with more than the necessary privileges is poor security practice, which may
cause users to refrain from consenting and affect your app’s usage. For
additional information, refer to Microsoft Graph
permissions.
| Least privileged permissions | Higher privileged permissions |
|---|---|
| GroupMember.ReadWrite.All | Directory.AccessAsUser.All |
| IdentityRiskyUser.ReadWrite.All | Directory.ReadWrite.All |
| Group.Create | Group.ReadWrite.All |
| User.ReadWrite.All | User.ReadWrite.All |
| Group.ReadWrite.All | Directory.Read.All |
| User.Read.All | SecurityAlert.ReadWrite.All |
| SecurityAlert.Read.All | GroupMember.ReadWrite.All |
| GroupMember.Read.All | Group.Read.All |
| LicenseAssignment.ReadWrite.All | User.EnableDisableAccount.All |
| User.ManageIdentities.All | |
| Directory.Read.All |
- Click Add permissions to save the changes.
-
Click Grant admin consent for
<your tenant>on the API permissions page. Only admins can grant consent.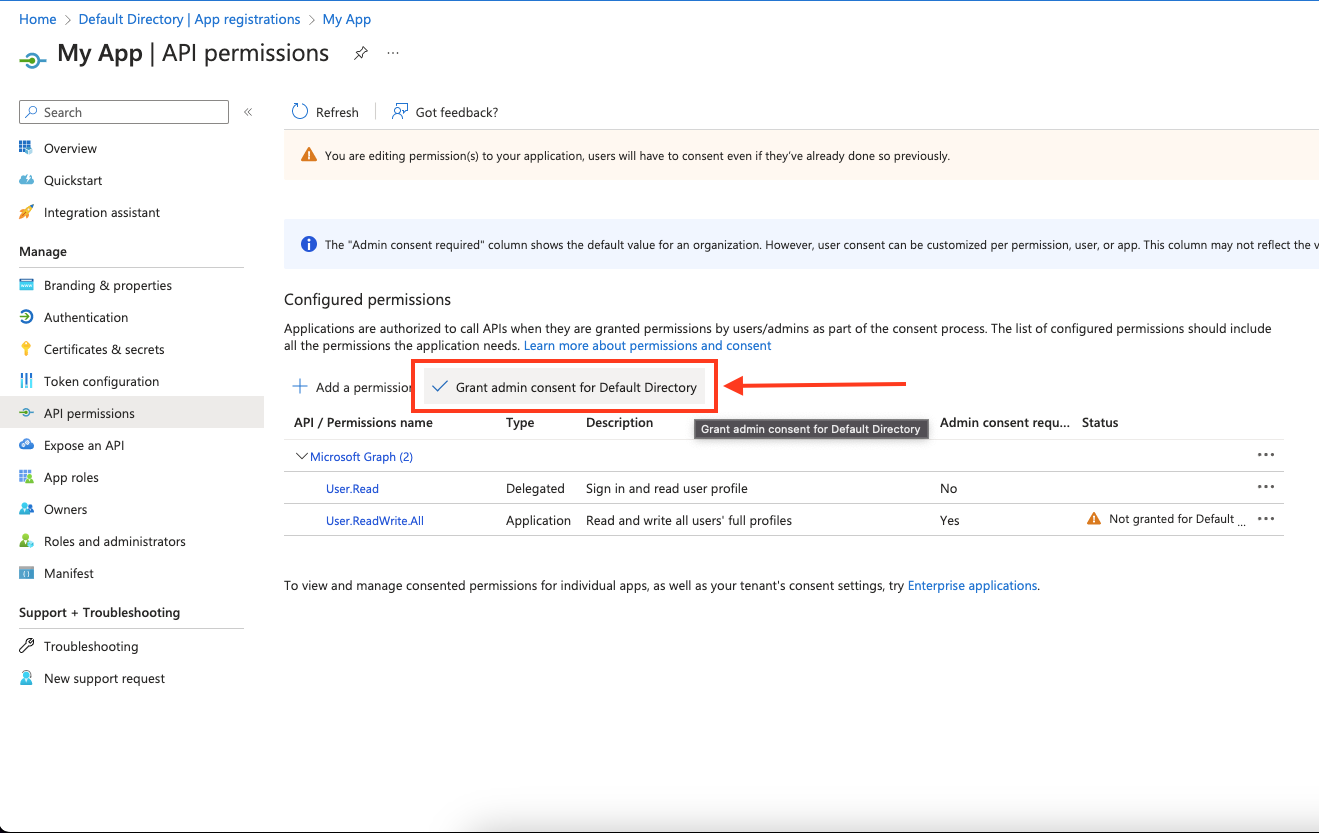
-
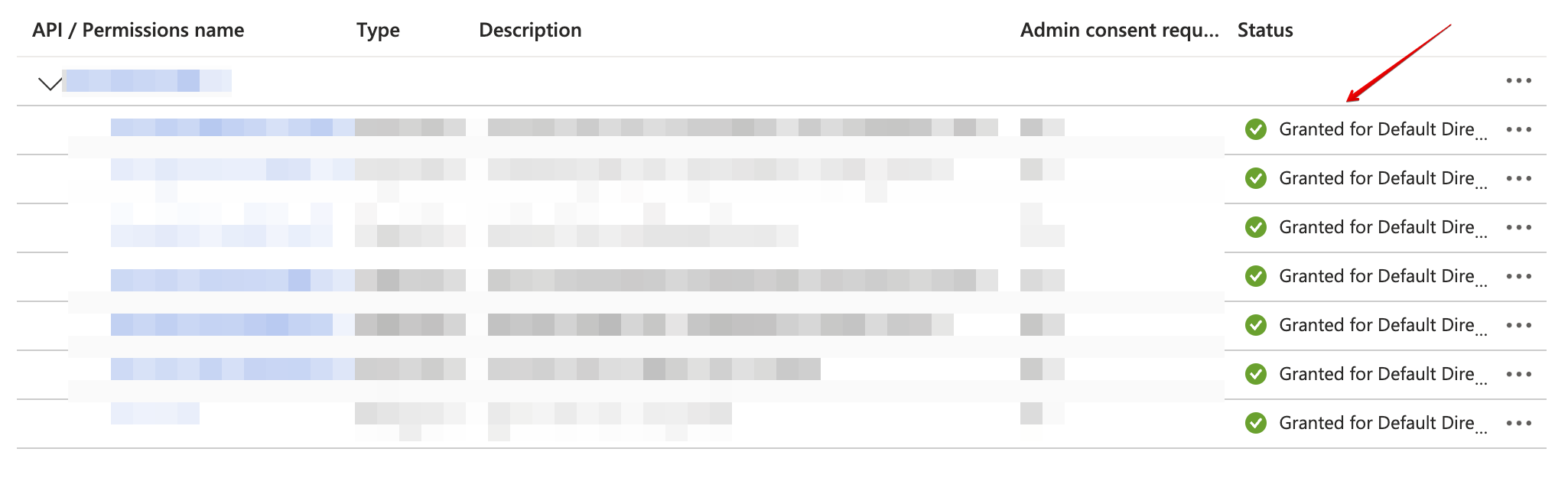
Confirm that the added permissions are now verified.
-
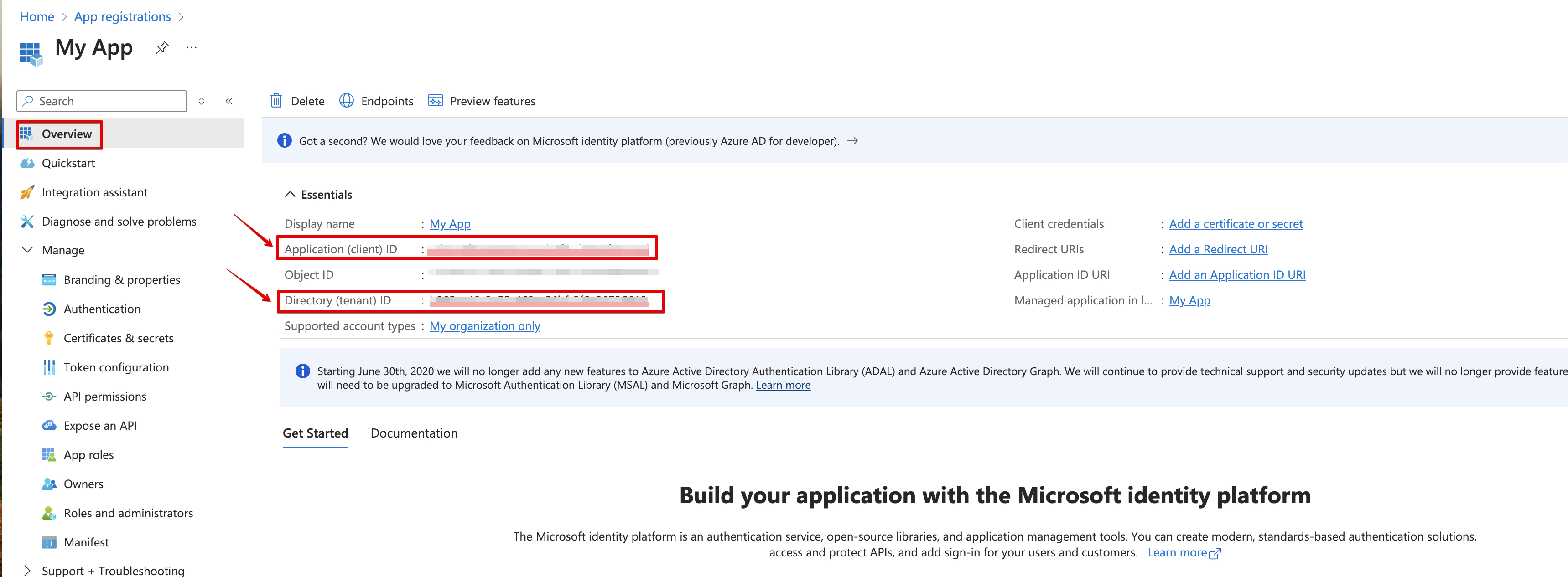
Navigate to Overview and Copy your client ID and tenant ID.
-
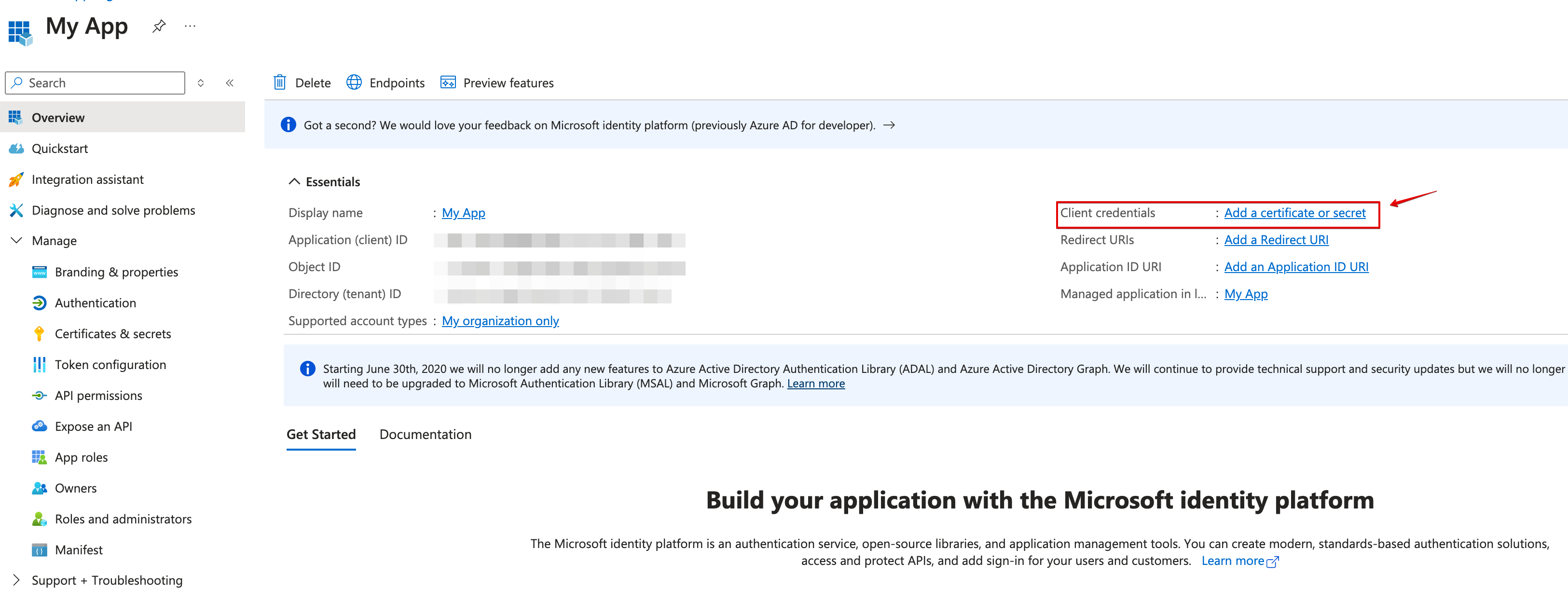
Create a new client secret.
-
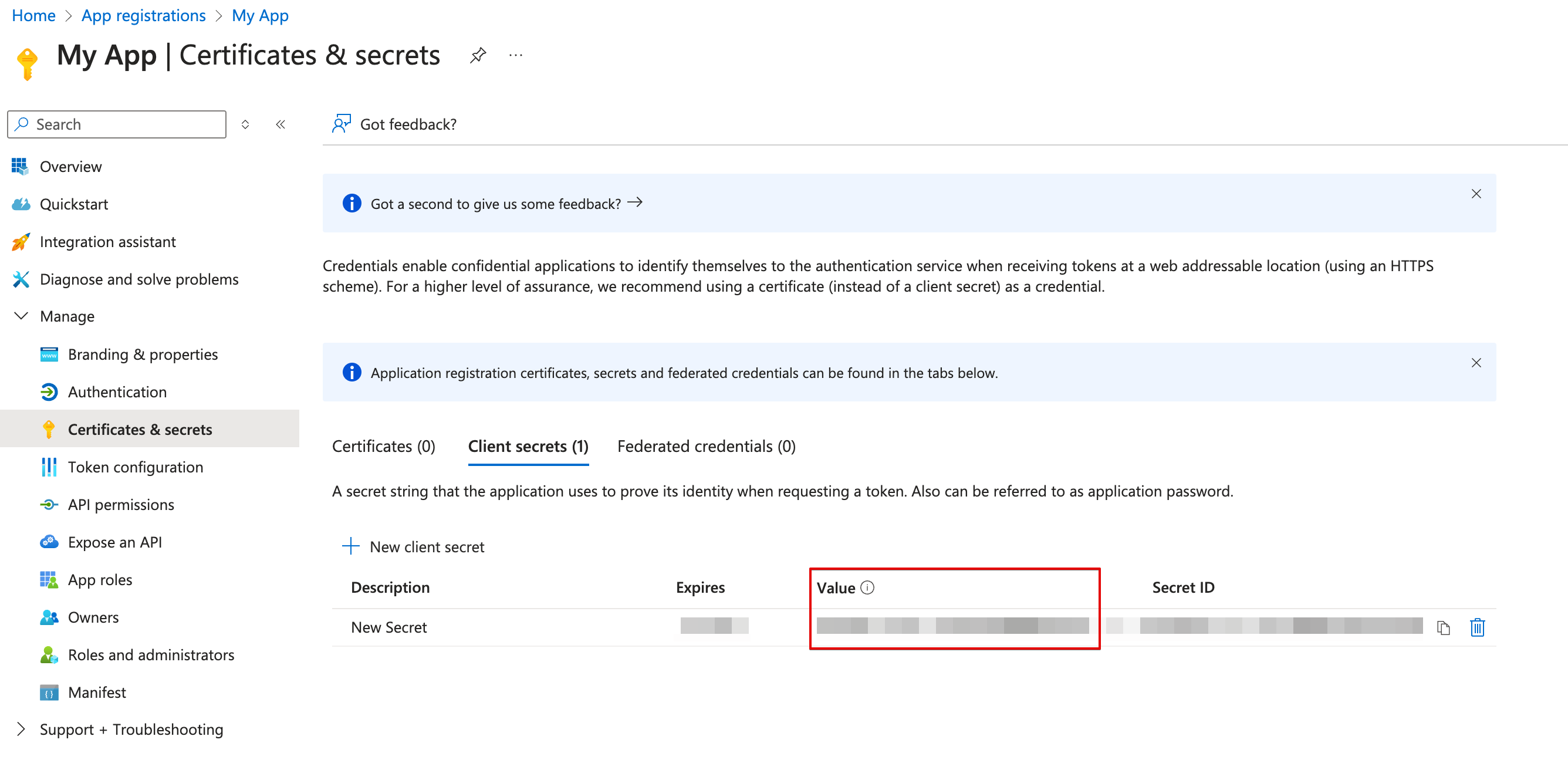
Copy the secret value.
Creating your connection
- In the Blink platform, navigate to the Connections page > Add connection. A New Connection dialog box opens displaying icons of external service providers available.
- Select the Microsoft Entra ID icon. A dialog box with name of the connection and connection methods appear.
- (Optional) Edit the name of the connection. At a later stage you cannot edit the name.
- Select App Registration as the method to create the connection.
-
Fill in the parameters:
- The client ID
- The client secret
- The tenant ID
- (Optional) Click Test Connection to test it.
- Click Create connection. The new connection appears on the Connections page.
Using LDAP
Microsoft Entra ID supports administration using the LDAP protocol, allowing you to manage your workspace using Blink’s LDAP actions instead of the Microsoft Entra ID integration. In order to expose your Microsoft Entra ID workspace as an LDAP server, follow these steps:- Set up an Microsoft Entra ID Domain Services managed domain.
- Access the domain controller’s virtual subnet.
- If your runner is running on premises and connected to the Azure virtual subnet, your LDAP server URL is the domain controller’s IP address.
- Otherwise, in order to use an external runner, you need to add a public IP to the virtual subnet and assign it to your domain controller.
-
To create an LDAP connection to this server:
- Use the IP address accessible to the runner as your URI, with
ldap://protocol, orldaps://if you enabled “Secure LDAP” - Acquire the Distinguished Name of a Microsoft Entra ID user who has permissions to the server. You can use dsquery on a connected Windows Server to obtain the full name of a user.
- Use the password of the specified user. After activating your domain controller, the user should reset their password so that it is properly synced.
- Use the IP address accessible to the runner as your URI, with